BullGuard – Protecting Your Computers, Home Networks, Smartphones, Tablets, and Most Importantly, You!
- Please tell us a little bit about your cybersecurity background and current position at BullGuard.
- What are some of today’s major online threats and how can they potentially compromise a computer or network?
- What products does BullGuard offer to keep users’ computers and information safe?
- I notice that many of your suites include both anti-malware software and a firewall. What are the differences between the two and why a user would need both?
- How does BullGuard’s Identify Protection keep customer’s personal information safe?
- How does Game Booster improve the gaming experience?
- What are some features of your Parental Control module? What “loopholes” have internet savvy kids used to bypass other Parental Control programs and how have you closed them?
- What are zero-day threats and how does BullGuard protect against them?
- Will having all these processes running in the background affect a computer’s speed or performance?
- What products do you offer for cell phones and tablets?
With cybercriminals becoming increasingly sophisticated in accessing all our connected devices and personal data, the traditional antivirus approach is simply unable to keep up with recognizing and stopping the constant emergence of new threats. We sat down with BullGuard’s CEO Paul Lipman to talk about their next generation engine and how it is continually learning to identify these malicious files to keep our devices, identities, and families safe.
Please tell us a little bit about your cybersecurity background and current position at BullGuard.
I find cybersecurity continually fascinating and challenging! I’ve been in the industry for over a decade at companies whose area of focus ranges from consumer endpoint security to enterprise cloud security. I joined BullGuard a couple of years ago with the express goal of taking it into the new, emerging and significant market of cybersecurity for the consumer home.
What are some of today’s major online threats and how can they potentially compromise a computer or network?
Probably the most significant online threat to consumers’ computers, and increasingly other connected devices, is ransomware, when a cybercriminal hacks into a device, encrypts or blocks a user from his own data and demands a ransom to return it. While most people will not succumb to ransomware threats as they’ll restore their data from a backup or the cloud, it’s still highly lucrative and almost impossible to trace. The traditional antivirus approach is simply unable to keep up as the combination of a zero-day attack with a ransomware payload is very challenging to prevent, and I’ll speak a little bit later about how we do that at BullGuard.
I think the other significant, emerging online threat are attacks against the Internet of Things, such as smartphones, connected baby monitors, thermostats, music systems, etc. Most of those products have little to no security protections, making them wide open jumping off points for malicious access to the home network. In our labs we have even seen hackers getting into home alarm systems and disarming them remotely. Unfortunately, we’re going to see more of this.
What products does BullGuard offer to keep users’ computers and information safe?
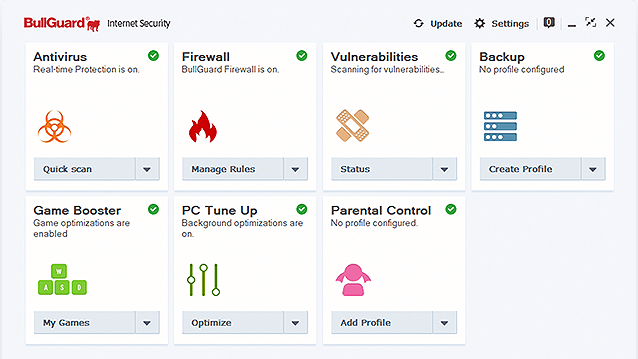
Our products for the PC, smartphone, and tablet range from the most lightweight anti-virus applications to a fully-featured internet security suite which includes identity protection, parental controls, technologies for improving and optimizing PC performance and the scanning of entire networks for potential vulnerabilities and threats.
We also offer Dojo by BullGuard (https://dojo.bullguard.com/) which secures home networks and all connected devices, regardless of what those devices may be. So even a connected smart lock, smart thermostat, etc., is protected against attacks.

I notice that many of your suites include both anti-malware software and a firewall. What are the differences between the two and why a user would need both?
Firewalls and anti-malware software serve different purposes. The best analogy is having a locked gate at the front of your property and then a lock on the front door of your house. You want to stop the bad guys at the gate, but if they make it through, you certainly want to stop them at the door. A firewall is the locked front gate, the arbiter of good traffic/bad traffic coming into and leaving the PC and it will block incoming connections from malicious IP addresses. However, there are ways malicious files and processes can bypass a firewall, such as an email with a malicious attachment, an infected USB stick, or a downloaded program that looks legitimate but is infected. The anti-malware component is the locked front door that will detect these files and stop them dead in their tracks. So, you really do need both layers of protection.
How does BullGuard’s Identify Protection keep customer’s personal information safe?
We protect you against identity theft in several ways. The most obvious one is by checking with credit rating agencies to assure no unauthorized accounts are opened in your name. We also look at outbound connections to ensure that when you are connected to your bank that you are connected to your bank’s legitimate site and not a phishing or malicious site which can steal your credentials and identity. To the untrained eye, the facsimile and authentic sites look completely identical, but BullGuard is able to identify and block them.
Furthermore, there exist forums within the dark web where cybercriminals engage in the illicit trade of stolen identities. Our ongoing monitoring involves scanning these forums for the presence of your social security number, credit card numbers, bank account numbers, and other sensitive information. This is conducted in order to determine if your identity has been compromised.
How does Game Booster improve the gaming experience?
We found that people were turning off their anti-virus programs during gameplay to maximize their computer’s performance. However, it left their PC unprotected, and if you’re anything like my kids, you’re playing games for inordinate stretches of time. Game Booster keeps the anti-virus program running but limits the amount of processing power it and other running applications use, so game playing gets the maximum possible computer power. What we found in testing is that even with the anti-virus protection, a system with Game Booster maximized game playing better than a system without it. So, we’re able to offer our customers the improved experience of gaming while adding the protection of BullGuard software.
What are some features of your Parental Control module? What “loopholes” have internet savvy kids used to bypass other Parental Control programs and how have you closed them?
Great question! Our parental controls module has a sophisticated set of controls allowing parents to set and enforce rules, but really it comes down to essentially 3 things:
- Controlling the time and use of a PC. Parents may be unaware that their child is on the computer until 3 AM. Now they can control how long a child can use the PC and to restrict internet usage and specific applications to certain times of the day. So, a parent can say, “OK, you can use the PC, but there’s no internet after 10 PM”, or “You can only play the following games within a certain time window”.
- Content filtering. Parents can restrict access by categories, such as adult content, gambling, hate speech or drug-related content. Additionally, applications such as violent games can be blacklisted, so they can’t be installed or run from the PC.
- Closing loopholes. A computer-savvy child can deactivate or even uninstall parental controls. Preventing deactivation is straightforward by requiring a password which is needed to change parental control settings. To prevent the software from being uninstalled, we recommend parents set their children up with a non-administrative account, so the child can do everything they need to do but are unable to uninstall the software. In the past, a really savvy child could download a VPN to access inappropriate content. With our software parents can blacklist the installation and running of VPNs, setting restraints in a way that is tamperproof.
What are zero-day threats and how does BullGuard protect against them?
A zero-day threat is a threat that has never been seen before, making it extremely dangerous as there is no known file signature to recognize and remedy.
Therefore, our behavioral engine (called a next-generation engine in the industry) also looks at behavioral characteristics. Is a file attempting to write to the registry, attempting encryption behavior, is it taking up an inordinate amount of memory or CPU? Did it try to access certain protected parts of the file system? If so, we immediately quarantine it and prevent it from executing. And not just on your machine, but on those of our millions of customers around the world.
We also gather vast amounts of data from honeypots we’ve set up and share samples with different vendors in the industry, so our very extensive machine infrastructure is continually learning to discriminate between the characteristics of good files vs. the characteristics of malicious files. This is how we stay one step ahead of zero-day threats.
Will having all these processes running in the background affect a computer’s speed or performance?
Not at all. The core behavior engine that is running locally on the PC is extremely lightweight concerning the resources it uses. The system I talked about that is looking at million, billions of data points across thousands of servers and virtual servers and the machine learning infrastructure that’s continually learning and improving and updating the models - all that heavy lifting is running on the cloud.
What products do you offer for cell phones and tablets?
Our products for cellphone and tablets include anti-malware, anti-phishing, performance optimization as well as device location, discovery, and locking. We have new products with additional capabilities coming in the very near future. We want to protect you however you are connected.


