
BeyondTrust – Making Sure Users Don’t Abuse Their Privileged Access Permissions
- Let us start with a little bit about you and your background.
- With your slogan “Stop Privilege Abuse,” BeyondTrust is somewhat different from most security companies in that you focus on insider attacks and then outsider attacks. Why is that?
- Your website talks about solutions and products – what is the difference between them?
- How do you define your target market?
- What does your pricing model look like?
- How many active customers do you have today?
- Who are some of your biggest customers?
- Whom do you see as your main competitors?
- You recently released the results of your annual Privileged Access Management Survey. Please tell me a little bit about the survey and this year’s results.
- How do you see the security software market evolving in the next few years?
- What are some of the future plans for BeyondTrust?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
BeyondTrust is convinced that the greatest cause of enterprise data breaches is the fact that users abuse the privileged level of access permission given to them, i.e. admin or root access. Sometimes this abuse is malicious and sometimes it is accidental – but it is always a bad thing. The BeyondTrust platform and tools address what is known as “Privileged Access Management” from several different angles.
In my discussion with Morey Haber, Vice President of Technology at BeyondTrust, we discuss the four pillars of the BeyondTrust platform and what concerns they each address. We also discuss the results of their annual Privileged Access Management Survey and what new findings they uncovered this year.
Let us start with a little bit about you and your background.
I have been in the security field for over 20 years. I started my career as an engineer building flight simulators and training equipment. I then spent 7 years at CA (Computer Associates) managing aspects of their Unicenter SWAT team. From there I went to a company called eEye Digital Security, where I was responsible for the product management of their vulnerability and endpoint solutions. After almost 8 years, BeyondTrust acquired that company (in 2012), which brings us to where I am today.
With your slogan “Stop Privilege Abuse,” BeyondTrust is somewhat different from most security companies in that you focus on insider attacks and then outsider attacks. Why is that?
After the merger of the two companies, we worked to better understand security threats in the enterprise. What we found was that many – if not most - data breaches were due to social engineering, insider abuse, and exploiting privileged admin (administrator) access.
Your website talks about solutions and products – what is the difference between them?
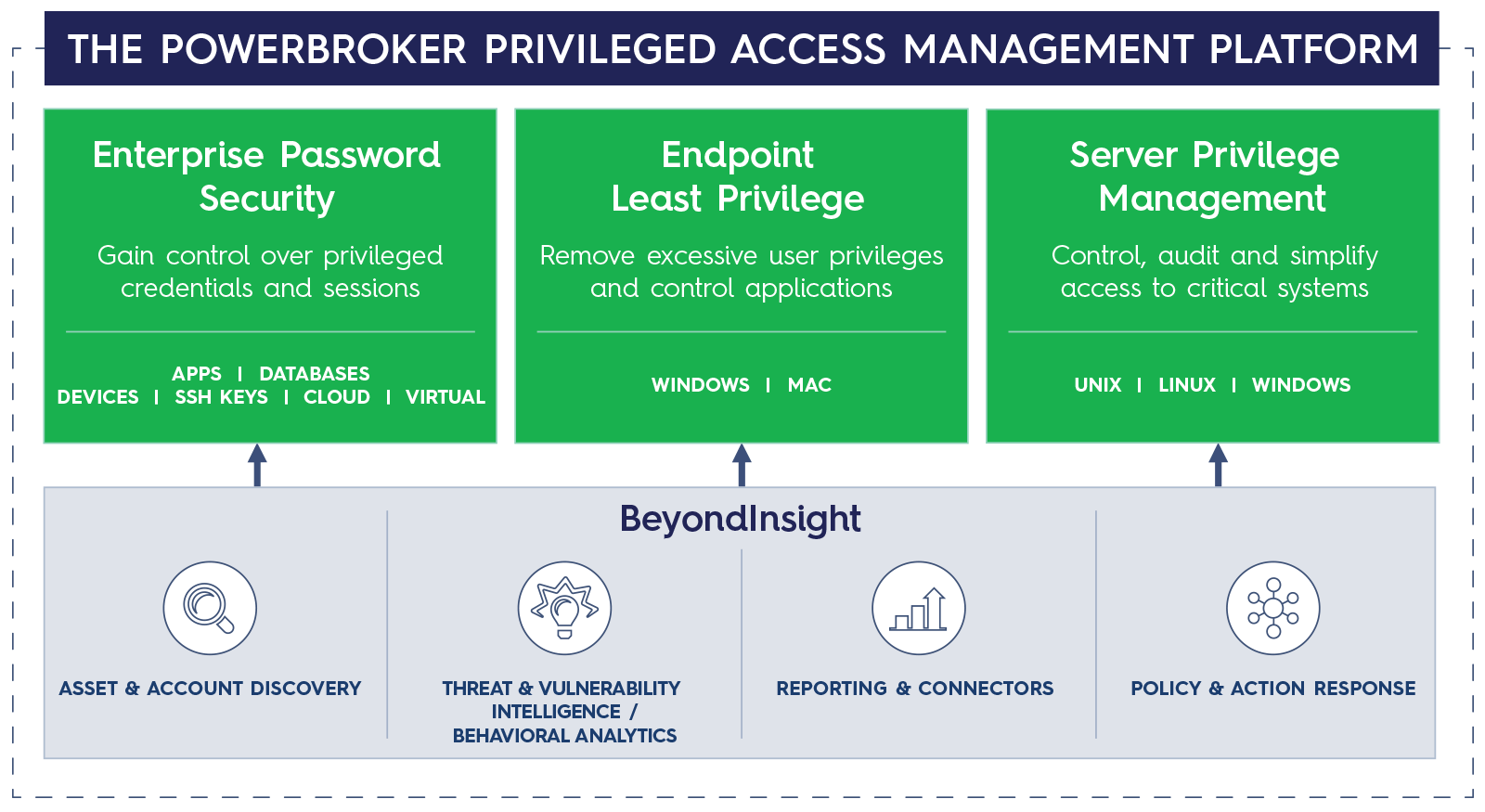
At the heart of our solutions is our PowerBroker family of solutions. The technology is a platform for Privileged Account Management (PAM). Our platform has four main product pillars, each of which addresses a different aspect of PAM:
- Privilege Management – Ensures users normally operate with the least level of privilege required. Admin/root access is removed from everyone – but when admin/root access is actually required for specific tools or actions, the access is granted and then every keystroke or action is recorded, saved, and reported.
- Password Management – Passwords are stored in a “safe” and need to be checked-in and checked-out when needed. The passwords are constantly changed and are never shared. The technology is applicable to users, service accounts, applications, scripts and even cloud deployments.
- Active Directory Bridging – Users authenticate with Windows Active Directory credentials on Unix and Linux assets. This allows you to eliminate all local accounts and to track the same user ID across all of your systems while also controlling key settings on Unix and Linux via Group Policy Options.
- Auditing, Reporting, and Protection – Monitors, detects, and reports any changes to Microsoft Active Directory, file systems, Exchange servers, etc. Also provides backup and recovery services for instant rollback
How do you define your target market?
The main driver for our business are regulatory requirements, such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), PCI DSS (Payment Card Industry Data Security Standard, ASD (Australian Signals Directorate), SWIFT Networks, etc.
Therefore, our target market is organizations that operate in highly regulated industries. Our biggest verticals today are financial services and healthcare, but we are starting to see a lot more demand from companies in the insurance, manufacturing, and telecommunications industries.
What does your pricing model look like?
Our products are available in several different forms, in order to meet the needs of our customers:
- Software
- Virtual Appliance
- Physical Appliance
- Cloud Marketplaces (Google, Azure, AWS)
We base our pricing on a per-asset license model. That means every physical device, virtual machine, and/or cloud resource requires a license for our solutions regardless of the number of users that interact with the technology.
How many active customers do you have today?
We currently have more than 4,000 paid customers on maintenance agreements, including half of the Fortune 100 companies. Most of our customers are located in North America.
Who are some of your biggest customers?
Our customers include 8 of the world’s 10 largest banks, 8 of the world’s 10 largest aerospace and defense firms, 7 of the 10 largest US pharmaceutical companies, all 5 branches of the US Military, and renowned universities across the globe.
I can give you a sampling of some specific names:
- Sprint
- Verizon
- Exxon Mobile
- Bank of American
- Prudential
- Capital One
- NASA
- Abbott
- Blue Cross Blue Shield
- Paypal
- MTV
- Time
- Boeing
- Oracle
Whom do you see as your main competitors?
There are a lot of companies competing in this space. However, many of them only address one pillar of PAM, instead of the multiple aspects of PAM. We have been most successful when we are able to sit with a company’s senior management and discuss overall strategy and the benefits of having a single vendor that can address all of their needs. Our products and solutions include multiple patents integrated together.
You recently released the results of your annual Privileged Access Management Survey. Please tell me a little bit about the survey and this year’s results.
We have been doing this annual survey for several years now. The statistics generally fall in line with what other similar survey reports.
This year, however, we decided to ask more leading questions, in order to get a better understanding of user behavior and to identify the words that explain why people are fearful of giving up admin rights. We surveyed nearly 500 IT professionals from around the world with involvement in privileged access management. Here, we were actually somewhat surprised by what we learned and it led us to put together our paper on "The 5 Deadly Sins of Privileged Access Management.”
We discovered five reasons why people continue to use elevated access rights despite the known security risks:
- Apathy – Even though the threat level is high, respondents report bad password practices still persist
- Greed – Users hold out removing administrator rights despite the risk
- Pride – Teams ignore the risk of excessive privileges with an attitude of “it will not happen to me.”
- Ignorance – Belief that the security controls built into an operating system or application are sufficient to protect the organization
- Envy – The risk of the cloud, BYOD (Bring Your Own Device), and on-premise privileges are believed not to be the same for everyone. That is just not true.

Our report also offers several steps that any organization can take in order to address these issues:
- Deploy enterprise password management globally across all data centers.
- Remove local admin rights from ALL Windows and MacOS end users immediately.
- Prioritize and patch vulnerabilities.
- Replace Sudo for complete protection of Unix/Linux servers.
- Unify all privileged access management into a single console for management, analytics, and reporting.
How do you see the security software market evolving in the next few years?
There is a rapidly increasing emphasis on the cloud. Today, moving to the cloud can be very expensive, but once you have made the transition, operating in the cloud is much cheaper. Many analysts have papers validating the return on investment.
Because of the long-term savings, we are seeing an explosion in the market of security tools for the cloud environment. The challenge for us, as tool providers, is to design and optimize our products to address the unique requirements of a cloud environment. In many ways, this is a whole new market!
What are some of the future plans for BeyondTrust?
Right now, security tools are essentially defensive – their goal is to try to prevent security threats. We want to change that by partnering with other leading companies so that our security tools can be offensive and provide automatic responses to detected threats.
Moving forward, our biggest push is focusing on completing these automatic threat responses, which include actions such as:
- Quarantining Users and Applications
- Stopping Processes and Inappropriate Behavior
- Monitoring and Preventing Lateral Movement
How many employees do you have today? Where are they located?
At present, our workforce exceeds 400 individuals, primarily based at our headquarters in Phoenix, Arizona. In addition, we have dedicated development teams situated in California and Canada. Furthermore, our sales and marketing offices span across the globe, reaching from the United Kingdom to Australia.
How many hours a day do you normally work? What do you like to do when you are not working?
I am generally online 10-12 hours every day. It is just the nature of this career. Almost every morning there is another breach, exploit, or threat to learn about, address in technology, and respond to clients protecting their environments.
Outside of work, I enjoy spending time with my family and kids and look forward to my recreational activities with them. And I rarely pass up the opportunity for a concert or science fiction movie.


