
BrandProtect – Detecting, Assessing and Mitigating Online Threats – Outside the Firewall
- Please tell us a little bit about your background and current position at BrandProtect.
- What are the biggest security risks to companies today?
- What is an External Threat?
- How does BrandProtect monitor social media sites?
- What is the FFIEC (Federal Financial Institutions Examination Council) Guidance on Social Media Risk?
- How does bankSMART™ address the unique needs of financial institutions?
- Typically, posts on social media and user review sites can only be taken down by the original poster. How do you arrange to have posts removed?
Outside the Firewall. It may sound like the next book in The Game of Thrones series, but it is very, very real and very today. It categorizes the ever-growing number of online threats which circumvent our firewalls. These threats can even exist on social media sites anywhere in the world, and we wouldn’t be any wiser. That’s where BrandProtect’s proprietary threat assessment software and trained professionals come in.
Please tell us a little bit about your background and current position at BrandProtect.
Over the years, I have held several different positions in the cyber world, starting as an IT systems administrator fresh out of school. About 11 years ago, I began work at Brand Protect as a junior incident response analyst handling incidents primarily outside the firewall. I worked my way up and have been a director for 5 or 6 years now. My responsibilities include managing the team that identifies new online trends and threats to our clients and getting those threats removed from the internet.
What are the biggest security risks to companies today?
The primary risk to corporations is ransomware. A subset of malware, ransomware essentially encrypts an infected system and then demands payment, typically in the form of cryptocurrency, to unlock the system and all the files. Additionally, most forms of ransomware will send out feelers across the network and could, in fact, infect all the systems on that network. Considering the price that is demanded to unlock these systems, this can be a very costly proposition.
We also see a lot of what we call BEC or Business Email Compromise attacks. These are social engineering type of attacks where a perpetrator will research the employees of a company on LinkedIn and other social media. With this information, they can ascertain a quasi-reporting structure within that company. After registering a domain name very similar to the targeted organization, they will choose a CEO or CFO and create what looks to be their email address. They then identify a low-level person in accounting or HR, and impersonating that high-ranking executive, will reach out to them in an email with a sense of urgency attached - “I’m on a business trip, I need this wire transfer done immediately." Of course, the junior person believing the CEO is making the request will transfer money to the perpetrators, typically in the amount of five, six, even seven figures. I read about one such attack today where Lazio, an Italian soccer club, fell victim to a BEC attack and ultimately ended up transferring 2 million Euros to a perpetrator thinking they were transferring it to one of their junior squads.
What is an External Threat?
External threats are anything that occurs outside of the firewall, so that can be any number of things, including those we just discussed. We originally started handling external threats in the form of phishing attacks that were targeting our client’s customers. That expanded into identifying cybercriminals who leverage our client’s brand to get unsuspecting customers to download and install their malware. We then expanded even further and handle threats to our client’s branding on social media and customer review sites.
For example, we had a customer facing an issue with a white nationalist website claiming their bank financed terrorism. And another white nationalist group was urging people to bank at a specific bank, which was also our customer. While these accusations and associations were false, they obviously posed a huge risk to our customer’s branding and brand positioning.
On social media we deal with risks including threats targeted towards executives. These could be people tweeting out CEOs’ addresses or phone numbers and urging people to go protest at their homes, which are physical security risks. We’ve also found newly hired employees tweeting or publicly posting things like “Thank God the background check didn’t find my drug arrest.” We are then able to report this to our customers, making sure that these people are ultimately not hired. Additionally, we’ve discovered fraudulent posts by people trying to recruit money mules.
We also look at mobile apps associated with our customers, not just at the official sources, but hundreds of third-party app stores, and then we define the risk. If clicking the link to Bank ABC ‘s mobile app brings a user to the google play or the iTunes store, that is not a huge security risk because the end user is ultimately installing the legitimate app from an official source.
It’s when the mobile app is available for direct download from these third-party stores that it poses a possible security risk. This mobile app may be straight up malware or a modified version of the legitimate app which may contain infected keyloggers or “Man in the Middle” attacks. So, there are all types of possibilities around mobile app security that we look at and mitigate for our customers.
We also monitor for brandjacking which includes unauthorized use of our client’s branding. We typically see a third-party organization create an online store that is a duplicate of our customer’s official website. They will change the name and logo a bit but use their assets, text, and images, all of which are copyrighted and owned by the brand.
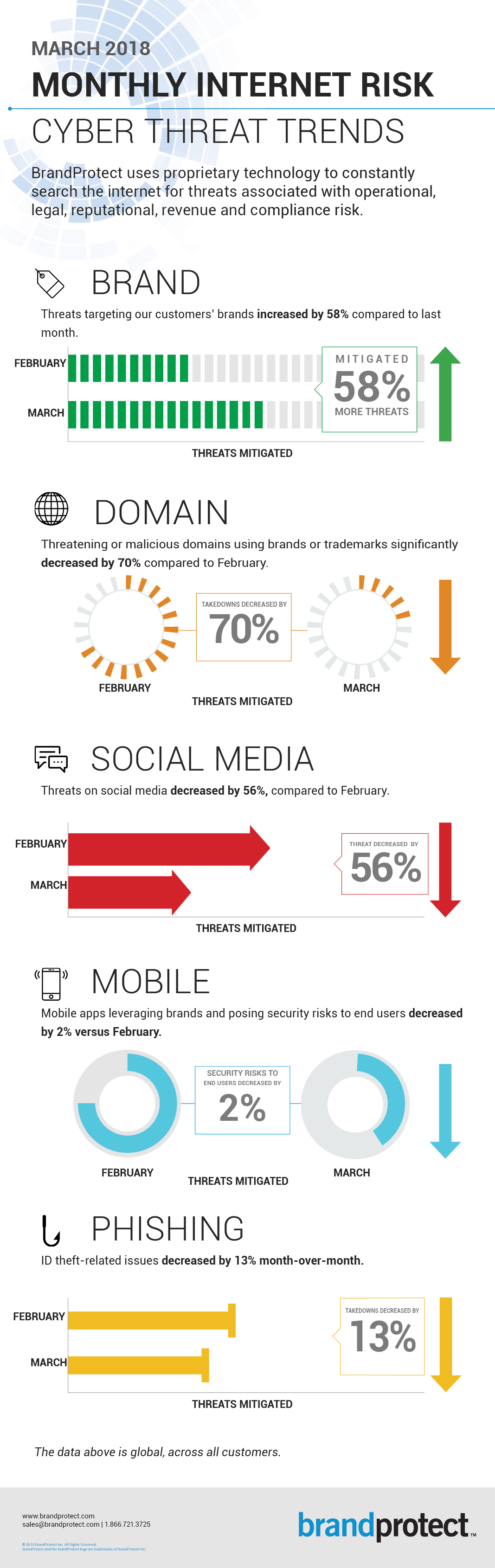
How does BrandProtect monitor social media sites?
Our exclusive platform for searching, crawling, and assessing threats scans both the public internet and the deep web, using a distinct set of keywords tailored for each customer. Moreover, we utilize data sets from different sectors, including financial institutions, healthcare, retail, and more. Based on the client's requirements, we incorporate these industry-specific terms into social media searches. This practice enhances detection accuracy and significantly reduces the number of false positives.
All the results come into our system and are handed over to our experienced threat analysts for review to pick out the stuff that is useful. By further categorizing this data, we can determine the type of risk our customer faces as a result of each specific issue. Our account managers then perform a second level validation. Once that is completed, the information is turned over to the customer for review and action where necessary. Our unique and thorough process ensures that our clients see only the incidents that matter to their business.
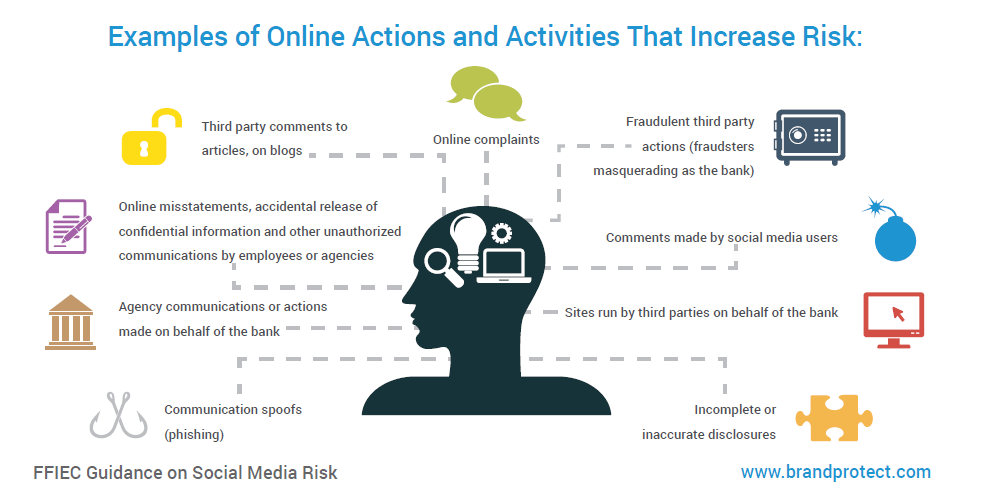
What is the FFIEC (Federal Financial Institutions Examination Council) Guidance on Social Media Risk?
Content created and shared on social media can have a damaging effect on financial institutions and their customers. Therefore, the FFIEC has stated that organizations doing business online need to have insight into what is being publicly posted about them. “I had a bad experience at this bank” or “I love my bank because…” is not a risky type of discussion. However, “The bank branch at 123 Main Street leaves their front door unlocked half an hour after closing time.” is obviously very dangerous. Additionally, there are risks of document and data leakage. We have seen employees posting customer information or advertising customer data for sale.
How does bankSMART™ address the unique needs of financial institutions?
We apply a list of industry terms relevant to financial institutions to the initial search results to provide a relevancy score. This second level of keyword matching facilitates validation of that data, not just by the BrandProtect analysts, but also by our customers.
bankSMART™ is actually a culmination of all our services, social media monitoring, mobile app service, domain service, and anti-phishing service. It supplies financial institutions with a comprehensive solution, including any takedowns of content that we find. This ensures that all their bases are covered, not just with regards to the FFIEC social media guidelines, but with regards to any existing legislation, especially as it concerns identity theft prevention and phishing detection.

All financial institutions are required to have a plan to address identity theft attempts, and we’re able to provide that comprehensive solution in a centralized location. All our data is kept in perpetuity so if the auditors come knocking five years down the road, we have it all archived, even if that institution is not a current customer.
Typically, posts on social media and user review sites can only be taken down by the original poster. How do you arrange to have posts removed?
Unflattering or critical posts do not come under the possible takedown process. Someone is certainly entitled to say, “I don’t like this bank because they wouldn’t give me a loan.” However, posting “I don’t like this bank because they wouldn’t give me a loan because I’m black,” is making an assertion about the motives behind the company which is obviously untrue in most cases. In these instances, our advice to our customers is to reach out to the poster and offer to clarify the situation for them. Ultimately, factually incorrect, damaging information left online can have a significant impact on our customer’s stock prices or industry share. We have contacts at hundreds of social media platforms around the world. So, if the original poster refuses to correct the information, our connection will make sure the post is reviewed, and if it meets the criteria the platform deems relevant for removal or blocking, they will do so.


