
Report: Massive Data Leak Exposes US Energy Sector to Cyberattack
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a breached database belonging to American software company RigUp.
RigUp is a labor marketplace and services provider built for the US energy sector, with clients across the country.
The breached database was huge, containing over 70,000 private files belonging to companies and individuals using RigUp’s platform.
Had it been discovered by malicious hackers, or leaked to the general public, the impact on RigUp, its clients, and 1,000s of energy workers across the USA could have been devastating.
Company Profile
Rigup was founded in 2014 as a jobs marketplace specifically for the USA energy industry, connecting independent contractors with work placements and projects in companies across the USA.
It quickly grew to provide additional services covering many aspects of energy company operations. RigUp is now considered the largest online marketplace and labor provider in the US energy sector, and in 2019 secured $300 million of investment, based on a $1.9 billion valuation.
The leaking database represents a major lapse in basic data security protocols for a company of this size.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the exposed database was an Amazon Web Services (AWS) S3 bucket, labeled “ru”, and many of the files contained within included RigUp’s name. Based on this, we were quickly able to confirm the company as the database’s owner.
We then reached out to both RigUp and AWS to report the vulnerability, and offer our assistance.
While it took them some time to reply, we must commend RigUp for responding positively to our disclosure, especially at a time when it must be experiencing considerable disruption, due to the coronavirus pandemic. The company took full responsibility for the leak - a rare occurrence - and guaranteed a root cause analysis would be conducted.
- Date discovered: 10th March 2020
- Date vendors contacted: 16th March and 2nd April 2020
- Date of contact attempt with AWS: 18th and 30th March 2020
- Date of Response: 8th April 2020
- Date of Action: 8th April 2020
Example of Entries in the Database
The exposed S3 bucket was a live database, with over 76,000 files exposed, amounting to over 100GB of data and dating from July 2018 to March 2020.
It appears the database was a ‘file dump’ used by RigUp to store various kinds of files belonging to its clients, contractors, job seekers, and candidates for employment.
The files related to human resources, recruitment, and a wide range of other business activities, belonging to unrelated companies and private workers from across the USA.
The human resources files being leaked included:
- Employee and candidate resumes
- Personal photos, including some private family photos
- Paperwork and IDs related to insurance policies and plans
- Professional IDs
- Profile photos, including US military personnel
- Scans of professional certificates in different fields
These files contained considerable Personally Identifiable Information (PII) data for the people affected, including:
- Full contact details: names, address, phone numbers, home addresses
- Social Security information
- Dates of birth
- Insurance policy and tax numbers
- Personal photos
- Further information relating to education, professional experience, personal lives
The following screenshots, all taken from files within the database, clearly demonstrate the seriousness of this leak.
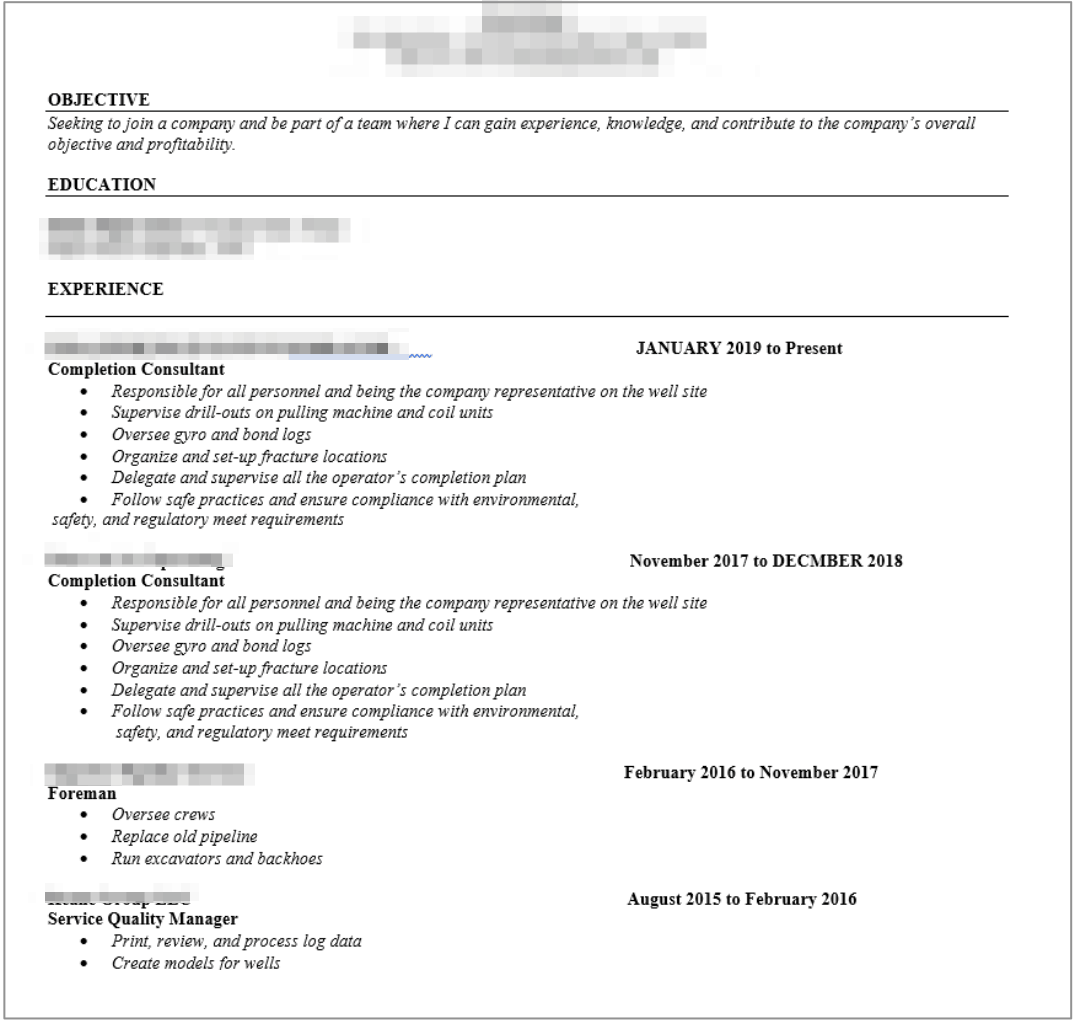
Example #1: The resume of a job applicant, revealing numerous PII data and other details

Example #2: Profile photo of an unknown individual uploaded to the database

Example #3: A personal family photo found in the database
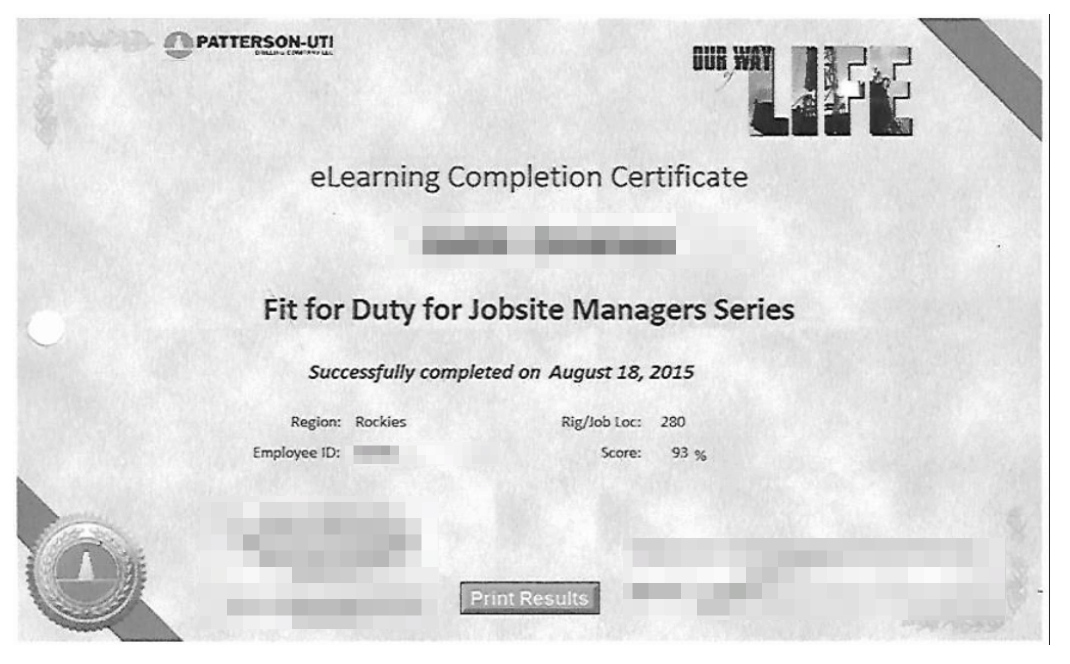
Example #3: A scan of a professional certificate revealing personal data of the graduate
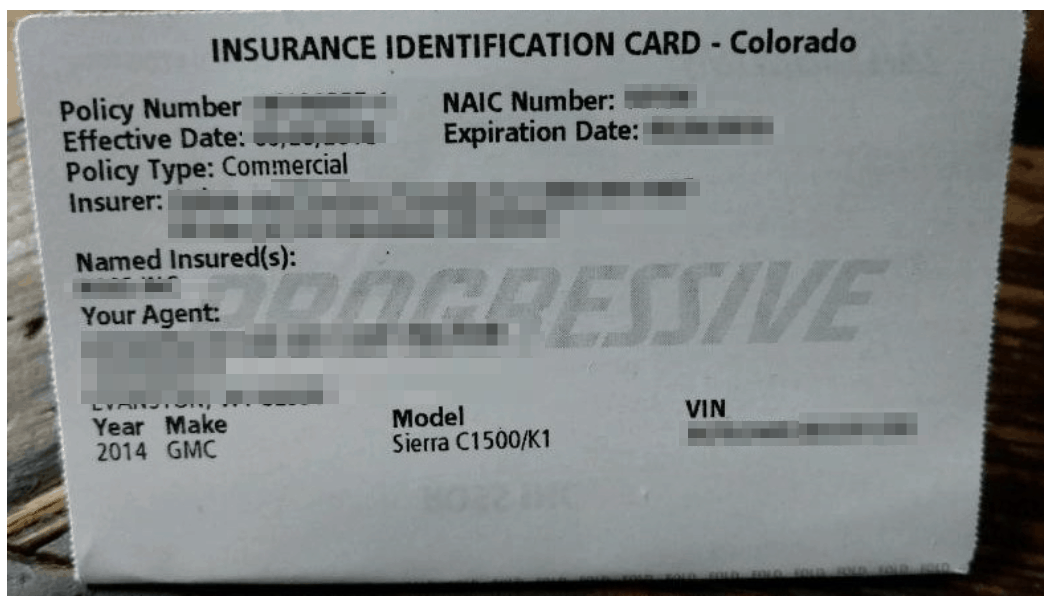
Example #4: ID card for individual motor insurance policy
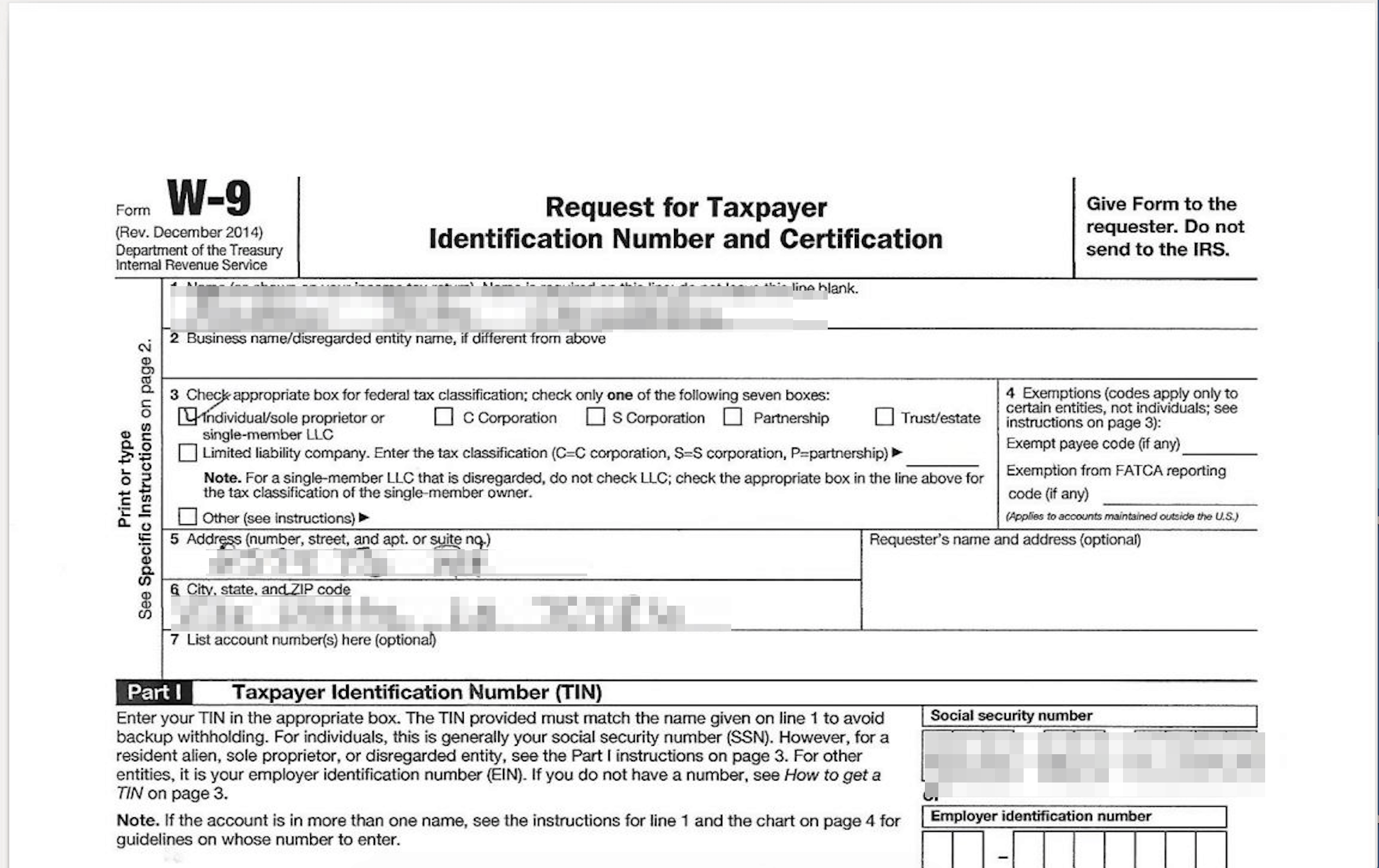
Example #5: A tax form exposes highly sensitive PII

Example #6: A certificate from the US government
Alongside human resources files, the database contained internal records relating to the business operations, projects, and corporate relationships of many energy firms. These included:
- Project proposals and applications
- Project outlines
- Technical drawings for drilling equipment
- Corporate insurance documents
The following screenshots are examples of the company files being leaked.
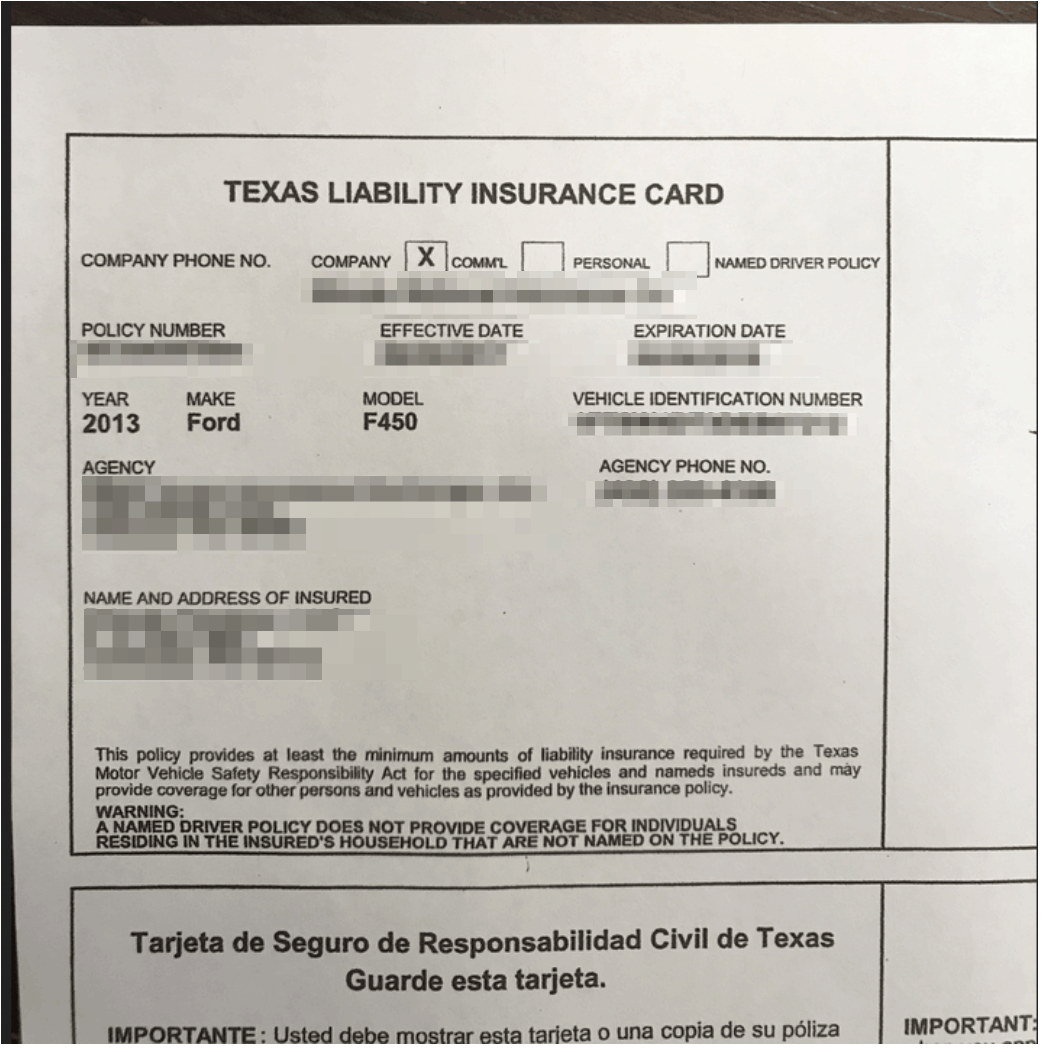
Example #7: Details of a corporate insurance policy
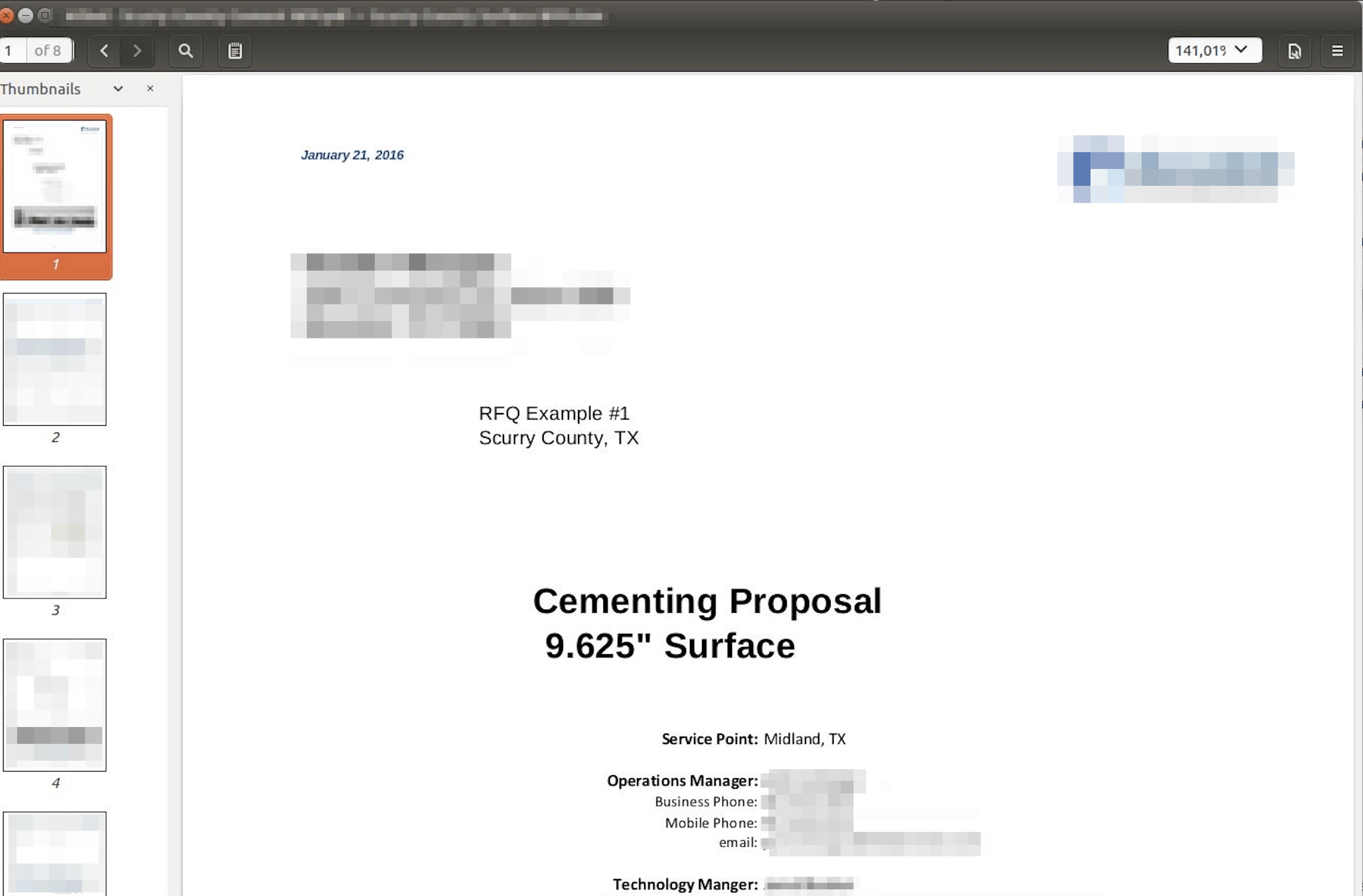
Example #8: One of many project proposals included in the database, also revealing PII of individuals involved
Data Breach Impact
By not securing its database, RigUp - a billion-dollar company - compromised the safety and security of the 1,000s of people across the USA.
Had malicious hackers discovered this database, it would have been an absolute goldmine for various fraud schemes and criminal attacks against everyone involved.
For People Exposed
The files in RigUp’s database contained PII data for 1,000s of energy sector employees, contractors, job seekers, and private individuals working within the industry.
All of this data could be used in a variety of fraudulent activities.
For example, with access to a person’s Social Security, tax details, and insurance policy information, hackers could pursue insurance fraud, tax fraud, and wholesale identity theft.
Hackers could also go a step further. Knowing the work status and personal histories or people, along with their contact details, they could create highly effective phishing campaigns.
Phishing campaigns involve sending a victim fraudulent emails imitating a legitimate business, bank, or government body and tricking them into any of the following:
- Sharing additional sensitive information that could be used to defraud them further.
- Providing details or login credentials for private online accounts, such as bank accounts.
- Clicking a link that embeds spyware and other malicious software on their devices.
In fact, a single phishing email could potentially combine all three forms of attack.
Many people across the USA are now facing huge uncertainty in their employment as a result of the Coronavirus pandemic. Millions of people have been ordered to stay at home, while businesses across the country shut down.
At this time, RigUp may see a significant increase in users, as people use their labor marketplace and recruitment services to look for alternative employment. Simultaneously, the global energy sector is facing massive disruption due to the ongoing price war between Russia and Saudi Arabia, and its impact on oil prices and the fracking industry.
As a result, the number of people potentially impacted by a leak from RigUp's website would increase exponentially.
Furthermore, many of these new users will be facing economic hardship and uncertainty in the coming months. The consequences of a successful hack or cyberattack on such peoples' security and livelihood would be dire.
For The Companies
The companies affected by this leak would be vulnerable to many of the same frauds and attacks listed above.
Of course, on a much bigger scale and with potentially far worse outcomes.
Private companies are increasingly vulnerable to attack from hackers, and often it's smaller, less-known companies who face the brunt of these attacks. They’re seen as easy targets, due to smaller cybersec budgets and fewer resources.
If hackers accessed the private internal files of RigUp’s clients, they could easily target those companies for fraud, phishing campaigns, and attacks with malware, spyware, ransomware, etc.
Doing so could cripple a company financially and put their employees’ jobs at risk.
The companies affected face other dangers.
Many of the files on the database related to construction and energy contracts between various parties. Having these leaked could jeopardize a project if a third party was uncomfortable having the details publicly accessible.
Lastly, if a competitor accessed files belonging to an exposed company, they could undermine it through negative press, undercutting their prices for a project, and numerous other dishonest but effective actions.
For RigUp
Considering the potential impact of this leak on RigUp’s clients and users, the company is also vulnerable.
It risks the loss of business and revenue if individuals and corporations within the US energy sector no longer trust its data security practices. They may look to alternatives or take other actions that impact RigUp’s market share.
As it is very likely that this leak affected companies and individuals in California, this leak falls within the jurisdiction of the state’s CCPA data privacy law. As a result, RigUp may face investigation and scrutiny from California’s legislature, along with other concerned parties.
Whatever the outcome for RigUp, it will need to be proactive and transparent in how it resolves any concerns over this leak and its broader data security practices.
Advice from the Experts
RigUp could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In this case, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For The People Exposed
If you’re concerned about how this breach might impact you, contact RigUp directly to find out what steps they’re taking.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
During a comprehensive web mapping initiative, the vpnMentor research team detected a breach in RigUp's database. Our investigative experts utilize port scanning to scrutinize distinct IP blocks and assess various systems for potential vulnerabilities or weaknesses. They subsequently probe each of these weaknesses for potential data leaks.
Our team was able to access this database because it was completely unsecured and unencrypted.
When we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to RigUp, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. RigUp users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the travel plans and personal details of American military personnel around the world. We also revealed that popular app PhotoSquared compromised the privacy and security of 100,000s of its users in the USA. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 08.04.2020]


