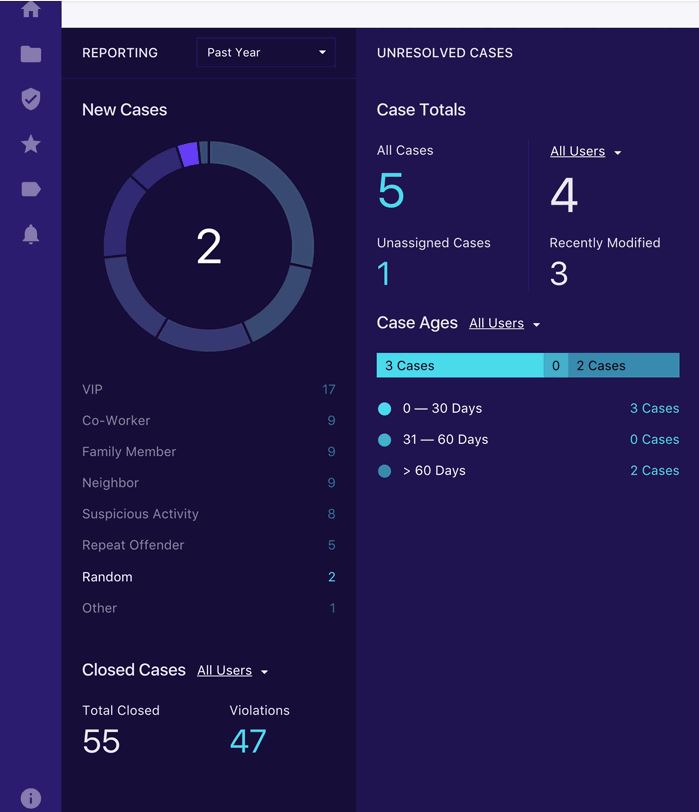
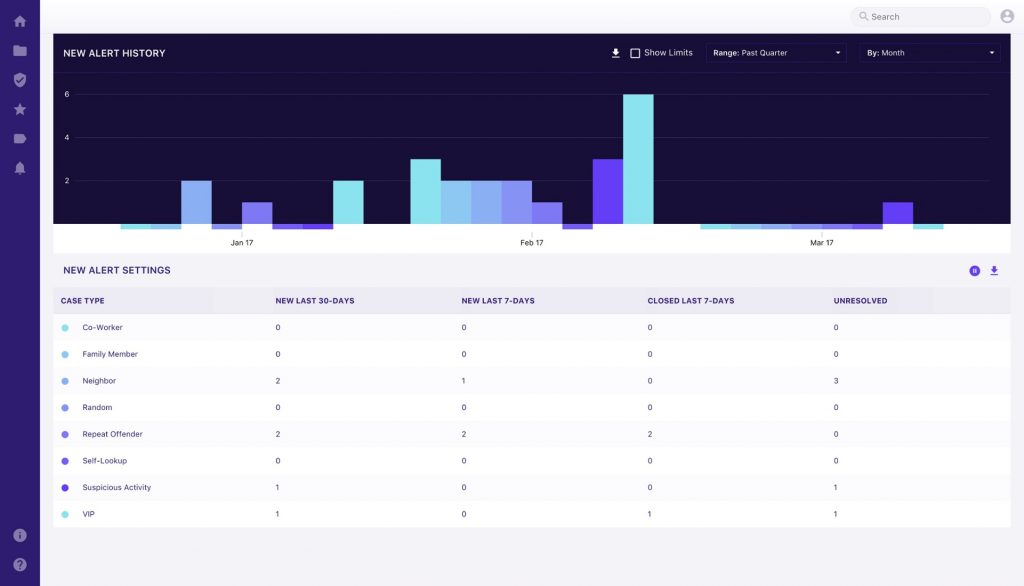
Protenus – Protecting Patient Privacy in Electronic Health Records
- Most company co-founders that I talk to met either in engineering school or in business school. You and your co-founder Nick Culbertson met in medical school. Did you finish medical school? Did you ever practice as a doctor?
- How/why did you start Protenus?
- Please give me an overview of Protenus.
- Why do we need a product specifically for healthcare, instead of just leveraging existing security and collaboration products?
- Who do you see as your main competitors? How are you different from them?
- How do you define your market? Is there a specific target audience within that market?
- How do you normally attract and engage with new customers?
- How many active customers do you have today? Where are they mainly located?
- Who are some of your biggest customers?
- What are your top three privacy protection tips?
- How do you see the medical health records software market evolving in the next few years?
- What are your future plans for Protenus?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Do we really need yet another enterprise threat detection system? If you are in the healthcare field, the answer is a resounding yes! In this interview, Protenus co-founder and President Robert Lord outlines very clearly how the security and privacy needs of electronic health records are very different from traditional enterprise security issues. Moreover, the privacy and security challenges facing the world of healthcare are very different – and difficult to address – as well.
Robert also shares with us his top privacy protection tips and his thoughts on the future of medical health records software – including why healthcare security and privacy should become the paradigm for other industries to imitate.
Most company co-founders that I talk to met either in engineering school or in business school. You and your co-founder Nick Culbertson met in medical school. Did you finish medical school? Did you ever practice as a doctor?
Yes, Nick and I met in medical school, but we both left half way through, and we therefore never practiced as physicians.
How/why did you start Protenus?
We founded Protenus with the goal of gaining a better understanding of the state of electronic health records (EHR). What we discovered was that a tremendous amount of money was being spent rolling out EHR systems, but that very little effort and money was being spent on security and privacy for those systems.
We saw a huge need and opportunity to address this problem. The great challenge was to figure out what was the appropriate behavior for every different person/role with access to the EHR system.
Please give me an overview of Protenus.
Protenus is a health data analytics platform specifically designed to understand the clinical workflows within in the complex clinical environment of a healthcare organization. This technology helps hospitals accurately detect the obvious and often hidden threats to patient data. Its main functions are to:
- Detect and prevent data breaches in healthcare records.
- Detect inappropriate activity and raise alarms to handle it.
- Visualize activity in real-time enabling security staff to rapidly see suspect events and respond to them.
Why do we need a product specifically for healthcare, instead of just leveraging existing security and collaboration products?
We actually asked ourselves that exact question when we were first getting started. However, we quickly learned that there are many unique issues and challenges in the healthcare security and privacy space.
For starters, the security challenges facing EHR systems are different from traditional IT security issues. We have identified and addressed the following threat scenarios, which are unique to EHRs:
- VIPs and public figures
- Friends, family, and other snooping
- Criminal insiders
- Phishing attacks
- Contractors, affiliates, and business partners
- Lost or stolen devices
In addition, hospital workflows are extremely complex and it is very hard to determine access rights a priori. Moreover, healthcare defaults to open access for all healthcare workers, so that they can handle any/all emergencies. That means that if you have any level of access, you essentially have complete access. Role-based methods do not work very well in this environment. Every doctor or nurse is different. You really need to understand the clinical and administrative context.
Who do you see as your main competitors? How are you different from them?
Several legacy systems try to address this space, but they are not well suited to the modern healthcare environment. Their integration with existing EHR systems is very difficult and they tend to produce many false positive warnings. In addition, those systems do not have as much deep information as we do, which makes it difficult for the security team to decide how to react.
One of the key differentiators of our system is that it is behavior-based. We are not trying to identify “bad guys.” Instead, we figure out what is normal behavior for each individual and report on anything that deviates from that. We make extensive use of big data, analytics, and machine learning. We track what each individual is doing in the HER systems on a second-by-second basis over long periods of time. We also utilize multi-dimensional behavior fingerprints in order to characterize each user.
That is not to say, however, that it takes a long time for our system to get up to speed. The Protenus system is effective from the first day you install it. It is able to analyze existing records, logs, and human resources information to get started.
How do you define your market? Is there a specific target audience within that market?
Our target market is any organization maintaining healthcare data, but here are a few of the main specific categories:
- Hospitals
- Health systems
- Health Information Exchanges (HIEs)
- Insurance companies
How do you normally attract and engage with new customers?
We are recognized as the leading privacy analytics provider in this space. We are also recognized as thought leaders since we are creating new ways of thinking about this problem. This results in many potential clients approaching us to begin a discussion.
In terms of our proactive efforts to engage with potential customers, we have your typical enterprise software sales and marketing efforts and also attend many industry conferences.
How many active customers do you have today? Where are they mainly located?
I cannot discuss specific numbers, but we have clients located throughout North America.
Who are some of your biggest customers?
Our system is deployed at the Johns Hopkins Health System and other similar top-tier health institutions.
What are your top three privacy protection tips?
I will actually give you four…
- You need to have the support for privacy and security at the highest level of the organization.
- Given the large attack surface and huge amounts of data, manual methods will not work – you must look to deploy big data and artificial intelligence solutions.
- You must actively engage the workforce, including culture, priorities, education, and incentives/consequences.
- You must re-orient your mindset – it is not enough to be just concerned about compliance, you must be concerned about being able to trust the EHR system.
How do you see the medical health records software market evolving in the next few years?
I can only address the privacy and security aspects of the EHR market.
- I see us turning a corner – I am witnessing increasingly more support from top management. We need to see more spending from government and large organizations.
- An organization’s trust posture and position will become a strategic asset.
- Healthcare security and privacy should become a paradigm for other industries, since the data in this industry is so massive and so sensitive.
What are your future plans for Protenus?
- Continue growing the business, message, and vision.
- Continue educating the market.
- Investigating and embracing opportunities for novel approaches in this space.
- Extending into additional areas of healthcare analytics.
How many employees do you have today? Where are they located?
We now have 30 employees and they are mainly located in the Baltimore, Maryland area.
How many hours a day do you normally work? What do you like to do when you are not working?
I generally try to keep it to a reasonable average of 12 hours per day. I feel that I need to set the example of work-life balance for the rest of team. Although I try to keep up with emerging technologies and trends in areas such as big data, AI (Artificial Intelligence), and healthcare, even outside of my formal working hours.
During my leisure time, I enjoy engaging in physical activities at the gym, while on the opposite end of the spectrum, I relish exploring new dining establishments. Additionally, I make an effort to embark on captivating journeys to enrich my travel experiences.