
Cybernance’s Unique Software Quickly Identifies Cyber-Risks People, Policy and Process are Key
- Please tell us a little bit about your background and current position at Cybernance.
- With major companies like Verizon and Equifax spending large amounts of money on online security, how are they still able to be breached?
- What is the NIST Standard?
- How does Cybernance help companies comply with NIST?
- Do the results give recommendations to improve compliance?
- Last April Cybernance was designated as a Qualified Anti-Terrorism Technology (QATT). What does that designation?
Today’s companies spend a lot of money on technology and devices to keep their information safe from bad actors that intend reputational or financial harm. But no matter how good the technology in place may be, it is imperative that companies set policies assuring that none of their practices inadvertently open a door and release sensitive data. Cybernance’s software helps companies easily identify dangerous practices and lack of important policies while recommending ways to correct these cyber-risks.
Please tell us a little bit about your background and current position at Cybernance.
I've been in the technology world for all my adult life. During that time, I started and sold a string of companies, the latest of which was Infoglide Software. After the sale, on my wife’s recommendation, I began looking very carefully at cyber risk within businesses and government and realized this was going to be a major issue with which they were not well equipped to deal. There was already a lot of money being invested in technical solutions at the perimeter (dig the moat deeper, build the wall higher), but it seemed to me that cyber-risk management related to governance, policies, and processes was sorely lacking.
The company I ran before Cybernance developed all of the underlying algorithms for the TSA’s terrorist screening program. I became very versed in risk management, identity management and all the things that go along with that very advanced software development, so it was a natural transition into this business
My “Aha Moment” was when I heard Luis Aguilar, who at the time was the head of the SEC, speak in Boston. He believes boards of directors could and should be held personally liable for cyber breaches when they do not adequately protect their enterprise.
With major companies like Verizon and Equifax spending large amounts of money on online security, how are they still able to be breached?
Equifax is today's poster child for management teams and boards. They released 147 million records of individuals with private information into the marketplace in a cyber breach which was not a technology breach, but a breach of policy and process. What happened was they used a particular web server technology to roll out a new product offering into the marketplace. However, the product was released without adequately patching and protecting the web service. So, it wasn't the Masked Marvel and his dastardly team of bandits from some foreign country that broke into Equifax; it was Equifax leaving the door wide open.
Equifax testified before Congress that they found the person responsible and fired him. Let me tell you that this was not an individual one-person screw-up - that's not possible. It's a simple policy and process question, and for the life of me, I can't imagine anybody ever, ever doing that. I'm very critical of the management of Equifax, and I'm sure that they wish they could do it over, but these things don’t start at the bottom, it comes from the top. It results from inadequate leadership and the lack of a simple policy stating that nothing ever gets released to the open marketplace before it has gone through a rigorous analysis of the safety the efficacy of the system. That's why we have policies and procedures within companies.
What is the NIST Standard?
During the Obama administration when it became clear that the weakest point the protection of the homeland was going to be cyber, there was an executive directive to develop a national standard to help primarily commercial enterprises develop risk management practices. So, the government created the National Institute Standards and Technologies cybersecurity framework (NIST), which is a really unusual type of government product. Typically, when the government passes rules and commits money, they develop an entire set of “Thou shalt do this” and “Thou shalt not do that.” What they developed with NIST was not a set of prescriptive rules for how you should behave and sets of punishments if you don't, but rather a set of good ideas for best practices and considerations, which made it very easy for businesses to begin to apply.
How does Cybernance help companies comply with NIST?
The secret to NIST’s success is that these standards are not mandatory but highly recommended. This flexibility allows you to run your business the way you run your business while understanding where your cyber risks lie and how to address them. Rather than having to comply with all the rules, you only need to focus on those cyber risks that affect your business.
We chose to construct our enterprise on the foundation of the NIST standard, trusting that it would emerge as the leading cyber security/protection framework in the corporate sphere. Our prediction turned out to be accurate, as it is now utilized by just over 40 percent of businesses in the US and worldwide.
We based our company on automating the NIST framework through software. It's made up of about 80+ questions that result in about 400 control points within an organization. We take all these questions and break it down into ten domains, so the kinds of questions fit into a very tightly focused set of people. Naturally, we have questions addressing cyber risk and technology and standards, but there are also entire sets of questions around non-technology concerns. Remember, a substantial amount of cyber risk is introduced into businesses by their purchasing department when they buy products from outside vendors. There are also questions around HR processes, third-party vendors, and general organizational issues. The idea is to involve the person who has specific knowledge and expertise around these basic areas. Once they receive those queries from the system, they can answer them or forward them to somebody else they feel is be better equipped to answer. And so, like a waterfall, these questions go to the place within the organization where a person most likely to know can answer them.
We ask things like: Do you have a policy for this? Is that policy reviewed quarterly, annually? Is there an approval process? Do you have the following responses? And so on. The questions are answered with a value of zero through four, ranging from “we don't do it at all” to “we absolutely do it all the time.”
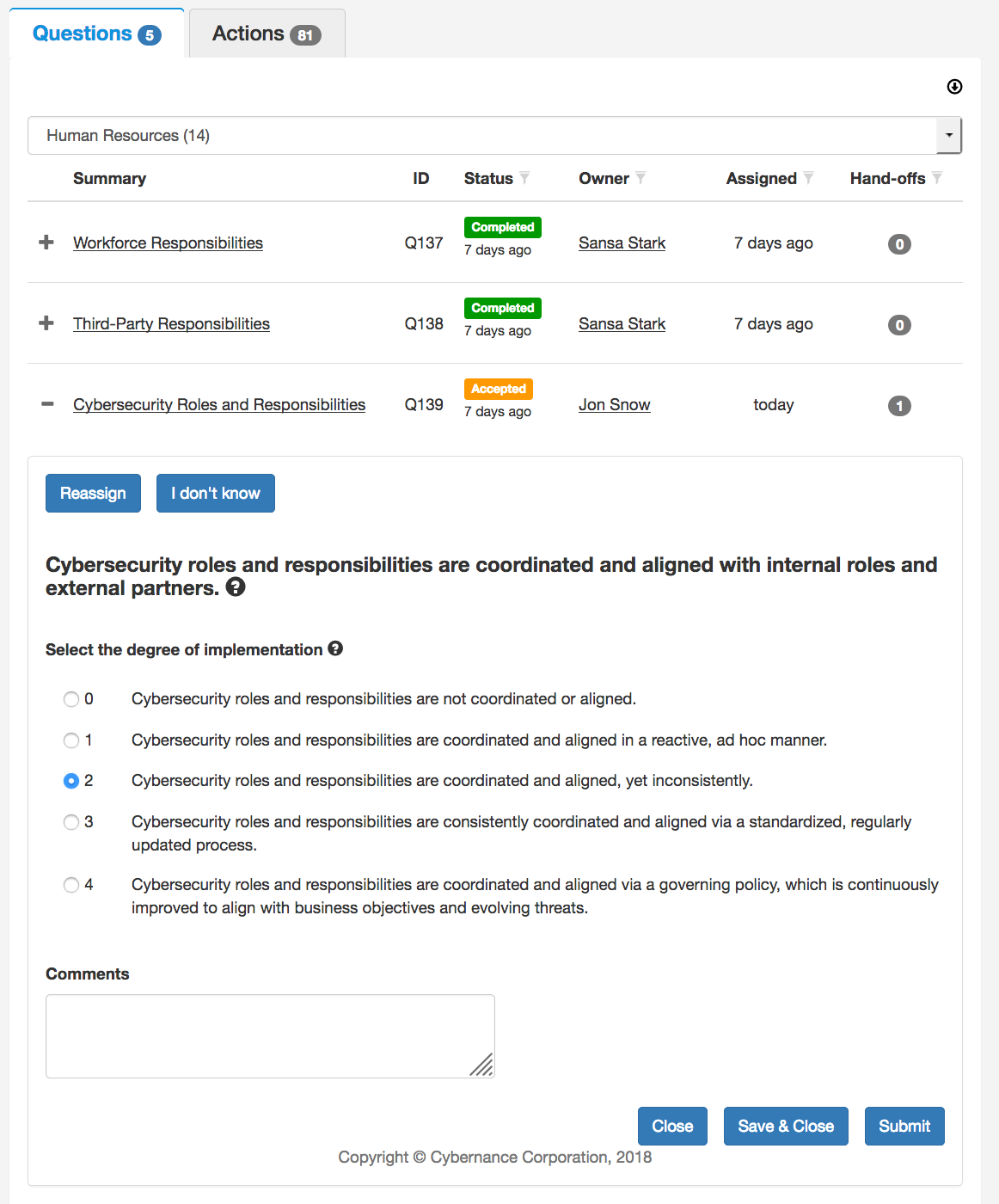
So, we’ve taken all of these standards, all of these control points, with all these queries and automated that process, so an organization can very quickly analyze their maturity and resilience based on the NIST standards. In fact, once the queries have found their way to the correct person within the organization, the process of answering and collecting the responses takes as little as 12-man hours.
Do the results give recommendations to improve compliance?
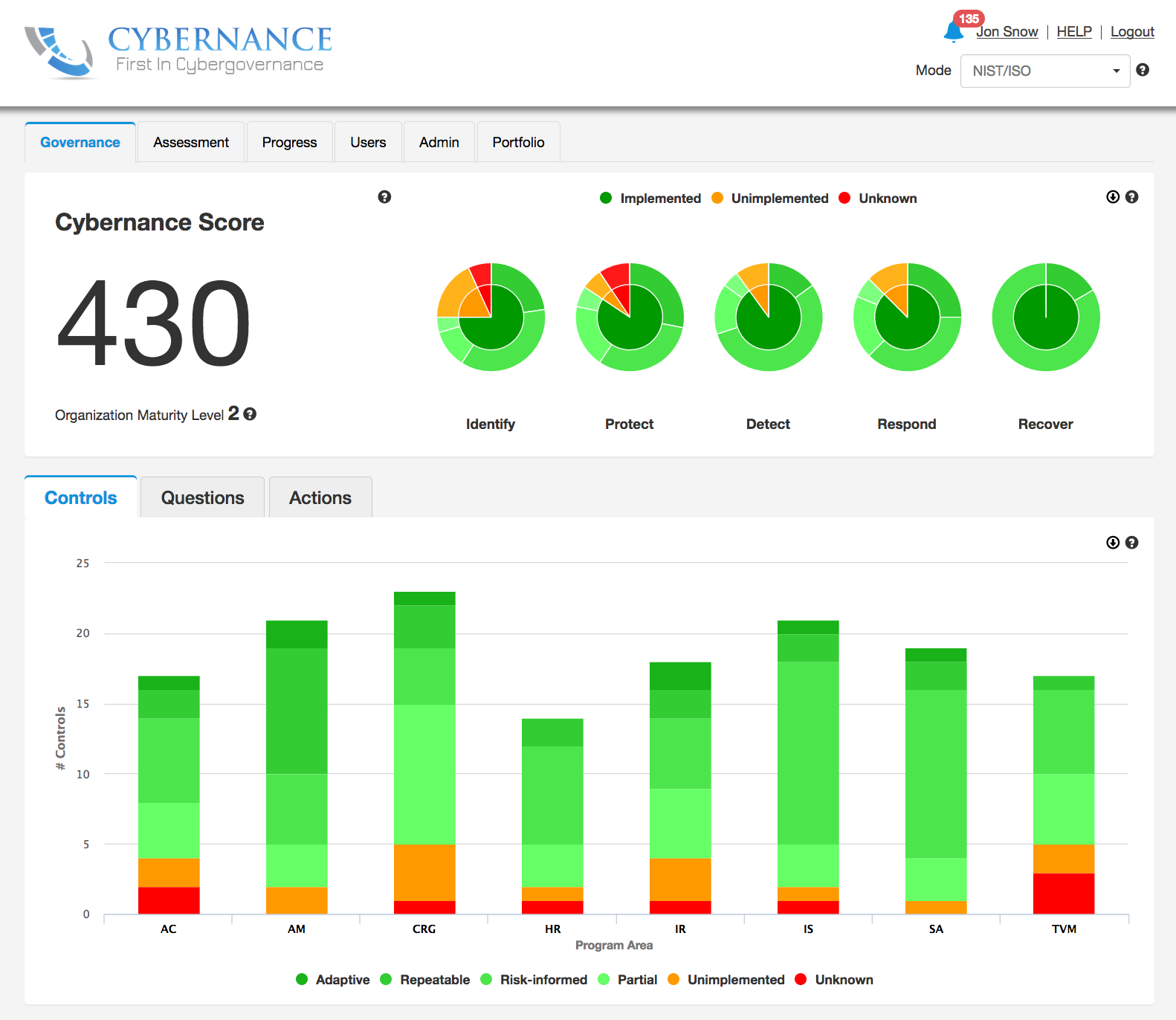
Yes, we roll all the results up into a dashboard which uses common business language (as opposed to technology language), so that the organization, including senior management and board of directors, can review and understand them very quickly. Along with listing the discovered risks relative to the NIST standard, we recommend corrective actions ranked by priority. Our dashboard processes in real time, so security gaps and recommendations are constantly changing as answers to questions are updated.
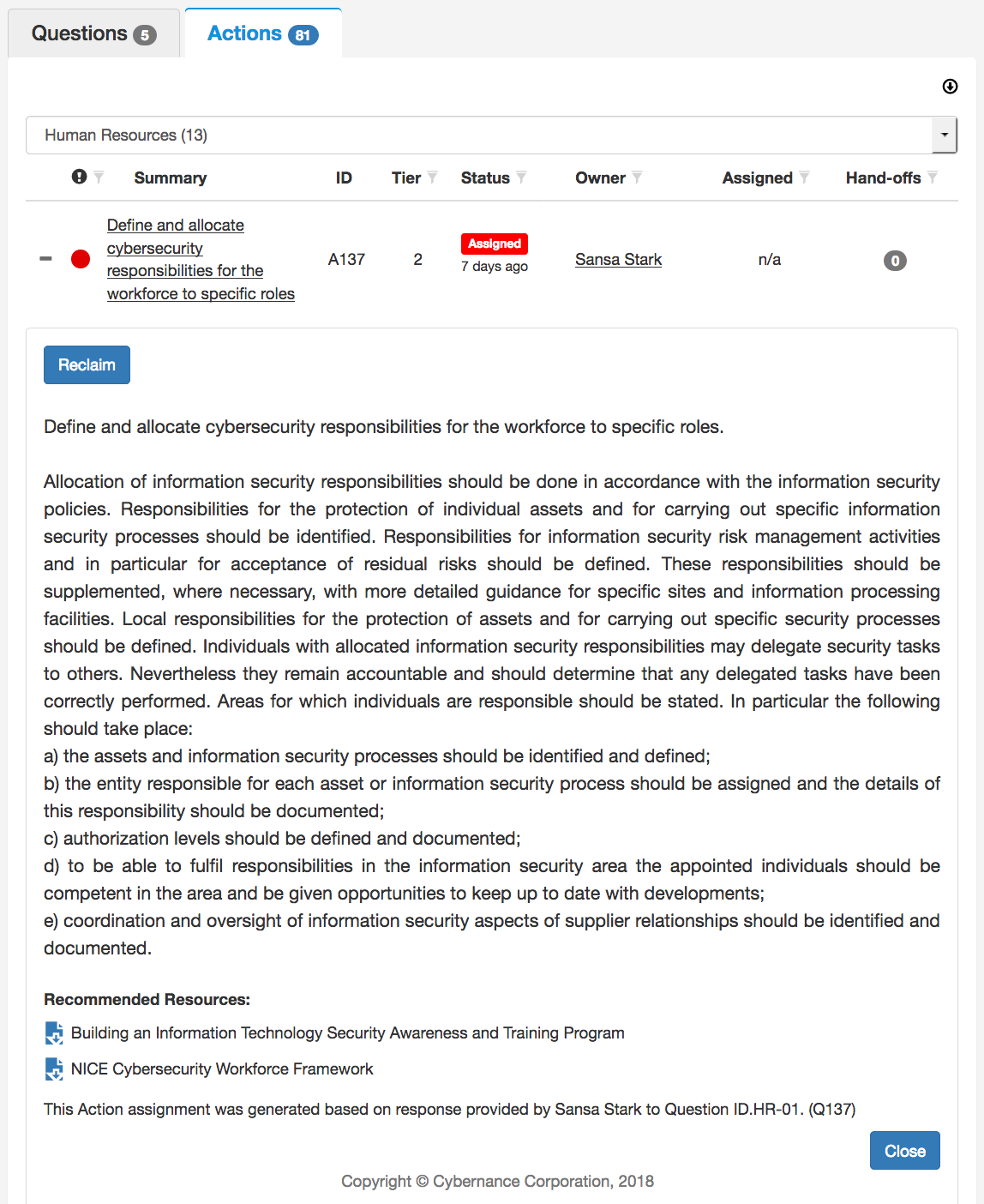
Our software also generates what you might call a score. However, it may not really be indicative of your particular cybersecurity risk. A company’s score can be very high if they are very strong in one area while another area leaves a gaping hole big enough to drive an 18-wheeler through. And they will never see that coming because of their “high score.” While on the other hand, a company with a “lower score” can actually have less risk, if many compliance queries are rated at zero simply because they simply do not pertain to their organization.
We also have a feature in the system where you can determine your risk acceptance and create goals for particular control points you may want to work on raising. So the score is really more to be used as a gauge of where you are today and where you’d like to be tomorrow.
The score is also helpful if you want to know where your company stands compared to your peers. We anonymize this data, so our customers can benchmark themselves against their peer group using SIC code, size, etc., giving them a good idea of how they’re doing within their industry. That's always important to management because, well, you know how this works; you put a ball on the floor with a room full of kids and pretty soon you've got a ball game. It’s very helpful to understand how you look within your industry to see if you are as good (or better!) or if you need to do more work.
Last April Cybernance was designated as a Qualified Anti-Terrorism Technology (QATT). What does that designation?
We submitted our product for review by the Department of Homeland Security's Safety Act office. We went through about a year of review and analysis by both Homeland Security and an independent contractor who took the technology and our company apart. They looked at it and questioned - does it do what we say it's going to do, does it do it correctly, is it a value, and is it likely to protect the homeland? And in the end, our product was named Qualified Anti-Terrorism Technology, known as the SAFETY Act, which means that if an organization uses our software as it's supposed to be used and there is a cyber breach based on terror, the organization has substantial liability protections up to and including 100% immunity for third-party actions.


