Rohde & Schwarz Cybersecurity Allows Companies to Maintain Full Security Control “Under the Hood”
- Please tell us a little bit about your background and current position at Rohde & Schwarz Cybersecurity.
- Recovering from the March 22 cyber-attack has already cost the city of Atlanta $2.7 million, and that number is expected to rise. How can your R&S®Browser in the Box protect local governments and companies, for that matter, who may have limited cybersecurity budgets and outdated technology?
- What if a company needs to download files from the internet?
- What are the biggest issues with security for mobile devices and how does your R&S®Trusted Mobile product help keep them secure?
- How does R&S Trusted Gate - Solution for Office 365 protect business-critical information contained in Microsoft Office 365 applications?
- What new security risks have been created by the emergence of the IoT (Internet of Things) and what solutions have you developed?
As the work environment becomes increasingly mobile, and more devices than ever before are connecting to company networks, security challenges are increasing exponentially. Rohde & Schwarz Cybersecurity has developed technologies to keep networks secure by isolating sensitive data from the open internet while allowing employees to continue to use their applications without any additional steps or new skills.
Please tell us a little bit about your background and current position at Rohde & Schwarz Cybersecurity.
My background is a very technical one. I’ve been in IT security for over 15 years. I was with HP Labs in the UK for ten years working on IT security, networking data center, high-speed networks and so on. About five years ago I joined Rohde & Schwarz Cybersecurity.
Recovering from the March 22 cyber-attack has already cost the city of Atlanta $2.7 million, and that number is expected to rise. How can your R&S®Browser in the Box protect local governments and companies, for that matter, who may have limited cybersecurity budgets and outdated technology?
Our R&S®Browser in the Box addresses one of the biggest issues we face today: protecting ourselves and our data while browsing the internet. In the end, it is a simple product, but it addresses these threats by separating your data from the internet, assuring secure browsing. Any site you visit, any file you download, is always contained in the virtual machine and cannot cross over into the platform where you keep your confidential or sensitive data. It’s a very effective product because whenever the browser is closed, all the data in the browser gets destroyed and whenever it is opened again it is a completely fresh browser. This assures malware cannot persist on the platform and furthermore offers ways to separate what is your internet and what is your trusted internal data. It is seamlessly integrated into the Windows environment, so it’s transparent to the user and has no learning curve.
Additionally, the browser is running on a virtual machine using its own file system with no access to anything on the real system, so it does not actually see any of the files on the computer. It’s like a separate machine on your PC which makes it is impossible for malware to either spy on your computer files or to spread to your system.
Another security aspect is that the browser uses a VPN connection gateway located at your headquarters. In this way, even if the browser gets compromised with malware it wants to spread, it is restricted and cannot get onto your LAN since it is located outside of your network.
What if a company needs to download files from the internet?
For those cases, we have created Information Flow Control to regulate when information crosses from one domain to another, like from the internet to your intranet. For a user to transfer his downloaded files to his local file system, the company’s security administrator needs to allow for that activity by setting up a provision in the central management system. They can also set a policy that only allows certain types of files. The file can then be placed in a “staging area” sort of like a sandbox where virus scanners or other filters can be applied. Only if the file passes those scans will it then be allowed to be transferred onto a local host or file system.
It's crucial to realize that the discretion does not lie with the user, but with the security administrator to decide who is authorized to download which kind of file and which procedure should be used to scan the file. Only after these security controls have been established can files be downloaded to the file system and stored permanently.
What are the biggest issues with security for mobile devices and how does your R&S®Trusted Mobile product help keep them secure?
As mobile devices are being used more and more for business and government purposes, their security is also becoming more important. With R&S®Trusted Mobile, companies can provide their employees with a cell phone that looks like a regular Android phone but actually has two parts. One is what we call the “personal area” where a user has full control and can download Facebook, Google Apps, games, etc. That personal area has a direct connection to the internet and is unrestricted for personal use. Then on the other side, it has what we call the “business area” which is highly restricted. This is where all the business apps such as your mail client, your secure browser, etc. are pre-installed on the phone by the company. These business apps don’t go directly to the internet but rather through a VPN gateway at the corporate site where the security administrator decides which business apps can go on the internet or just allowed to go to the intranet. Or maybe the admin wants to allow business apps only able to reach the mail server and some internal file server, but not the internet.
This way users don’t have to start a VPN client or look after security themselves as it’s all done under the hood by the R&S®Trusted Mobile platform. So, there is one device, but it has sort of has two personas, one for personal use and the other for business. The platform ensures that you can use your device securely for processing sensitive data and reading confidential emails, while at the same time on the same device you can have your FB, your WhatsApp, etc. The platform enforces the separation, so this is a bit like the Bring Your Own Device idea that people don’t need to have multiple phones for their personal use while R&S®Trusted Mobile operates to secure corporate data.
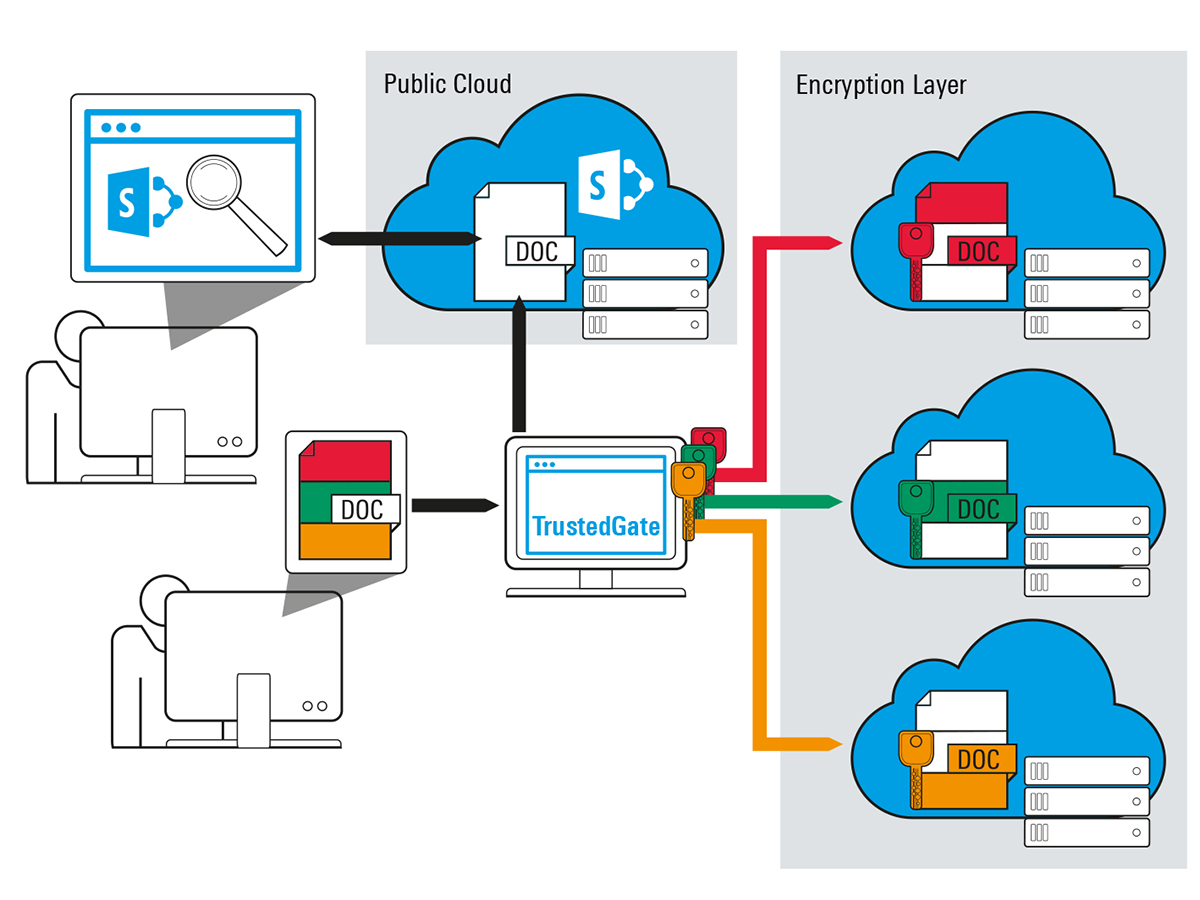
How does R&S Trusted Gate - Solution for Office 365 protect business-critical information contained in Microsoft Office 365 applications?
R&S®Trusted Gate – Solution for Office 365 is one of our most exciting products! It focuses on a secure PC, laptop, or tablet in the Windows environment. It’s a very efficient component that sits on your infrastructure, securely processing, intercepting, and encrypting data on the fly before it is moved out into the public or onto the cloud. Those encrypted data chunks are then completely under your control, so you can either keep your data on-site or once encrypted, securely store it on public clouds. R&S®Trusted Gate runs completely seamlessly under the hood, so there is no change in the way employees use Office products, cloud products, Sharepoint, etc.
What new security risks have been created by the emergence of the IoT (Internet of Things) and what solutions have you developed?
At Rohde & Schwarz Cybersecurity, we have a strong background in hardware security and hardware security modules, and since IoT space is a very big area, we have different offerings. For example, firewall and network analytics products which focus more and more on the protocols used in the IoT space helping to protect the network and IoT solutions. We’re working with factories to ensure the connectivity of their machines while securing IoT devices and protecting their network. We also have secure Linuxware that is going in the direction of IoT.
Additionally, we have different technologies that can identify and authenticate a device, allow secure updates for that device, have a secure crypto implementation, and also have network connectivity and network encryption for those kinds of devices.