
What’s the Difference Between DNS and IP Leaks? (& How to Stop It)
Due to privacy concerns and other pertinent reasons, some internet users prefer to use a VPN service to disguise their actual IP address and encrypt their data while surfing the web. However, all those goals can crumble if your personal data is leaking due to one security flaw or the other. There are the two major ways your VPN can leak your personal data or IP address: DNS leak and WebRTC (IP) leak.
What is DNS leak?
Likely without realizing it, you've interacted with the Domain Name System (DNS) if you've ever accessed the Internet. Essentially, the DNS operates like the Internet's version of a telephone directory. It keeps a record of domain names (like vpnmentor.com) and converts these into their respective numerical identifiers—Internet Protocol (IP) addresses—which are vital for finding resources online.
Domain names are for human consumption only, computers only understand numbers in the form of IP addresses (168.212.226.204) which may not be easy for humans to remember (hence the need for a DNS). Whenever you visit a site to request a web page, your computer contacts your ISP’s DNS server to request the website’s IP address. When using privacy service such as a VPN, your computer typically contacts your VPN server for DNS service instead of your ISP’s DNS.
How does it happen?
There is a security flaw that sometimes allows DNS requests to be forwarded to your ISP’s DNS servers, despite your use of a VPN service to attempt to conceal them. This flaw is known as a DNS leak. It results from an unencrypted DNS query sent by your computer outside the established VPN tunnel. This flaw stems from operating systems’ inherent lack of the concept of universal (collective) DNS. Each network interface can have its own DNS, and – under various circumstances – the system will send out DNS queries directly to your ISP or other third party servers (see diagram below) without respecting the default gateway and DNS settings of your VPN service, thereby causing a leak.
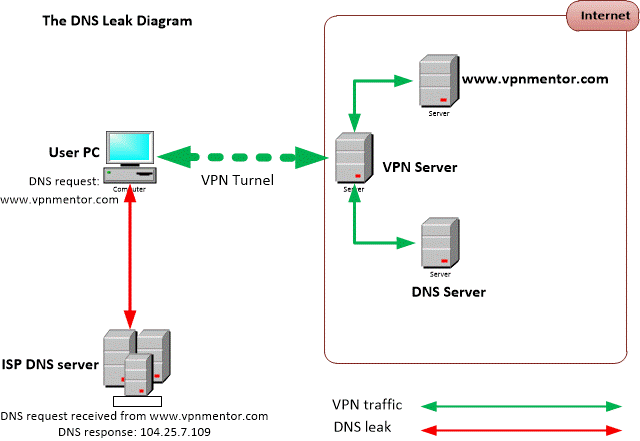 The flaw allows an ISP or eavesdropper to see what websites a user may be visiting. When you use a VPN and discover that your actual IP is leaking, it means your DNS requests are also being forwarded to your ISP other than to your VPN provider. Some ISPs even implement a technology called 'Transparent DNS proxy' that effectively forces your computer to use their DNS service for all DNS lookups even when you change your DNS settings to something other than theirs.
The flaw allows an ISP or eavesdropper to see what websites a user may be visiting. When you use a VPN and discover that your actual IP is leaking, it means your DNS requests are also being forwarded to your ISP other than to your VPN provider. Some ISPs even implement a technology called 'Transparent DNS proxy' that effectively forces your computer to use their DNS service for all DNS lookups even when you change your DNS settings to something other than theirs.
What is WebRTC (IP) leak?
In 2015, a security researcher, Daniel Roesler, posted a demonstration about a security flaw that allows an eavesdropper to take advantage of a special interface (API) program built into most web browsers called Web Real Time Communication (WebRTC) to reveal a user’s actual IP address, even if they’re connected to a VPN. WebRTC is usually used by computers in different networks for browser-to-browser communication, P2P file sharing, voice and video calling amongst others.
How does it happen?
All it takes is a few lines of code to trick WebRTC into revealing your true IP address via communications with an Internet-based server known as STUN (Session Traversal Utilities for NAT). The STUN server allows computers and devices in your internal network to find out their public IP (internet) addresses. VPNs also use STUN servers to translate your internal network address to a public internet address and vice-versa. To accomplish this, the STUN server maintains a database of both your VPN-based internet (IP) address and your local internal IP address during connectivity.
This leak has nothing to do with how secure your VPN is but it has everything to do with the vulnerability in the WebRTC itself within your browser. When WebRTC in your browser accepts queries from a STUN server, it sends back a response to the STUN server that shows both your private (internal network) and public (internet) IP address and other data.
The result of the requests, which is basically the user’s actual IP address, can then be accessed via a small program called JavaScript. The only requirement for this to work is WebRTC support in the browser and JavaScript program. If WebRTC is enabled on your browser, it'll normally accept STUN request and send a response to the STUN server.
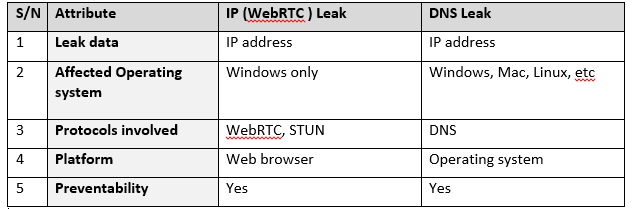
The bottom line here is that no system is perfect; once in a while flaws are uncovered. It’s therefore important that you use a reputable VPN provider that proactively responds to vulnerabilities when they occur. Ensure that you test your VPN against those leakages and take steps to fix them.
Your data is exposed to the websites you visit!
Your IP Address:
Your Location:
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 49% off.


