Arxan – Protecting Your Applications at Every Level
- Please tell me a little bit about yourself and your background.
- What do you think are the biggest security challenges companies face today?
- Arxan is in the category of security companies that assume security breaches will occur, and therefore application protection is required. Please explain that to me.
- Your web site talks about products, solutions, and technologies. How do I mix and match, or navigate, that to figure out what I need? Are all of the technologies included in all of the products?
- Products
- Solutions
- Technologies
- Which of your product areas is currently the most popular? Which is the fastest growing?
- What does it take to incorporate your products into an existing software development environment?
- How does your pricing model work?
- You also offer professional services. What percentage of your customers takes advantage of that? What percentage of your revenue comes from that?
- How do you define your target market?
- How many active customers do you have today? Where are they mainly located?
- How would you describe your current typical customer?
- Whom do you see as your main competitors?
- How do you see the security software evolving in the next few years?
- I recently interviewed Mark Lorion, the President and General Manager of Apperian, which Arxan acquired at the beginning of this year. Is that acquisition a major part of your growth strategy? How does Apperian complement your existing products?
- What are some of Arxan’s future plans?
- How many hours a day do you normally work? What do you like to do when you are not working?
Despite all of the technologies and efforts invested in protecting an organization’s network, the reality is that there will ultimately be some malware or hacker that breaches the security of the network. When (not if) that occurs, how vulnerable are your applications and the data they process?
In my interview with Rusty Carter, Vice President of Product at Arxan, we discuss how Arxan provides very deep protection - down to the binary code level – for desktop, web, and mobile applications. Rusty also shares with me what are the fastest growing markets for his application protection products as well as his view on where the industry as a whole is headed.
Please tell me a little bit about yourself and your background.
I have spent my entire professional career in the areas of high-tech and security. I have a long history as a product manager, at both large and small companies. I am really quite passionate about it.
What do you think are the biggest security challenges companies face today?
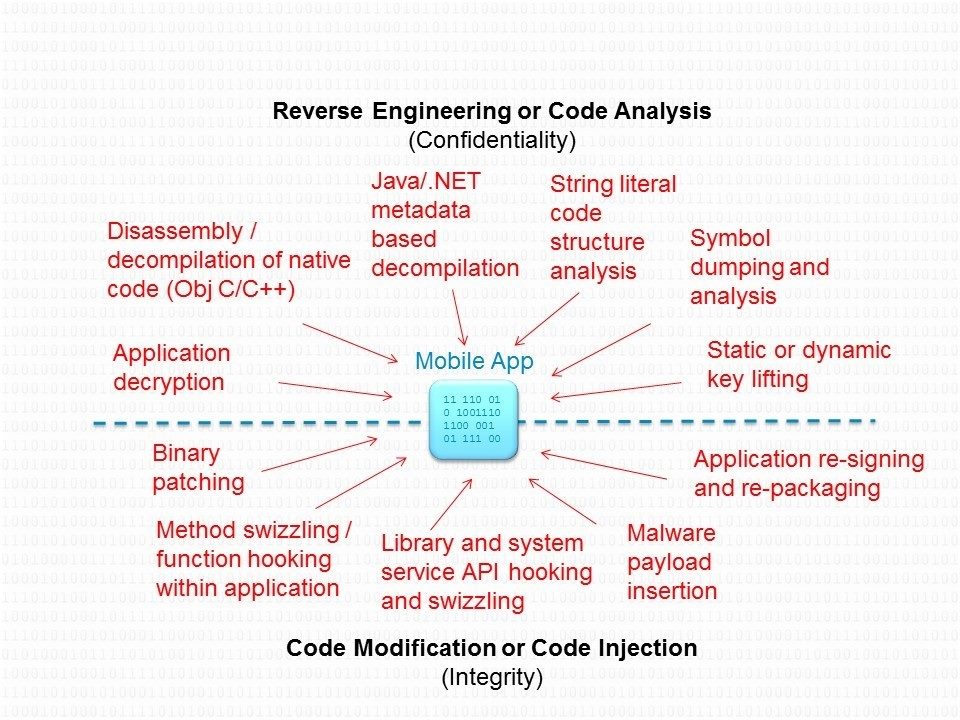
Cyber security has traditionally focused on protecting the company’s network and detecting threats at the perimeter. Today, however, the situation is different. Most threats today actually start on phones and other mobile devices.
The sophistication of attacks is getting more advanced and attackers now take advantage of the fact that there is currently limited monitoring, and almost no visibility, at the endpoint. They are also getting more sophisticated in their ability to reverse-engineer and tamper with applications.
As a result, companies are starting to realize that security must start at the application level.
Arxan is in the category of security companies that assume security breaches will occur, and therefore application protection is required. Please explain that to me.
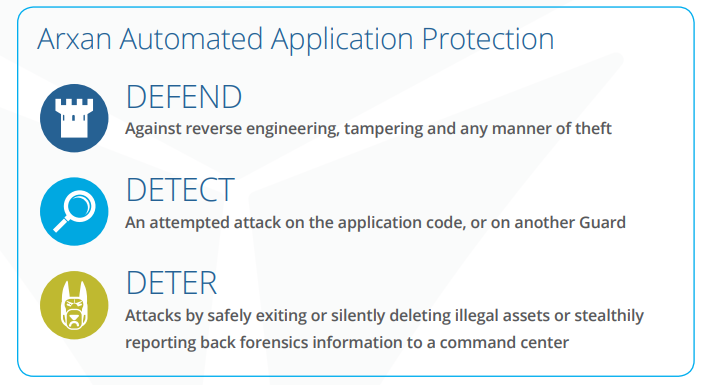
Despite the best efforts of enterprises and security solution providers to keep the network safe and to stop all threats at the perimeter, that is just not enough. Of course, we must continue with these efforts to protect the perimeter, but we also need to assume that they WILL be breached. Therefore, Arxan offers technologies to protect your applications on the inside of the network perimeter (or wherever else they may be running).
The technologies that we offer protect applications all the way down to the binary level. The less sophisticated attacks try to get to an application’s source code, while more sophisticated attacked will look at the binary in memory. Our technologies protect applications all the way from the binary image in memory, to the application running on an endpoint, up through the data center.
Your web site talks about products, solutions, and technologies. How do I mix and match, or navigate, that to figure out what I need? Are all of the technologies included in all of the products?
Here is how we organize things:
Products – Centered on specific platforms and the technologies that they support.
Solutions – Span platform technologies and get into the application details.
Technologies – Are included in one or more products.
I think it will be clearer if I list the offering in each category:
Products
- Application Protection for Mobile
- Application Protection for IoT and Embedded
- Application Protection for Desktop
- Application Protection for Server
- Application Protection for JavaScript
- Professional Services
Solutions
- Mobile Payments and Bankin
- Automotive IoT
- Healthcare IoT
- API Protection
- Gaming
- Digital Media
- High-Tech
Technologies
- API Protection
- Cryptographic Key Protection
- Mobile SDKs and WDKs
- Obfuscation
- Runtime Application Self-Protection (RASP)
- White-Box Cryptography
Which of your product areas is currently the most popular? Which is the fastest growing?
Historically, the most popular product was desktop application protection. We originally started with gaming companies who wanted to protect their intellectual property and with media companies that needed to protect their encryption keys.
Our fastest growing area today is the mobile application market. It has been growing in popularity for over a decade now. Within the mobile space, there are specific segments that are more popular, since they are targeted more often for attacks, e.g. banking and finance.
A little further out in the future, but already growing rapidly, are applications for connected medical devices and connected automobiles.
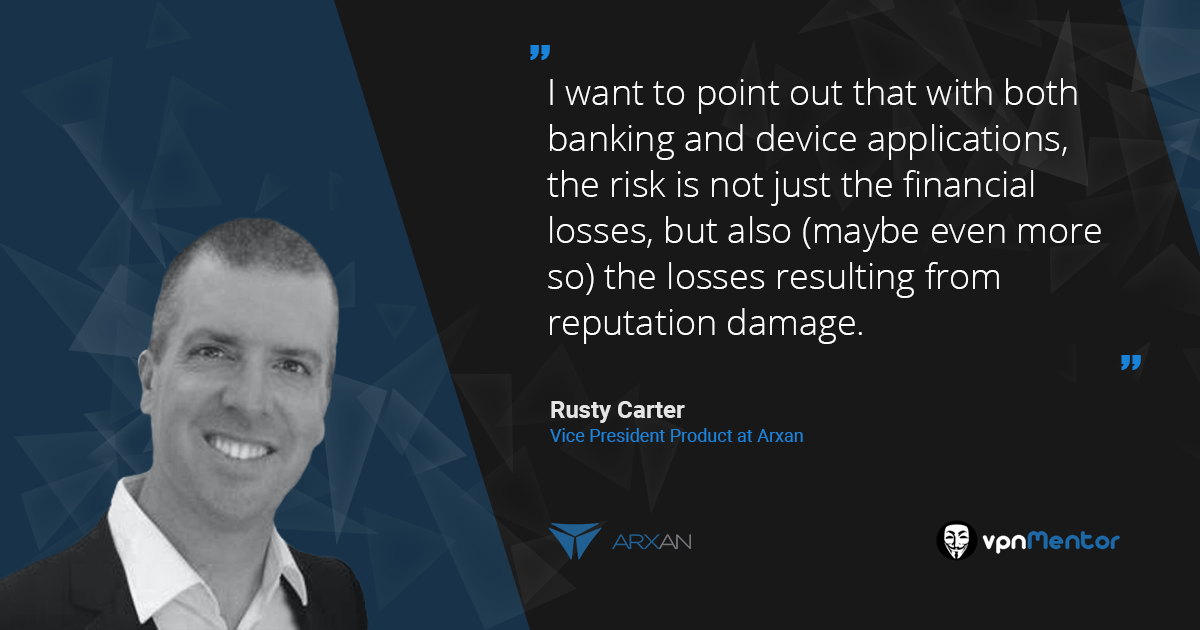
I want to point out that with both banking and device applications, the risk is not just the financial losses, but also (maybe even more so) the losses resulting from reputation damage.
What does it take to incorporate your products into an existing software development environment?
We have chosen an approach that is very low-touch for application developers. They just need to specify what/how to protect their application. Most developers do not even need to know about Arxan, because we act as a post-build step on the compiled binaries - the last step before final testing.
How does your pricing model work?
Our pricing is on a per-application basis, depending on the complexity of the application and the needs of the company. We also offer enterprise/site pricing for large organizations.
You also offer professional services. What percentage of your customers takes advantage of that? What percentage of your revenue comes from that?
That is actually a growing part of our business. We have a great team with a lot of knowledge and we focus on being a true partner with our customers.
As customers protect their applications, they begin to think more broadly and want to know how to also secure their data center. Large organizations utilize our resources on-site, helping them to manage and maintain the security of their applications throughout their entire environment.
How do you define your target market?
In the past, our main target markets were:
- Gaming
- Media
- ISVs (Independent Software Vendors)
- Application developers
Now, however, the biggest demand is in the following markets:
- Banking
- Mobile Payments
- Medical Devices
How many active customers do you have today? Where are they mainly located?
Our customers are distributed all over the world, but are primarily located in:
- North America
- Europe
- Asia
How would you describe your current typical customer?
Our customers are typically large global businesses, often consisting of multiple operating companies. As I mentioned previously, the main industry segments are banking, mobile payments, and medical devices. We also have several customers in the automotive and aerospace industries.
Whom do you see as your main competitors?
This market is still very young. I would say that our biggest competitor is “lack of awareness.” There are definitely other companies entering this space that compete with us in specific cases. What we have seen so far is that we usually win in these competitions, due to our depth and breadth in protecting all aspects of enterprise application development.
How do you see the security software evolving in the next few years?
We are seeing many new developments in this industry. In particular, developers are integrating new platforms into their development process, especially for mobile applications.
There is also a strong shift to hybrid web-mobile applications, using HTML and JavaScript for the user interface and business logic on the front end and using Java or C# for the business logic on the back end.
I recently interviewed Mark Lorion, the President and General Manager of Apperian, which Arxan acquired at the beginning of this year. Is that acquisition a major part of your growth strategy? How does Apperian complement your existing products?
There is a very strong synergy between our two companies. Apperian focuses on application management and Arxan focuses on application protection. This combination allows us to provide greater end-to-end protection for our customers’ applications.
What are some of Arxan’s future plans?
Our aim is to deliver comprehensive safeguarding for applications. Our perspective extends beyond perceiving an application solely as software installed on a specific device; instead, we adopt a broader interpretation. Our ongoing efforts revolve around developing technologies and solutions that cater to this broader definition, supporting and ensuring the protection of applications in various dimensions.
How many hours a day do you normally work? What do you like to do when you are not working?
That is very hard for me to define. I really love what I do and the job of a product manager is not a 9-5 job. I am in the office during normal working hours, but I am working through issues with customers at all hours of the day.
I used to be a competitive ultra-distance athlete, until my son was born three years ago. Now I enjoy biking on trails together with him.