VPN Leaks Found on 3 Major VPNs out of … 3 that We Tested
In 2018, we tested 3 popular VPNs: Hotspot Shield, PureVPN, and Zenmate with accredited researchers to find if the VPNs could leak data.
While we hoped to find zero leaks, we regretfully found that all of them leak sensitive data.
On the positive side, after we contacted the VPN vendors, we saw that two were fast to respond and release a patch within days.
Here's a is a summary of our findings
- Hotspot Shield, PureVPN, and Zenmate VPN all suffer from IP leaks.
- The leaks allow governments, hostile organizations, or individuals to identify the actual IP address of a user, even with the use of the VPNs.
- Zenmate’s leak was somewhat minor compared to the two other VPNs.
- We believe that most other VPNs suffer from similar issues, so the fast response of Hotspot Shield is something we think is worth commending. We felt that they worked with our research team in a fast and serious manner and that they care for their users. They took our research as help for improvement rather than criticism.
- Since it took longer for ZenMate and PureVPN to respond to us, we are only sharing information about the vulnerabilities that were found and patched in HotSpot Shield. We advise users of PureVPN and Zenmate to be wary of the leaks they may face and check with their VPN providers for an immediate fix.
The research team
VpnMentor hired a team of three external ethical hackers to find vulnerabilities in three random popular VPNs.
While one hacker wants to keep his identity private, the other two are known as File Descriptor and Paulos Yibelo.
File Descriptor is a reputable, ethical hacker working for Cure53, the company hired by TunnelBear to identify and fix issues with their VPN applications, and one of the leading companies in security research.
Paulos Yibelo, who also managed the team, is a reputable application security researcher. He has found vulnerabilities in popular VPNs and published them in the past. His work was mentioned in ZDNet, SlashDot, and other media sources.
*As part of the agreement with our research team, vpnMentor cannot directly influence the research team nor the conducted research.
Hotspot Shield's Vulnerabilities
These are the technical details of Hotspot Shield’s vulnerabilities, which have all been fixed by the company:
All the issues are related to PAC scripts and were found in the Chrome plug-in. The mobile and desktop apps were not affected by these vulnerabilities.
1. CVE-2018-7879: Hijack all traffic
We observed the following PAC script used in Hotspot Shield Chome extension:
if(url.indexOf('act=afProxyServerPing') != -1) {
let parsed = url.match(/act=afProxyServerPing&server=([^&]+)/);
if(parsed && parsed[1]) return 'https '+parsed[1]+':443; DIRECT;';
}
It detects if the current URL has the query parameter act=afProxyServerPing, and if it does, it routes all traffic to the proxy hostname provided by the server parameter.
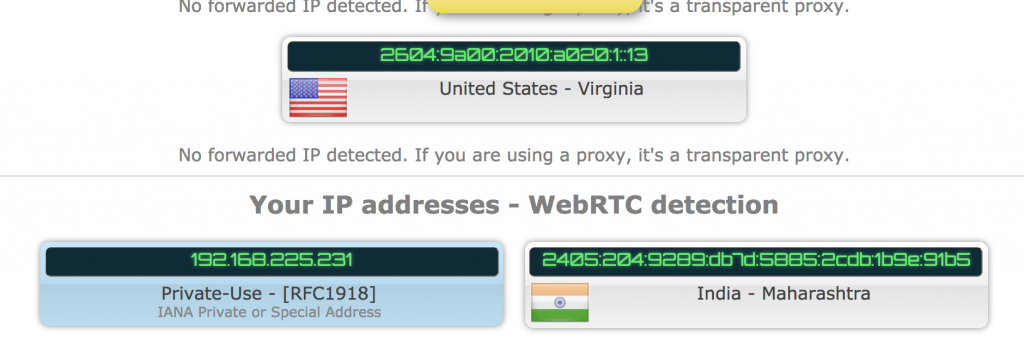
 This is a result of the proxy hijack.
This is a result of the proxy hijack.
While we believe this is for internal use, it fails to validate what host is making this "call". Therefore any URL with the aforementioned parameters will have the traffic routed to the specified proxy.
The problem with this is that a malicious adversary could simply ask a victim to visit a link with those parameters, and all traffic will go to an attacker's proxy server. It would be worse if the connection is on HTTP.
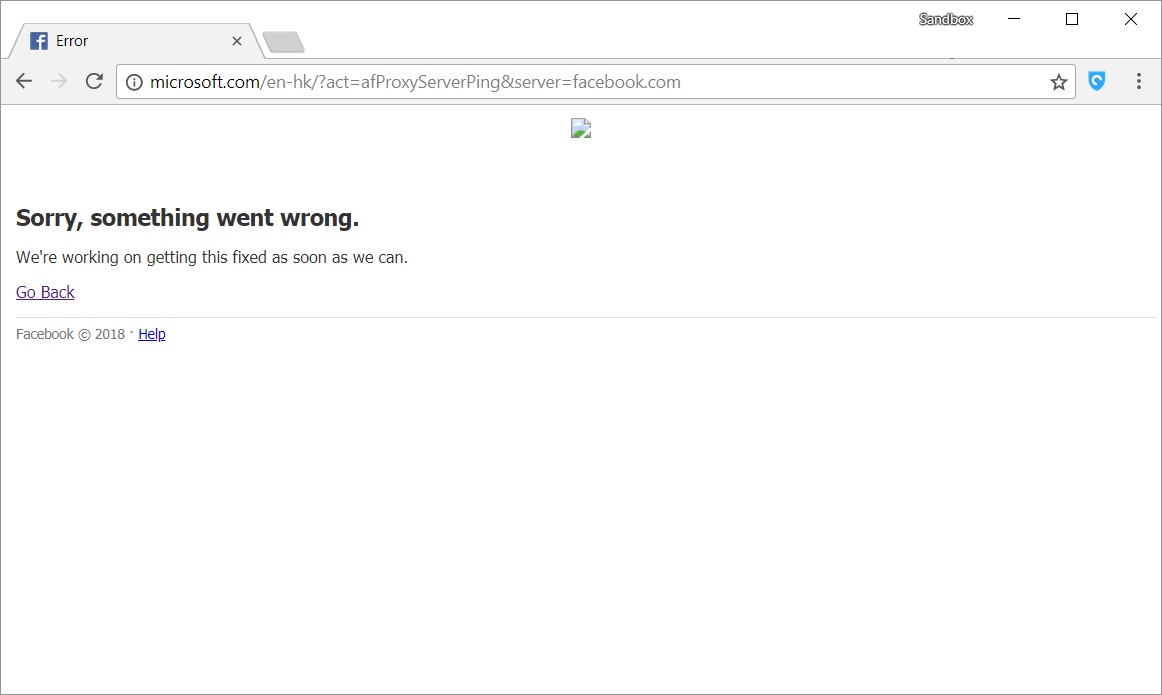
2. CVE-2018-7878 DNS leak
We observed the following PAC script:
This means that dnsResolve will make a DNS request via the system DNS. This is essentially leaking DNS, as the proxy is only assigned after all those conditions.
How do we prove it?
A simple check in https://www.dnsleaktest.com/ reveals your DNS server. This example shows the leak we found with HotSpot Shield.
 Our leak that we found with HotSpot Shield on the Chrome extension
Our leak that we found with HotSpot Shield on the Chrome extension
Take note, any website has the ability to identify the DNS server a user is utilizing, thereby potentially revealing your country and other crucial details. This website serves as a tool designed to assist you in verifying such occurrences.
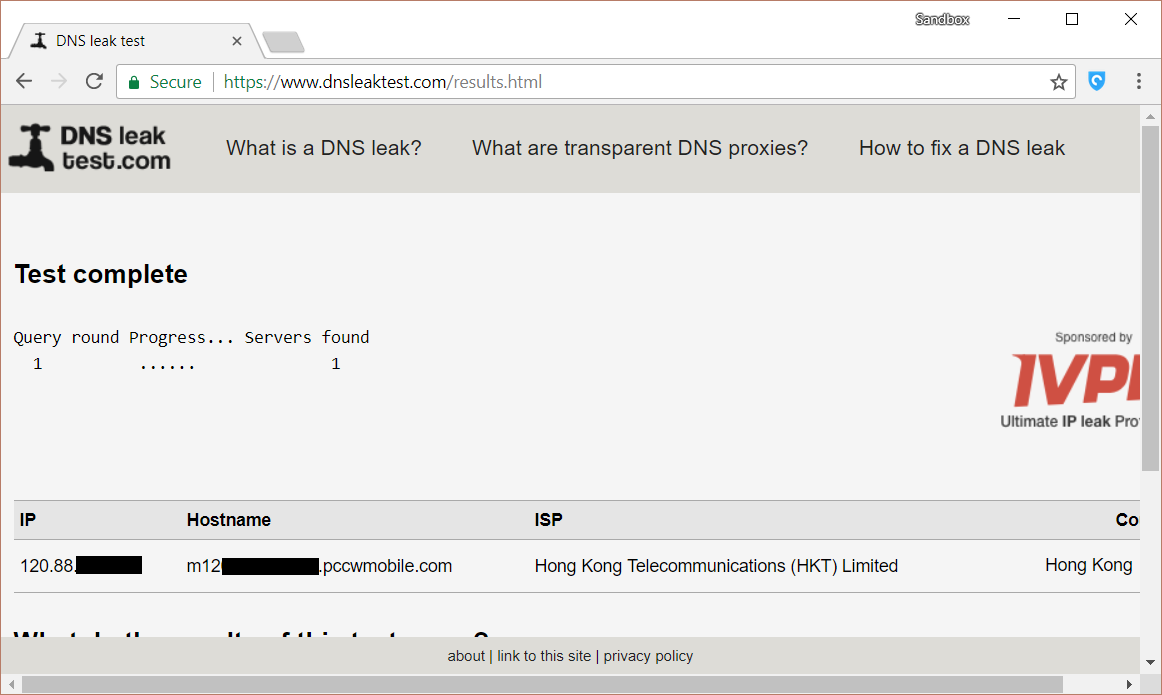
3. CVE-2018-7880 IP leak
We observed the following PAC script:
What we found is that the whitelist for DIRECT connection is just too loose.
Here are two examples we found:
- Any domain with localhost will bypass the proxy, e.g. localhost.foo.bar.com
- Any URL with type=a1fproxyspeedtest will bypass the proxy
How do we prove it?
We went to this site with the unpatched version of Hotspot Shield, and our actual IP was leaked.
 Our IP address was revealed when we tested it.
Our IP address was revealed when we tested it.
This means that when Hotspot Shield sees the parameter a1fproxyspeedtest in any URL, it routes all traffic to the proxy hostname provided by the server parameter. Therefore, if a hacker redirects someone who is using HSS to https://example.com/?act=afProxyServerPing&server=mywebsite.com, that website will get a hit from the user’s actual IP address.
We found similar vulnerabilities in Zenmate VPN and PureVPN. While Hotspot Shield already updated their service with a patch, we hope this will prompt the other VPNs to do the same.
Additional research on ZenMate and PureVPN
PureVPN's leak
 Visiting a website using the Firefox browser revealed our IP address with PureVPN.
Visiting a website using the Firefox browser revealed our IP address with PureVPN.
We will not go into detail about PureVPN's and ZenMate's vulnerabilities (please see each VPN's response below). While they are not exactly like HotSpot Shield's vulnerabilities, they are similar.
VPN's responses
Hotspot Shield:
After fixing the vulnerabilities, Hotspot Shield contacted vpnMentor with this message.
"The researchers hired by vpnMentor did not find any vulnerabilities in the mobile or desktop versions of Hotspot Shield. The vulnerabilities they reported were present only in the free Chrome plug-in. Neither mobile nor desktop users of the Hotspot Shield app were affected by these vulnerabilities. We appreciate and commend vpnMentor's initiative to improve the security of consumer VPN applications, and look forward to seeing more research from their side involving more VPN products in the near future."
Zenmate:
"I would like to give you some more background to the security issues vpnMentor found in ZenMate's browser extension. We appreciate the work from vpnMentor in pointing out potential problems as the security and privacy of our users are very important to us and we put a lot of effort in to protect that. In fact, we are one of the very few commercial VPN companies operating under very strict German privacy laws and do not track, log or sell the data of our users, as opposed to many other companies in this field.
We are aware of that situation since Google introduced WebRTC in its Chrome browser and of the fact that there are possible privacy implications of WebRTC as they are generic to every VPN and not only affecting ZenMate users. Additionally, we are very transparent and open with the communication to that: We have a support article (https://zenguard.zendesk.com/hc/en-us/articles/201259661-How-can-I-protect-myself-from-IP-leaks-caused-by-Flash-or-WebRTC-) that explains this issue and also tells the user how what to do to prevent IP leaks (for example to install the extension WebRTC Leak Prevent). Moreover, we also mention that on the description of the extension in the Google Chrome Webstore.
One of the reasons why we decided not to block that in our extension like some of our competitors do is that there are some webservices out there that rely on WebRTC. WebRTC is a complex matter and just disabling it without educating the user on possible downsides is unfortunately not an option for us, as we thrive to provide the best user experience possible in our products. Many services rely on P2P realtime communication to function properly, e.g. Google Hangouts would stop working if WebRTC would be disabled.
To solve that issue immediately for our users we suggest to install the extension WebRTC Network Limiter (https://chrome.google.com/webstore/detail/webrtc-network-limiter/npeicpdbkakmehahjeeohfdhnlpdklia?hl=de&) and select the 4th option (see attached picture). However, we understood that this might not be clear enough and currently work on a dedicated new product to specifically protect against possible WebRTC privacy issues in a new user-friendly way. This new product will be promoted through our VPN extension whenever WebRTC is being used and interconnects with our VPN offering in a seamless way."
PureVPN:
"In continuation of our communication regarding the article recently published on vpnMentor regarding VPNs leaking users' IPs, I have updated you our stance on it.
The Firefox browser, by default, has an inherent limitation where it makes it almost impossible to identify and differentiate remote and local hosts. Our intention was to allow users the freedom to access all local domains conveniently while using our extension.
I am sure that the tests you carried out were not on the latest build, since it has already been patched.
The Firefox store clearly shows that our extension was last updated on March 07, 2018, and this update included the fix for the above-mentioned issue."
What does this mean to a VPN user?
VPNs are not as safe as many may think.
The fact that we found leaks in all the VPNs that we tested is worrying.
Our guess is that most VPNs have similar leaks and that users should take this into consideration when using VPNs. If you use Hotspot Shield or PureVPN user make sure you have updated your app. If you are a user of Zenmate, make sure you are aware of the (minor) vulnerability that we have indicated and follow Zenmate’s instructions.