
Report: Spotify Targeted in Potential Fraud Scheme
Led by Noam Rotem and Ran Locar, vpnMentor’s research team has discovered a possible credential stuffing operation whose origins are unknown, but that affected some online users who also have Spotify accounts. Credential stuffing is a hacking technique that takes advantage of weak passwords that consumers use -- and often re-use -- online.
We unearthed an Elasticsearch database containing over 380 million records, including login credentials and other user data being validated against the Spotify service.
The origins of the database and how the fraudsters were targeting Spotify are both unknown. The hackers were possibly using login credentials stolen from another platform, app, or website and using them to access Spotify accounts.
Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users. We also helped the company isolate the issue and ensure its customers were safe from attack.
Incident Summary
| Company targeted | Spotify |
| Company Headquarters | Stockholm, Sweden |
| Industry | Music Streaming and Media |
| Size of data in gigabytes and number of records | 72 GB; 380+ million records |
| Suspected no. of users | 300,000 - 350,000 |
| Date range/timeline | Unknown |
| Geographical scope | Unknown |
| Types of data exposed | Email addresses; login credentials (usernames and passwords) |
| Potential impact | Identity Theft & Fraud; Scams, Phishing and Malware; Account Abuse. Credential Stuffing |
| Data storage format | Open and unencrypted Elasticsearch server; exposed MySQL servers |
Company Profile
Spotify is probably the most popular music and audio media streaming service in the world, with over 299 million active monthly users in 2020.
The company was founded in Stockholm, Sweden, in 2006, and the first version of the Spotify app launched two years later, with 60 million songs available for streaming, and has grown rapidly in the years since.
Spotify went public in April 2018, skipping a traditional IPO and making a direct listing on the New York Stock Exchange. The company’s stock price has recently surged, doubling in value since March 2020, most likely due to increased engagement from listeners stuck at home while under lockdown.
Discovery and Investigation Timeline
- Date discovered: July 3rd, 2020 (reviewed on July 9th)
- Date Spotify contacted: July 9th, 2020
- Date of Response: July 9th, 2020
- Date of Action: Between July 10th and July 21st
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregard our research, or play down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
What We Discovered
In this case, the incident didn’t originate from Spotify. The exposed database belonged to a 3rd party that was using it to store Spotify login credentials. These credentials were most likely obtained illegally or potentially leaked from other sources that were repurposed for credential stuffing attacks against Spotify.
Early in our investigation, we contacted Spotify to present our initial findings. Together, we concluded that whoever owned the database had probably obtained the login credentials from an external site and used them on Spotify accounts.
This is a common tactic used by cybercriminals to access private accounts on popular platforms like Spotify, and something the company -- like most online businesses -- has dealt with in the past, given the pervasive use of weak passwords by so many consumers online. Companies cannot prevent this from occurring since they do not control the passwords that consumers use (and re-use) online. But they can play a role by helping users regain control of their accounts and promoting safer password practices by users, which Spotify did in this case.
In response to our inquiry, Spotify initiated a ‘rolling reset’ of passwords for all users affected. As a result, the information on the database would be voided and become useless.
What We Found in the Database
The database in question contained over 72 GB of data, totaling 380+ million individual records, and was hosted on an unsecured Elasticsearch server.
The origins of the database and how the fraudsters were targeting Spotify are both unknown. The hackers were possibly using login credentials stolen from another platform, app, or website, and using them to access Spotify accounts.
Examples of Data Exposed
Many of the database records contained information about potential Spotify users, such as their Personally Identifiable Information (PII) data and Spotify login credentials.
This included:
- Account usernames and passwords verified on Spotify
- Email addresses
- Countries of residence
There were also numerous server IP addresses exposed in the leak. However, these were most likely from proxy servers belonging to the operators of the network on which the database was hosted.
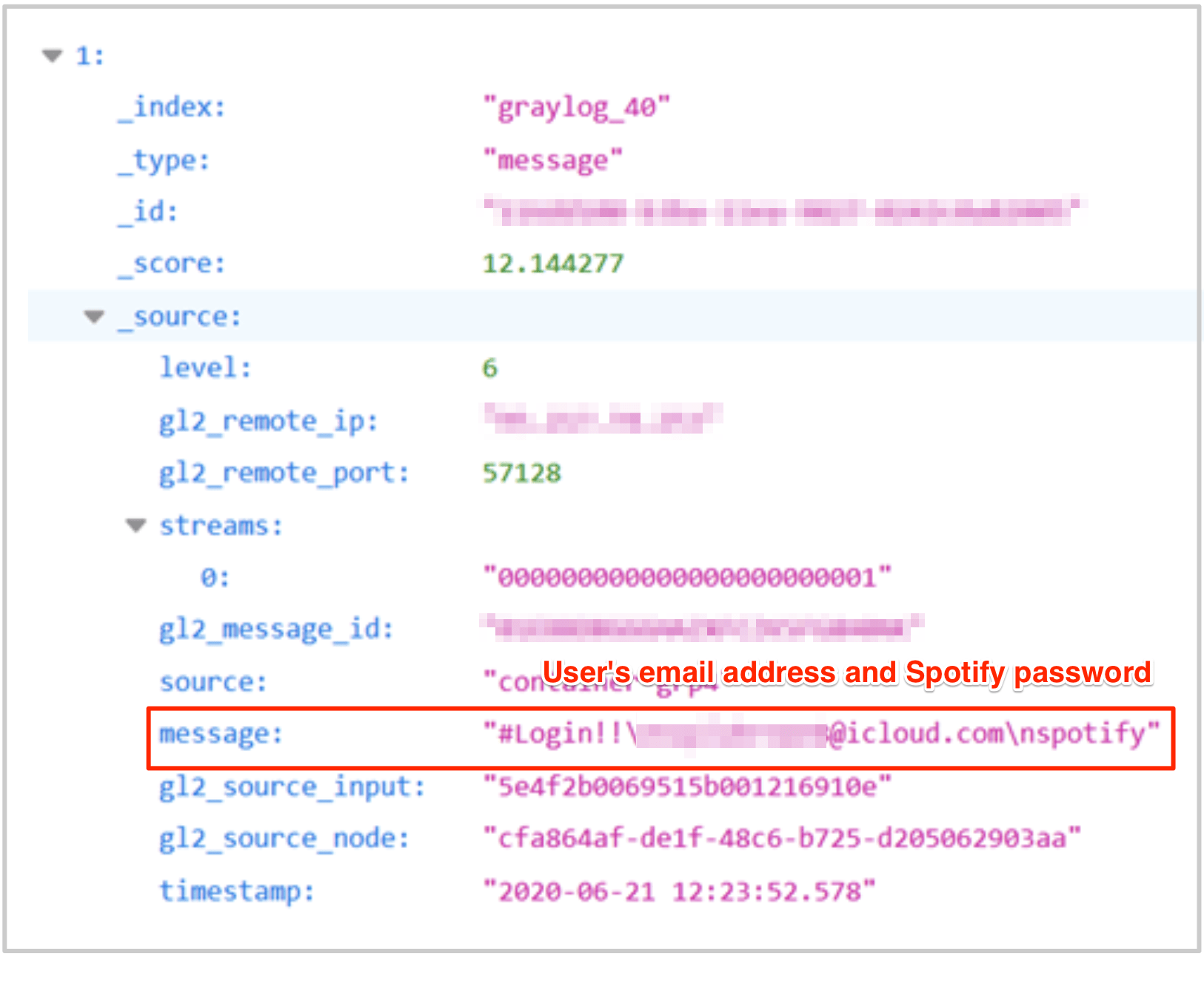
The following screenshot demonstrates how someone’s PII data and login credentials were exposed. In this case, their Spotify account password was simply “spotify”.
Potential Impacts of the Incident
The exposed database could be used in many criminal schemes, not just by the fraudsters who built it, but also by any malicious hackers who found the database, as we did.
Any of these parties could use the PII data exposed to identify Spotify users through their social media accounts, and more.
With this information, criminals could pursue several activities to defraud and hack Spotify users.
Financial Fraud and Identity Theft
Fraudsters could use the exposed emails and names from the leak to identify users across other platforms and social media accounts. With this information, they could build complex profiles of users worldwide and target them for numerous forms of financial fraud and identity theft.
Phishing Scams and Malware
Fraudsters could also use the contact information to directly target the exposed users with phishing emails, tricking them into providing sensitive data like credit card details, or clicking a fake link embedded with malware. By imitating Spotify in these emails, they could be very successful in such a campaign.
Account Abuse
Fraudsters could use the stolen credentials to access a user’s account and take advantage of digital services paid for by the original user (e.g., Spotify's Premium service tier).
External Account Takeover
Many affected users are probably reusing usernames, passwords, and email addresses across numerous platforms, apps, and private online accounts.
With one set of PII data and login credentials, the fraudsters could target other popular platforms for hacking by logging in to accounts with the same details. This is a pervasive form of fraud and is often very successful.
Advice from the Experts
If you were contacted by Spotify to change your password, we suggest you follow the instructions provided. If you reused your Spotify password on any other accounts, change it immediately to protect them from hacking. We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.
You can also use our password meter to ensure your current passwords are strong enough.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
In the course of a comprehensive web mapping endeavor, the research team at vpnMentor came across the database. Our investigators implement port scanning to study distinct IP blocks and probe various systems for any weaknesses or vulnerabilities. Each discovered weakness is then meticulously inspected for potential data leakage.
Our team was able to access this database because it was completely unsecured and unencrypted.
The fraudsters were using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when our research uncovers issues that may impact its users. In this case, we reached out to Spotify to inform it of a potential fraud targeting its users.
These ethics also mean we carry a responsibility to the public. Spotify users must be aware of attempts to expose sensitive data, even if it didn’t originate from within Spotify.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of millions of free VPN users around the world. We also revealed that a group of dating apps compromised the privacy and security of their users. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: 23.11.2020]


