
Report: Major Pharmaceutical Company Exposes Private Data of US Prescription Drug Users
We can reveal that Big Pharma giant Pfizer has been leaking the private medical data of 100s of prescription drug users in the USA, in a significant data breach discovered by Noam Rotem, Ran Locar, and vpnMentor’s cybersecurity research team.
The exposed data related to conversations between Pfizer’s automated customer support software and people using its prescription pharmaceutical drugs, including Lyrica, Chantix, Viagra, and cancer treatments Ibrance and Aromasin.
By not protecting this data, Pfizer compromised the privacy and security of people using its medications, many of them already vulnerable due to poor health.
Data Breach Summary
| Company | Pfizer |
| Headquarters | New York, USA |
| Industry | Pharmaceuticals |
| Suspected no. of files | 100s, and growing |
| No. of people exposed | 100s, and growing |
| Date range/timeline | Oct ‘18 - Jul ‘20 |
| Geographical scope | USA |
| Types of data exposed | Phone call transcripts; PII data |
| Potential impact | Fraud; phishing |
| Data storage format | Google Cloud Storage bucket |
Company Profile
Founded in 1849, Pfizer is one of the biggest pharmaceutical companies in the world.
The company operates across the globe, developing medicines in a wide range of consumer healthcare and prescription medicine specialties. These medicinal products include patented, brand-name pharmaceuticals and generic products.
Publicly listed on the New York Stock Exchange, Pfizer generated $51.8 billion in revenue in 2019.
Timeline of Discovery and Owner Reaction
- Date discovered: 9th of July 2020
- Date vendors contacted: 13th of July 2020
- Date of 2nd contact attempt (if relevant): 19th of July 2020
- Date of 3rd contact attempt to Pfizer: 22nd of September 2020/li>
- Date of Reply from Pfizer: 22nd of September 2020
- Date of Action: 23rd of September 2020
Sometimes, the extent of a data breach and the owner of the data is obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the exposed files were stored on a misconfigured Google Cloud Storage bucket. Google Cloud Storage is different from Google Drive, providing service specifications for enterprise platforms and corporate customers.
Initially, we suspected the misconfigured bucket to be related to just one of the medication brands exposed. However, upon further investigation, we found files and entries connected to various brands owned by Pfizer.
Eventually, our team concluded the bucket most likely belonged to the company’s US Drug Safety Unit (DSU).
Once we had concluded our investigation, we reached out to Pfizer to present our findings. It took two months, but eventually, we received a reply from the company.
When they finally replied, all we received was the following statement: "From the URL you gave, I failed to see how it is important Pfizer data (or even an important data at all)." This was a surprising response from one of the biggest companies in the world.
We then shared a file with a sample of their customers’ PII data that we found in the Google bucket.
After this, they finally secured the bucket, but never replied to our messages again.
Example of Entries in the Google Bucket
The misconfigured bucket contained transcripts between users of various Pfizer drugs and the company’s interactive voice response (IVR) customer support software.
The folder containing the transcripts was named ‘escalations,’ suggesting they were part of an automated internal process managing customer queries and complaints.
We also reviewed transcripts in which the conversation was ‘escalated’ to human customer support agents. It appeared these agents were registered nurses representing Pfizer in matters relating to its pharmaceutical brands.
In total, there were 100s of transcripts from individuals across the USA, with more being uploaded during our investigation. Each transcript exposed numerous forms of Personal Identifiable Information (PII) data, including:
- Full names
- Home addresses
- Email addresses
- Phone numbers
- Partial details of health and medical status
The transcripts related to numerous products manufactured and sold by Pfizer, including many medicines used to treat various forms of cancer.
The following are just three examples of Pfizer products mentioned in the transcripts:
- Aromasin: an anti-estrogen used to fight breast cancer.
- Chantix: treatment for nicotine addiction.
- Depo-Medrol: a medicine used in a huge number of treatments for skins diseases, certain cancers, asthma, and much more.
- Ibrance: used in treatment for breast cancer.
- Lyrica: medication for epilepsy, neuropathic pain, fibromyalgia, restless leg syndrome, and generalized anxiety disorder.
- Premarin: Primarily used in menopausal hormone therapy.
- Viagra: Used to treat erectile dysfunction and pulmonary arterial hypertension.
Some of the transcripts were related to conversations about Advil, a common anti-inflammatory and pain relief medicine manufactured by Pfizer in a joint venture with GlaxoSmithKline.
The screenshots below show various forms of PII data exposed in different conversations:
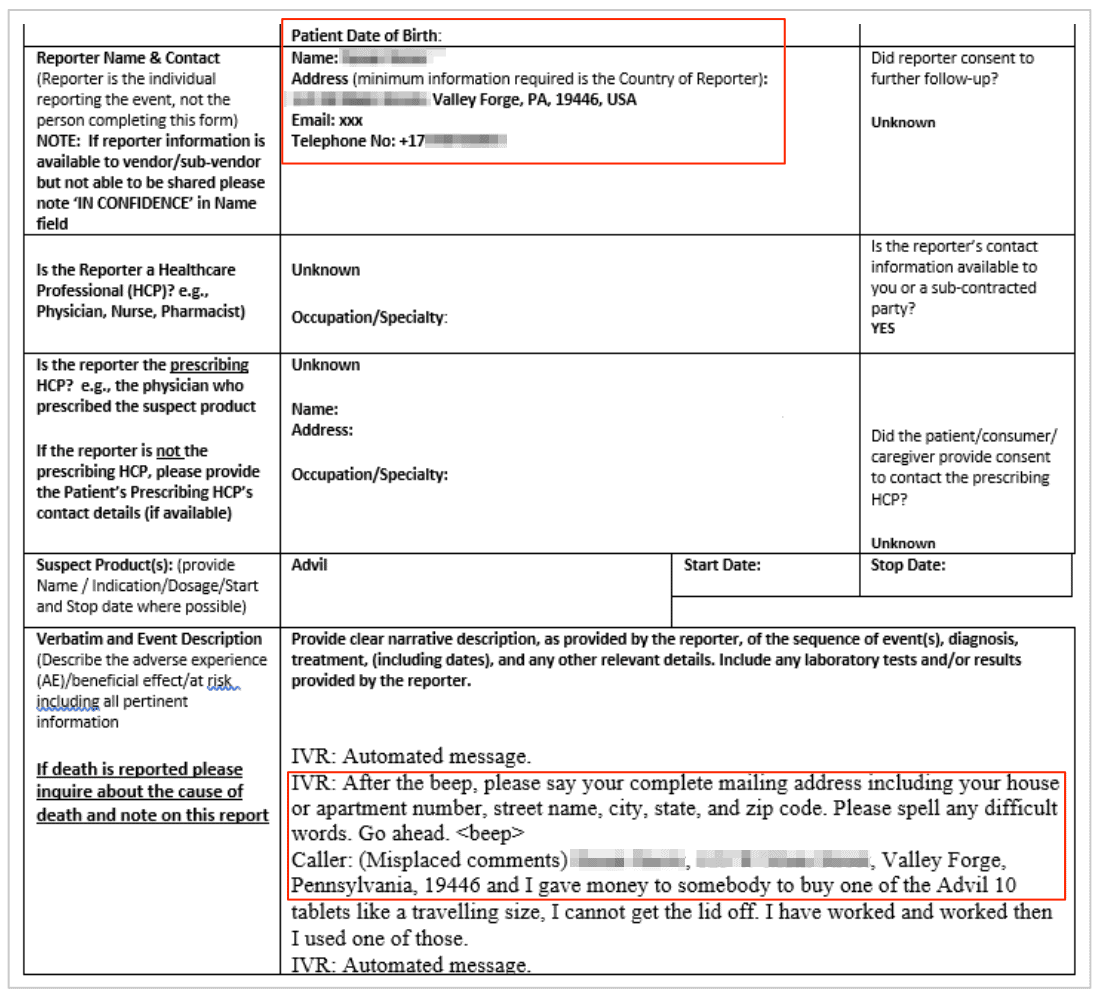
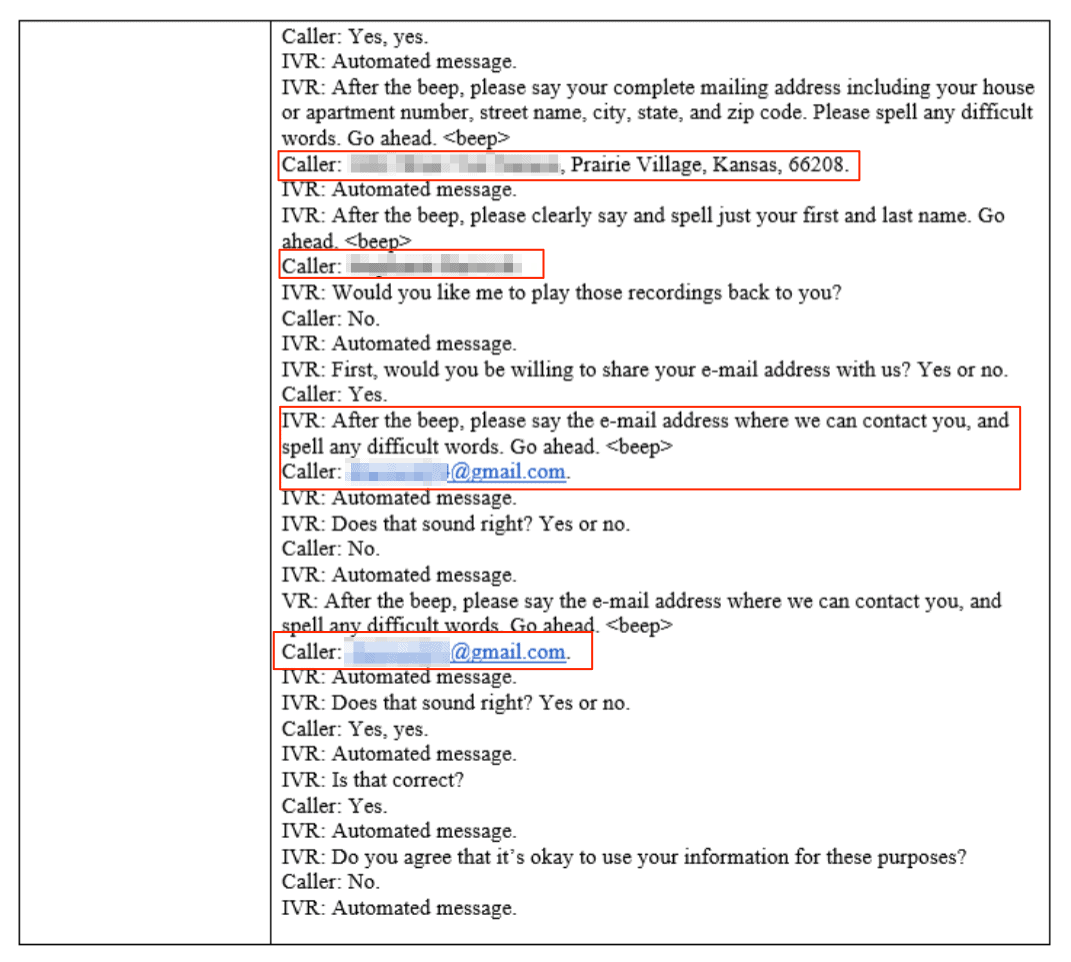
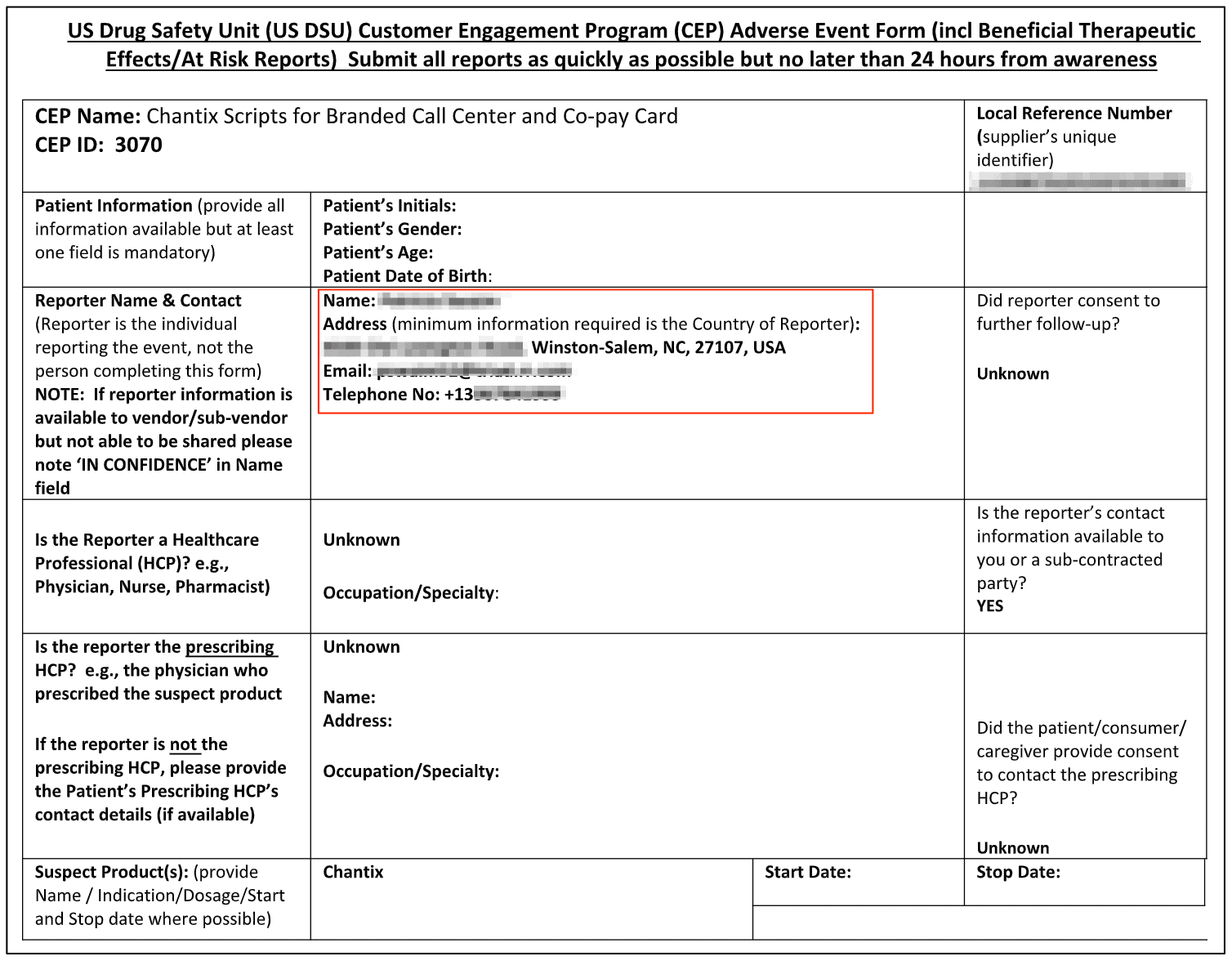
Pharmaceutical companies hold a great deal of responsibility to keep the data of their customers secure and private.
Not only is this a moral responsibility. It’s the law.
By exposing these transcripts to the public, Pfizer committed a basic lapse in data security and a breach of confidentiality, with significant implications for the wellbeing of the people exposed.
Data Breach Impact
Had malicious or criminal hackers accessed the data stored on Pfizer's Google Cloud bucket, they could have exploited it in numerous ways, targeting drug users in various fraudulent schemes.
Impact On Pfizer Customers
Using the PII data revealed in the transcripts, combined with details of medicine prescriptions and usage, hackers could target those exposed with highly effective phishing campaigns.
In a phishing campaign, cybercriminals create fraudulent emails imitating real companies hoping to trick victims into providing sensitive data (usually financial) or clicking a link embedded with malicious software, like malware and ransomware.
Hackers could easily trick victims by appearing as Pfizer’s customer support department and referencing the conversations taking place in the transcripts.
For example, many people were enquiring about prescription refills and other queries. Such circumstances give cybercriminals a great opportunity to pose as Pfizer and request card details in order to proceed with the refills. They could also use this to get additional information about a patient, such as their home address.
If a victim clicked just one dangerous link in an email, they could infect their device with a virus — whether a smartphone, laptop, or tablet — and expose the entire network through which they connect to the internet.
As a result, anyone on that network would be indirectly exposed to the viral attack, with devastating consequences.
If cybercriminals succeeded in tricking a victim into providing additional PII data, they could use this to pursue various forms of fraud, including total identity theft. In doing so, they could destroy a person’s financial wellbeing and create tremendous difficulty in their personal lives.
Furthermore, there’s a high probability the people exposed in these transcripts are experiencing ill health, physically and emotionally. One of the medicines referenced, Lyrica, used to treat anxiety disorders, while others, such as Ibrance and Aromasin, are used in the treatment of cancer.
At the time of the data breach, Coronavirus was still surging across the USA. If cybercriminals had successfully robbed from or defrauded someone taking medication for anxiety in any way, the potential impact on their mental health is immeasurable and impossible to understate.
Impact on Pfizer
By not securing the data exposed in this breach, Pfizer has made itself vulnerable to legal issues.
If any of the individuals affected were residents of California, the company falls within the jurisdiction of the state’s CCPA data privacy laws. As a result, Pfizer will be expected to take specific measures or face investigation and potential fines for not adequately securing private consumer data relating to its products.
More seriously, while Pfizer isn’t liable under US HIPAA laws (which dictate how healthcare companies manage customer data), it still broke plenty of rules and best practices for handling sensitive medical data in the US.
Editor's Note: We'd like to thank Dissent Doe for further looking into Pfizer's HIPAA status, and helping us define the type of violation in question. For more information about HIPAA violations, read DataBreaches.net's in-depth article.
And while this was a relatively small data leak, it could still have damaged many people's lives, and Pfizer may face serious questions about their broader data privacy protections as a result.
Furthermore, the company risks considerable negative publicity from news media covering the breach. The pharmaceutical industry is the most unpopular business sector in the USA, consistently ranked at the bottom of public opinion.
Any story that intensifies distrust and hostility of a Big Pharma company like Pfizer could go viral and create a storm of negative attention.
Advice from the Experts
Pfizer could have easily avoided exposing its customers’ data if it had taken some simple security measures to protect its customers’ data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open Bucket
It's crucial to understand that Google Cloud Storage isn't inherently flawed with the issue of open, publicly accessible buckets. Rather, such occurrences typically stem from a mistake made by the bucket owner. Google offers comprehensive guidance to its users to ensure their buckets are properly secured and maintained as private.
In the case of Pfizer, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow Google Cloud Storage access and authentication best practices.
- Add more layers of protection to their bucket to further restrict who can access it from every point of entry.
- Refrain from logging sensitive, personal user data unless necessary. If logging this data is required, it should be encrypted or at least masked in accordance with the highest security standards.
For Pfizer Customers
If you’re a customer of Pfizer and are concerned about how this breach might impact you, contact the company directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Pfizer’s data as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being exposed.
Our team was able to access this bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, and it's usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Pfizer, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. Pfizer users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing 1,000s of American domestic abuse victims to danger. We also revealed that a hugely popular gambling app was leaking millions of users’ data from around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect the Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: 20.10.2020 ]


