Report: Massive Instagram Click Farm Uncovered
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently uncovered a huge illicit Instagram click farm based somewhere in Central Asia and operating globally.
Click farms are usually based in developing countries with little to no data regulations, oversight, or enforcement. They create 1,000s of fake accounts to trawl Instagram, engaging with posts and profiles and clicking on paid advertisements. In doing so, they can inflate a person’s following, helping them earn income through advertising or sponsored posts on the app without appearing like spam.
However, we believe that the people (or person) behind this click farm instead created a highly automated process for managing 10,000s of proxy Instagram profiles based in countries worldwide, without needing much individual human input.
While a lot about this discovery remains a mystery, the click farm was clearly very successful.
Incident Summary
| Company targeted | |
| Company headquarters | California, USA |
| Type of Scam | Instagram click farm |
| Geographical scope | Global |
| Types of data exposed | Activity logs from the scam operation; data about fake profiles created |
| Potential impact | Fraud; Misinformation and fake news |
| Data storage format | Unsecured Elasticsearch |
Discovery and Investigation Timeline
- Database discovered: 21st September 2020
- Date Facebook contacted: 21st September 2020
- Database server closed*: 22nd September 2020
Sometimes, the extent of a data breach and the database's owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, it takes days of investigating before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the incident didn’t originate from Instagram.
The click farm is being operated by a 3rd party, possibly based in Kazakhstan or Armenia.
Early in our investigation, we contacted Facebook (the parent company of Instagram) to notify it of our discovery and present our initial findings.
In the meantime, we continued to investigate the database to learn more.
How the Scam Worked
The click farm appears to be run by a sophisticated operation that has built a highly automated process to create 10,000s of fake proxy accounts on Instagram. Each account had its own avatar, bio, and ‘persona’, appearing to join Instagram from all over the world.
Each fake account would then publish posts, view others’ posts, follow, react, and engage with profiles.
The click farm was also using proxy servers and IP addresses to hide its activity.
If 10,000s of new users started signing up to Instagram from a small town in rural Kazakhstan and behaving in almost identical ways, they would be quickly flagged as spam.
To get around this, every fake profile was matched with an IP address in a country that corresponded with its ‘persona.’
To demonstrate how to identify fake user accounts created by the click farm, we can use the Hebrew language.
For example, if the name on a Hebrew account is " "נועם פישמן" ("Noam Fishman") the email was " pyshmn.nv_m", which is the literal transliteration of Hebrew into Latin letters (without vowels). Hebrew is a language where vowels are implied most of the time, so here they used only the consonants of the name, which gave "Pyshmn Nv_m".
Another example is" צפורה" (Tziporah) gives Tspvrh (the sound O is written with the same letter that makes the sound V).
This suggests that the Hebrew accounts on the exposed database were set up by people who didn’t speak the language and are most likely inauthentic.
What We Discovered
Our research team uncovered a command and control server that appeared to be the hub for the entire operation.
The server contained data for 10,000s of Instagram profiles and actions being taken by the people running them:
- Instagram usernames and passwords
- Proxy IP addresses for each account
- Email address connected to Instagram accounts
- SMS verification codes
- Phone numbers used in the operations
By storing all this data in a single server, the click farm’s operations were completely centralized and controlled by a single entity.
This centralized model allowed anyone working at the farm to log into an account seemingly based anywhere in the world and immediately start taking various actions.
To operate the click farm, they also needed 1,000s of local SIM cards to receive verification codes for joining.
We believe this operation is being conducted from Central Asia. Many of the server's real IP addresses are from Kazakhstan and Armenia, along with the mobile phone operators used to receive SMS verification messages from Instagram.
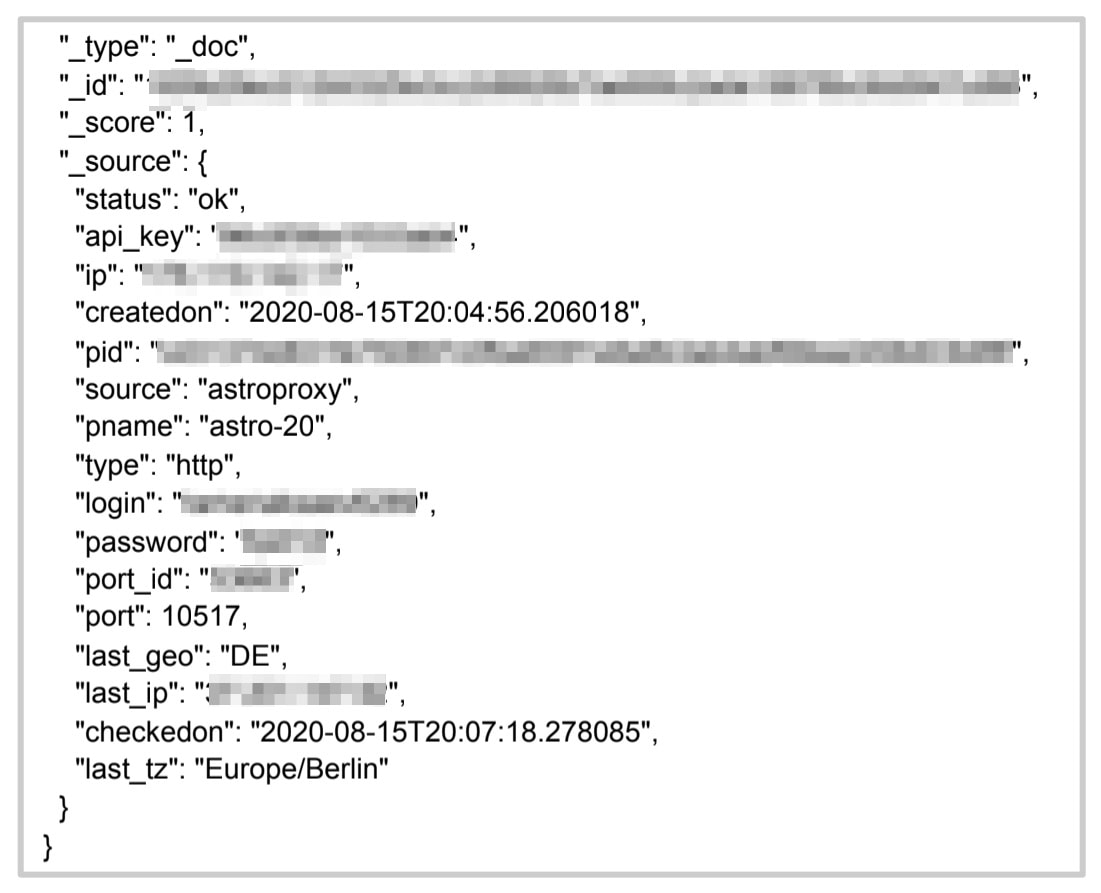 Data logs from the click farm's fake profiles
Data logs from the click farm's fake profiles
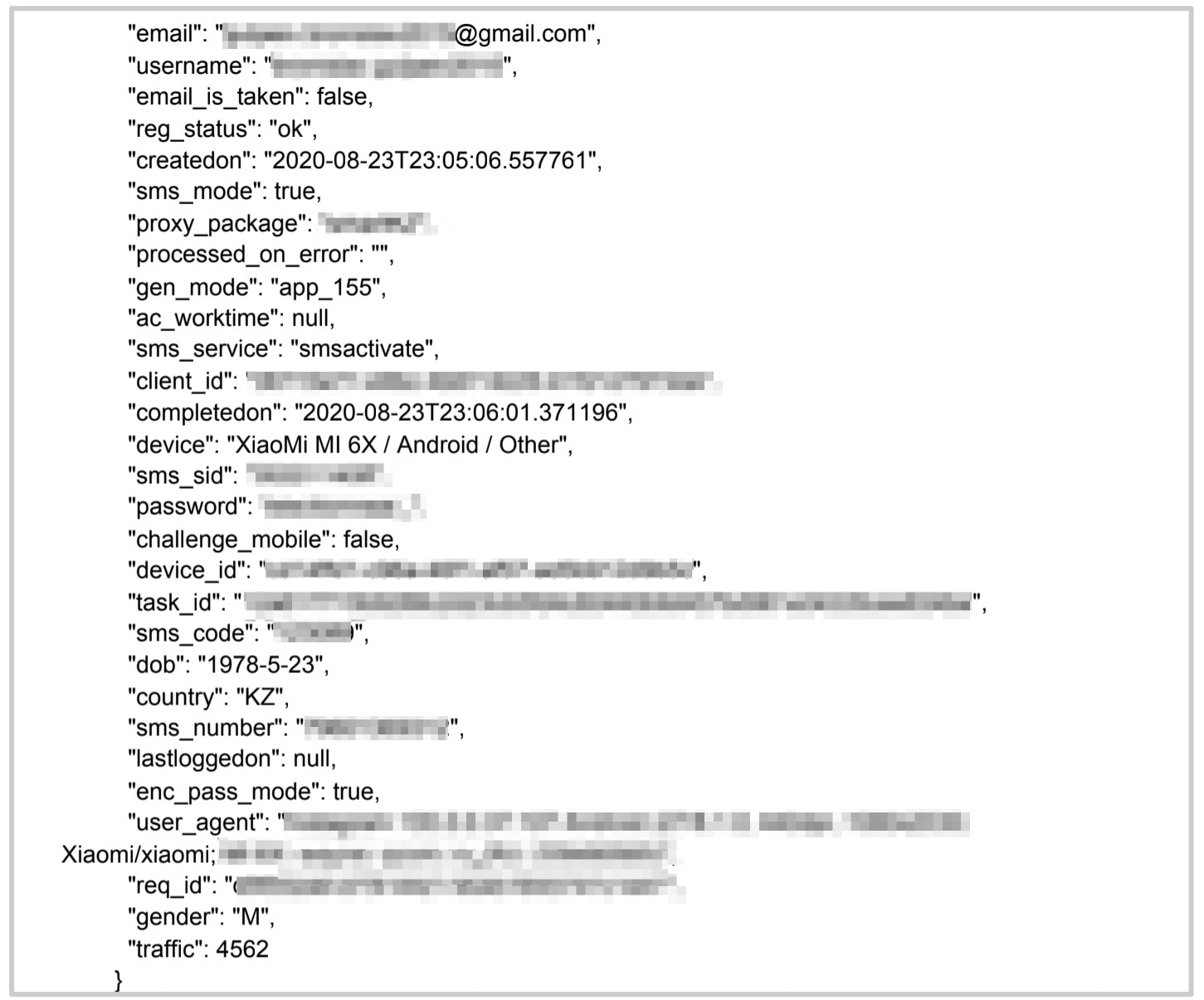 Data logs from the click farm's fake profiles
Data logs from the click farm's fake profiles
Potential Impact
Very little is known about the world of click farms and how they operate. However, we already know a couple of goals they commonly pursue for clients.
Fraud
Click farms are often paid by individuals or companies to inflate their followers and engagement. The people hiring click farms then use this to leverage sponsorship posts and other forms of income from the app.
In doing so, they're defrauding any company or 3rd party that pays them based on followers and engagement.
Misinformation and Fake News
Click farms are also used to spread fake news and misinformation.
There is plenty of evidence that this is already a widespread practice and a popular form of election interference, manipulation, and indirect attack on rivals by governments like Russia, China, Iran, and their allies.
Advice From the Experts
Facebook and Instagram can work to quickly remove this click farm's accounts from the Instagram app.
However, they may just be replaced with new ones.
Instagram users can help by reporting any accounts or activity they suspect to be spam or operating under false pretenses, and they may be taken down.
Fraudulent activities, misinformation, and click farms are widespread issues on widely used social networks like Instagram and Facebook. These companies have been grappling with these problems for years. However, by acquiring knowledge on how to identify these concerns, you can inform and create awareness within your own network.
Remember that a lot of what you see on social media has been manipulated in some way.
Awareness will reduce their influence, at least a little.
How and Why We Discovered the Database
The vpnMentor research team discovered the breach in this click farm as part of a huge mapping project.
Our researchers use port scanning technology to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access the click farm’s database because it was completely unsecured and unencrypted.
They were using an unsecured Elasticsearch database to store the data, which is ordinarily not designed for URL use. However, we were able to access it via a browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when our research uncovers issues that may impact their users. We reached out to Facebook to let them know about the scam and how many people had been affected.
These ethics also mean we carry a responsibility to the public. Instagram users must be aware of scams targeting them.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included scams targeting Spotify and Facebook users. We also revealed how a group of free VPNs recorded their users’ activity and exposed it in a massive data leak. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect the Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: December 9th 2020]