
Report: Leading Internet Security Company Exposes Customers to Fraud and Attack From Hackers
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a data breach belonging to SSL247, a reseller of internet security products.
The breach originated from a misconfigured Amazon Web Services S3 bucket, exposing private files belonging to the company. Many of these files included detailed information about customers purchasing security products through SSL247.
This data breach represented a lapse in the most fundamental data security practices by SSL247, a well-regarded company trusted by many high-profile corporations and government bodies.
Not only does this raise questions about the legitimacy of the company’s broader internet security practices, but it also exposed potentially 100,000s of people to fraud and attack, while compromising the security of people who depend on SSL certificates and similar products to protect their identity.
Exactly what SSL247 is trying to prevent.
Data Breach Summary
| Company | SSL247 |
| Headquarters | London, United Kingdom |
| Industry | Internet security |
| Size of data in gigabytes | 158 GB |
| Suspected no. of files | 465,000 |
| No. of people exposed | Up to 350,000 |
| Date range/timeline | 2012-2020 |
| Geographical scope | S. America, Middle East, N. America, Europe, and Africa |
| Types of data exposed | Invoices; customer lists; promotional and sales material |
| Potential impact | Corporate mail fraud; compromised anonymity and security; breach of trust |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
Founded in 2003, SSL247 is based in London, with offices in France and operating in 14 international markets. The company has a global reach across much of South America, the Middle East, North America, Europe, and Africa.
Billed as ‘Europe’s Leading Web Security Consultancy Firm,’ SSL247 started as a reseller of SSL certificates.
Over the years, it has branched out to provide products and consultancy services for a wide range of web security solutions, including security audits, penetration tests, social engineering tests, compliance, physical security and network products, and much more.
SSL247 is well regarded globally within the web security industry, winning many awards and working in partnership with industry leaders like Symantec, Globalsign, Qualys, Thales e-Security, and Norton.
The company is also trusted by many multinational corporations, including some of the biggest companies in the world:
- Casio
- Motorola
- Xerox
- Thomas Cook
- T-Mobile
- JPMorgan
- Ford
- Yamaha
- Siemens
- ThyssenKrupp
- Sega
Many government bodies and global institutions also rely on SSL247:
- The government of Ontario, Canada
- USDA
- UNESCO
- University of Cambridge
- Greenpeace
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the exposed records were stored on a misconfigured Amazon Web Services (AWS) S3 bucket, an increasingly popular form of cloud storage. The S3 bucket was tagged with ‘ssl247’ in its name, and our team was quickly able to confirm SSL247 as its owner.
Upon doing so, we reached out to the company with the results of our investigation and offered our assistance closing the breach.
Rather than address the vulnerability or the potential of a data breach, SSL247 refused to accept our attempt at a responsible disclosure and a senior representative from the company sent the following single-sentence reply:
“I very much doubt it.”
While we’re used to companies denying our conclusions, this is the first time somebody has officially refused to even hear about our findings. Usually, they would just ignore us and not reply to our initial emails.
For such a well-regarded company within the internet security industry to react in this way is surprising and disheartening.
With this in mind, we also contacted AWS directly to present our findings to them. A few days later, the data breach was closed.
- Date discovered: 5th May 2020
- Date vendors contacted: 6th May 2020
- Date of Response: 7th May 2020
- Date AWS contacted: 7th May 2020
- Date of Action: 11th May 2020
Example of Data Entries
The S3 bucket contained approximately 465,000 files dating as far back as 2012. Due to misconfigured permissions and privacy settings, it was completely open and accessible to the public.
It appears SSL247 was using the S3 bucket to store various files and documents relating to its customers. These included:
- Invoices
- Purchase orders
- Account documents
- Customer lists in CSV format
Each of these documents exposed various forms of Personally Identifiable Information (PII) data of private individuals and companies using SSL247’s services. We estimate up to 350,000 people and businesses in total.
The PII data exposed included:
- Full names
- Email addresses
- Contact phone numbers
- Personal and business addresses
- Company details
- Profile photos
- SSL247 account information (i.e., account ID, start dates, products purchased, and more)
- Credit filings and financial data

Example: SSL247 customer list exposing PII data
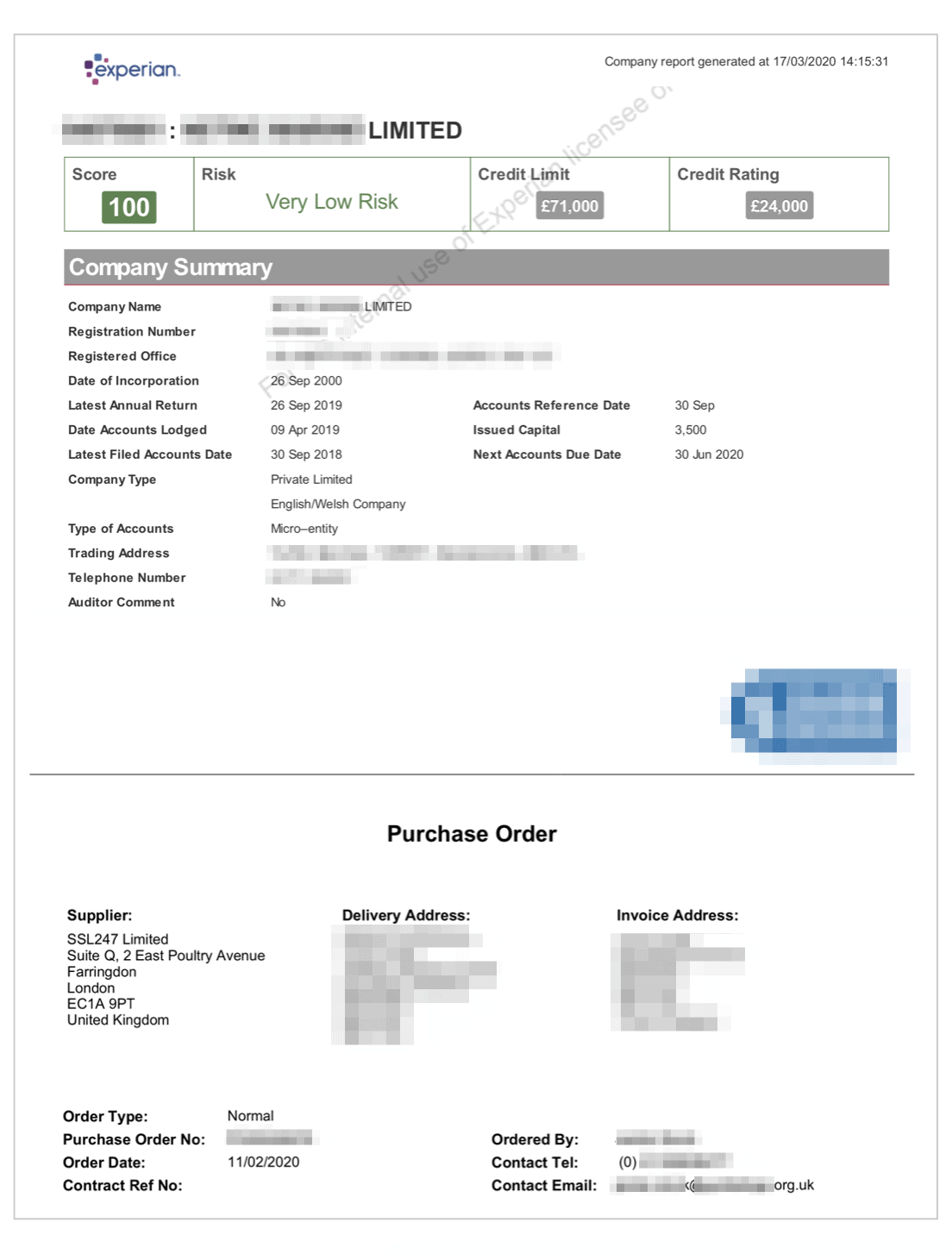
Example: Credit report for a UK-based NGO
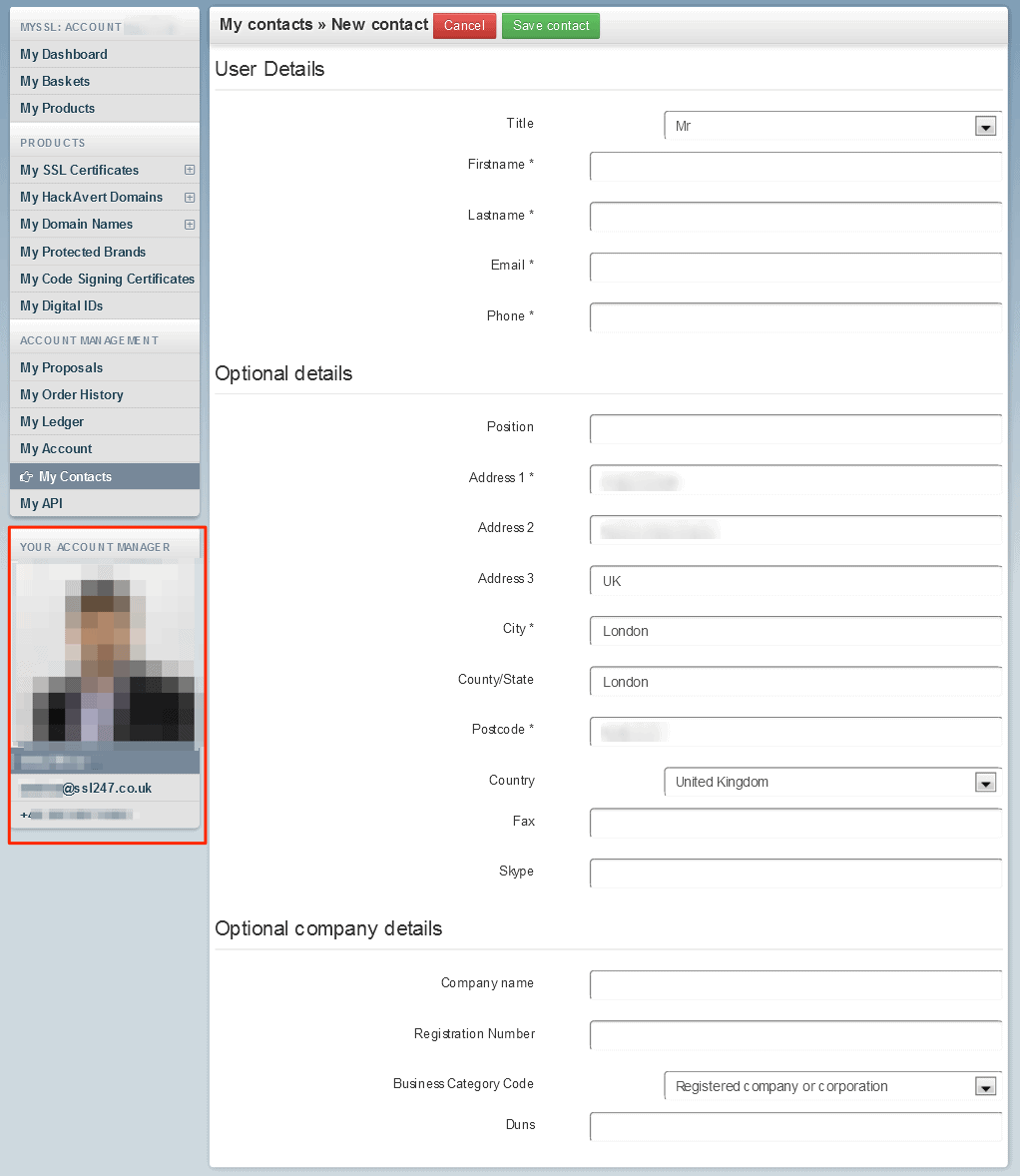
Example: Screenshot from an SSL247 account dashboard, exposing one of their employees’ PII
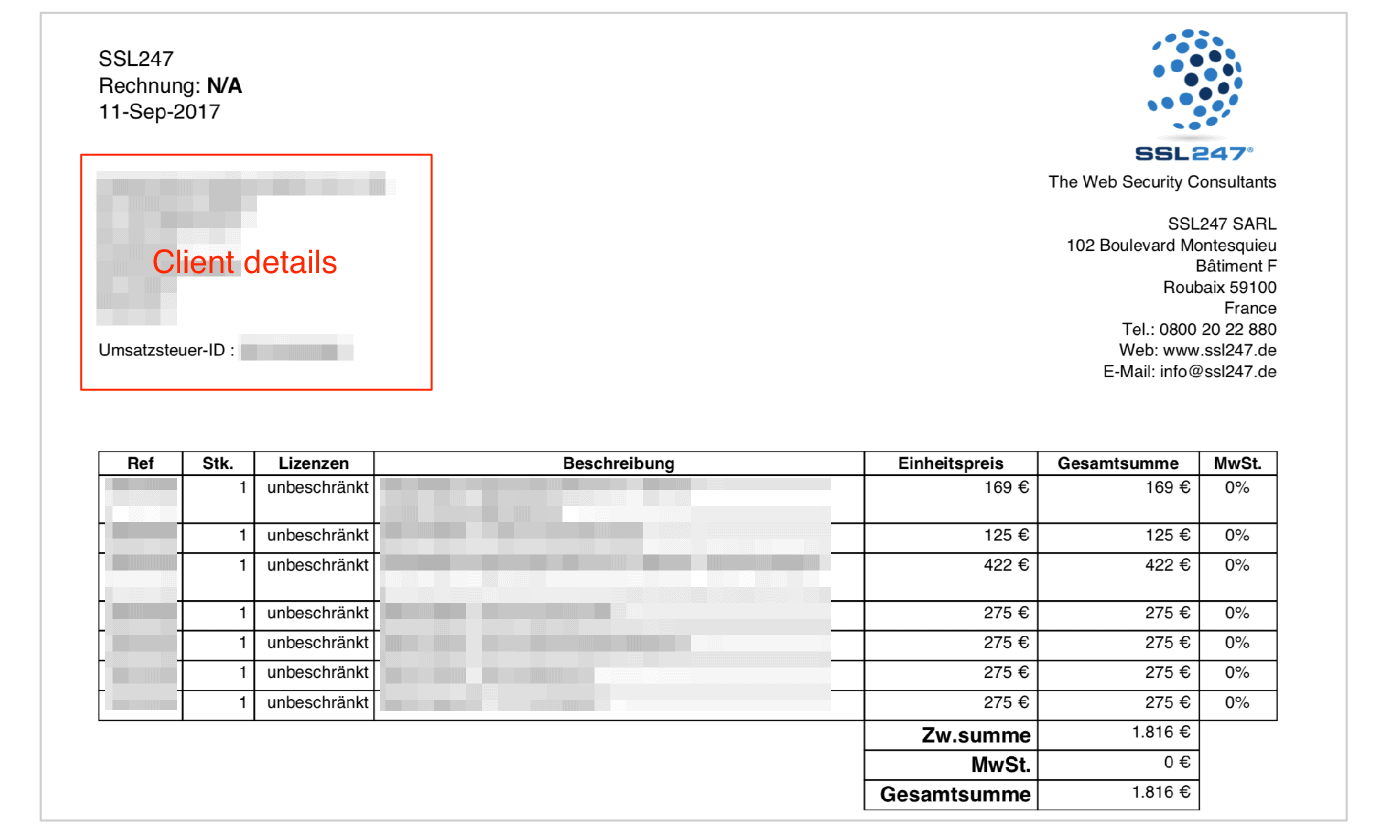
Example: Client invoice detailing products purchased through SSL247, exposing the entity behind the domain
Alongside these incredibly sensitive records, the S3 bucket also contained files related to marketing and promotion for SSL247’s services and products. There were also some records associated with the company’s internal operations and finances.
Many of these files would have been publicly available, and any risk from them being exposed minimal. However, the fact that they were stored on an unsecured S3 bucket alongside significantly more sensitive records may further damage SSL247’s reputation as experts in web security.
Altogether, the existence of the misconfigured S3 bucket not only discredits SSL247’s claim to be an industry leader, but it could have also compromised the safety of 100,000s of people.
Data Breach Impact
For a company dedicated to internet privacy to expose such sensitive data belonging to a large group of people is incredibly negligent. Anonymity is the core function of products like SSL certificates, so by breaching this anonymity and exposing the identities of its customers, SSL247 has failed in its most basic function as a business.
By not securing this data, SSL247 compromised the safety and security of its customers and jeopardized its future as a respected company in the internet security industry.
For SSL247 Customers
Malicious hackers could have used the private customer files stored within the misconfigured S3 bucket in a variety of ways to implement numerous criminal schemes.
Using the details of individual customers, they could create effective phishing emails impersonating SSL247 to commit corporate mail fraud, e.g., posing as SSL247 and sending their customers an invoice with the hacker’s bank account number. They could also trick victims into providing credit card details and other sensitive, valuable information used to steal from them.
The same emails could be used to embed malware, spyware, and other malicious software on an SSL247 customer's devices.
Hackers could use the same methods against employees in businesses and organizations purchasing products through SSL247, with a much more devastating impact.
Aside from fraud and viral attacks, there could be a greater risk to the security of people purchasing domain anonymity through SSL247. When buying an SSL certificate for your domain, you expect that nobody can connect the domain directly back to you. This privacy is an invaluable asset for many, including activists and political dissidents.
Through SSL247’s misconfigured bucket, the ownership of 100,000s of domains was now publicly available. Had this information been exposed to the general public, malicious actors and oppressive governments could potentially use it to target domain owners for harassment - or worse.
The negative consequences of exposing such information cannot be understated.
For SSL247
Had this information been obtained by criminal hackers and used to defraud or attack SSL247’s customers, it could have theoretically led to the collapse of the company.
This is what happened to Dutch certificate authority DigiNotar in 2011. After a massive hack that used fraudulent DigiNotar certificates to initiate man-in-the-middle attacks, the company lost the trust of every web browser using their certificates, was taken over by the Dutch government, and went bankrupt.
All in the space of a few short months.
While Diginotar’s collapse was the result of high-level hacking, SSL247 has put itself at risk due to incompetence - which is actually worse.
The company could also still face numerous other issues, even without criminal hackers using this information to attack its customers.
SSL247 risks losing trust from users and damage to its reputation as a result of the breach. Storing such sensitive, private customer data in a publicly accessible S3 bucket is a fundamental lapse in data security for any company, but especially one reselling security products.
People may question SSL247’s credentials as a result, and look to other providers when purchasing such products.
As the company has many customers in the EU, with offices in France, it falls with the jurisdiction of GDPR. It is required to report any data breaches within its network and may face audits and investigations from regulatory bodies as a result.
SSL247’s partners may also be concerned by this breach, demand answers for how it happened, and require the company to provide proof there are no other vulnerabilities in its network. If it can’t provide such information, it may lose valuable corporate relationships.
Finally, competitors will be scrutinizing this breach for an opportunity to exploit it.
SSL247 operates in a highly competitive industry in which any flaw or lapse in security has severe consequences for a brand. That it failed to keep its customer data safe, its competitors can take advantage of this fact and use it for negative publicity against the brand, and even take their customers.
All of these outcomes would inflict varying degrees of damage on SSL247, threatening its revenue and the medium term or long term health of the company.
Advice from the Experts
SSL247 could have easily avoided exposing its customers’ data if it had taken some basic security measures to protect its customers' data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of SSL247, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For SSL247 Customers
If you’re a customer of SSL247 and are concerned about how this breach might impact you, contact the company directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
During an extensive web mapping initiative, the research team at vpnMentor uncovered a breach within SSL247's S3 bucket. Our team of investigators applies port scanning to investigate specific IP blocks, assessing various systems for potential weaknesses or vulnerabilities. Each identified weakness is then meticulously scrutinized for any indications of data exposure.
Our team was able to access the S3 bucket because it was misconfigured and completely unsecured.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to SSL247, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. SSL247 users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
Introducing The Leak Box
To ensure our mission has the most significant impact possible, we’ve also built The Leak Box.
Hosted on the dark web, the Leak Box allows ethical hackers to anonymously report any data breach they find online. We then verify and report any submission deemed a legitimate threat to the public’s safety.
We never sell, store, or expose any information we encounter during our security research. This includes any information reported to us via The Leak Box.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 1,000s of American energy sector workers. We also revealed that an Israeli phone network compromised the privacy and security of its customers. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 17.06.2020]


