
Report: Cloud Backup Provider Exposes Customer Data in Massive Leak
Led by Noam Rotem and Ran Locar, vpnMentor's research team recently discovered a breached database belonging to Cloud backup provider SOS Online Backup. With over 135 million records, this was a huge breach. It exposed significant metadata related to user accounts on SOS Online Backup and the structure of their cloud services. The breached database represented a serious lapse in data security by a company that prides itself on industry-leading privacy and security for its customers. Had malicious hackers discovered it, the consequences for both SOS Online Backup and its customers would have been dire.
SOS Online Backup Company Profile
Based in the US, SOS Online Backup is a secure cloud-based backup provider, offering personal and business packages to customers around the world. They claim to be a "multi-awarding" provider and "The World's Most Secure Online Backup" cloud service. SOS Online Backup's marketing and website emphasize 100% data privacy, safety and security across all devices as their USP and standout feature against competitors. They have 12 data centers around the world in the US, Canada, Australia, United Kingdom, India, Ukraine, and South Africa.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
In this case, the team discovered the database in November. However, it was some time before they could fully investigate it and learn what it contained. We analyzed the database on December 9th, and contacted SOS Online Backup the next day. While we didn't receive a reply from the company, the breach was closed around December 19th.
- Discovered by our system: November
- Date vendors contacted: 10/12
- Date of 2nd contact attempt (if relevant): 17/12
- Date of Action: Approx. 19/12
Example of Entries in the Database
The exposed database contained over 135 million records, totaling almost 70GB of metadata related to user accounts on SOS Online Backup. This included structural, reference, descriptive, and administrative metadata covering many aspects of SOS Online Backup's cloud services. Aside from metadata relating to SOS Online Backup, the database also contained personally identifiable information (PII) data of their customers. This included:
- Full Name
- Email address
- Phone number
- Internal company details (corporate customers)
- Account usernames
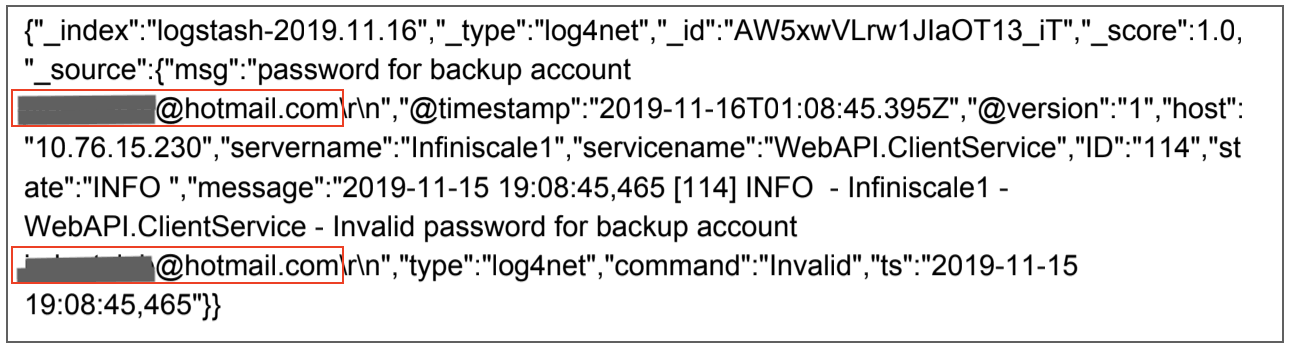
Due to the size of the database, there's potential it affected SOS Online Backup users around the world, impacting their entire user base. In the first examples, users' email addresses have been exposed:
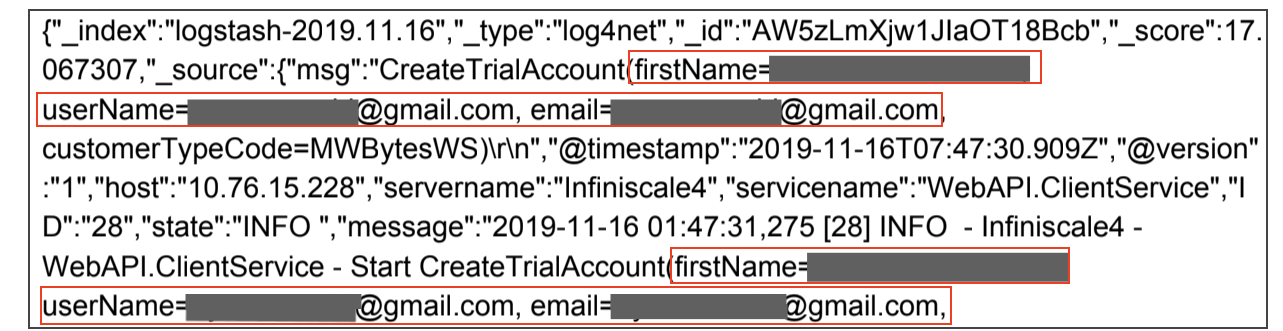
Next, by providing their full name in the "firstName" entry along with their email and username, this user is particularly vulnerable.
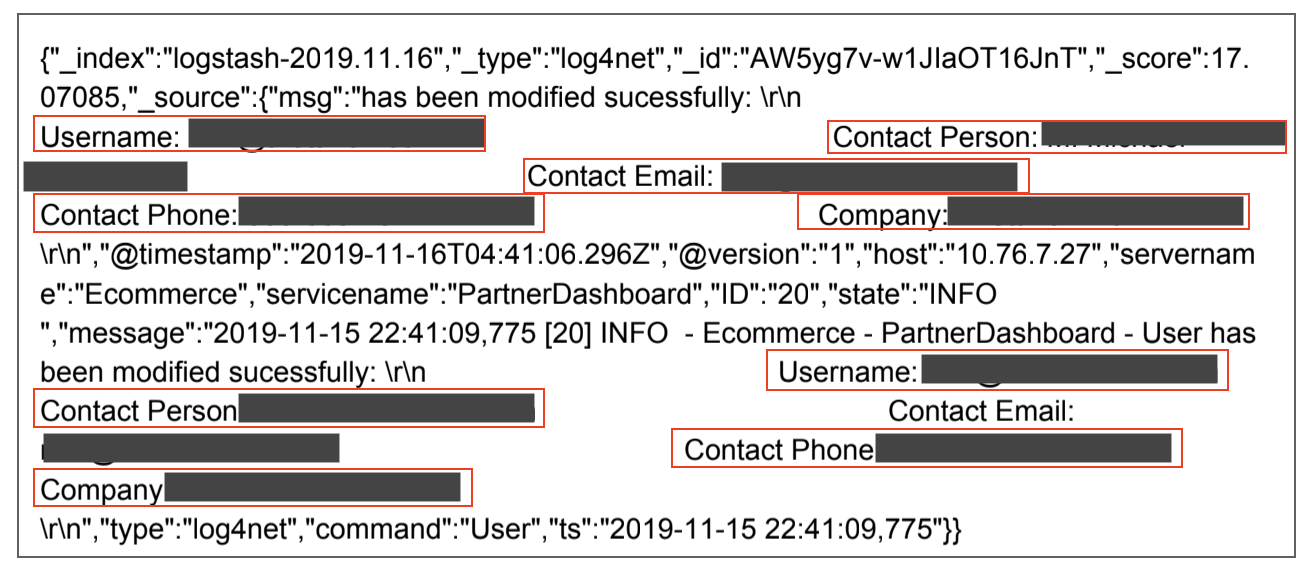
Finally, we have an example of a corporate business customer's details being leaked.
Data Breach Impact
By exposing so much metadata and user PII, SOS Online Backup has made itself and its customers vulnerable to a wide range of attacks and fraud. This database could have been a goldmine for cybercriminals and malicious hackers, with access to cloud storage highly sought after in the online criminal underworld.
For SOS Online Backup
This data leak creates myriad issues for the company, which will need immediate attention. The biggest issue for the company is the negative impact this leak could have on their reputation and trust amongst customers. SOS Online Backup claims 100% privacy & data security. Based on our team's discovery, this is not the case.
The exposed database will also solicit questions about their wider data security policies and how robust they truly are. As a result, current customers may consider moving to another provider. Potential future customers may be reluctant to pay for unsecured cloud accounts. Competitors could also jump on this leak to undermine SOS Online Backup and attack their claims of market-leading security.
This would be an effective marketing tool in luring customers away from SOS Online Backup. There is also the potential for legal action from governments and regulatory bodies within countries that SOS Online Backup operates. California, where the company is based, recently passed the swiping California Consumer Privacy Act (CCPA). This is just one example of new government legislation tackling consumer data privacy and breaches in data security by private companies.
If SOS Online Backup was found to be leaking the data of EU citizens, they would also fall within the jurisdiction of the bloc's GDRP rules. Each of these eventualities would further damage SOS Online Backup's reputation, market share, and revenue.
Finally, the exposed database showed the structure of their cloud-based backup technology, accounts' systems, and how they work. Hackers could use this information to plan effective attacks and embed malicious software in their system. This would allow them to steal customer data and files, or attack SOS Online Backup directly. The consequences of such an attack could be devastating for the company and its customers.
For SOS Online Backup Customers
The exposed database also made SOS Online Backup customers vulnerable to many forms of attack. With the information in these files, hackers and cybercriminals could target victims with phishing campaigns and fraud, gain access to their accounts and download, steal, or ransom their files.
They could also use any stolen files for further fraud, such as identity theft. For example, if users uploaded financial records to their secure accounts, hackers could take this information and break into their online banking or credit card accounts.
The exposed PII data and login credentials for SOS Online Backup could also be used for other illegal uses, such as attempting to access private accounts unrelated to SOS Online Backup. Finally, any data downloaded or stolen could be sold on the Dark Web and become untraceable in the online criminal underworld.
Advice from the Experts
SOS Online Backup could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn't require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For SOS Online Backup Users
If you're a customer of SOS Online Backup and concerned about how this breach, we suggest changing your account username immediately. You should also contact the company directly and ask what steps they're taking to resolve the issue and improve their security.
Whenever feasible, employ two-factor authentication for accessing your private, cloud-based accounts. This method decreases the likelihood of account breach due to an exposed username or password in the event that any of your account holders become victims of hacking or their login credentials are leaked.
To learn more data security, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in SOS Online Backup's database as part of a huge web mapping project.
Our researchers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked. When they find a data breach, they use expert techniques to verify the database's identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this database because it was completely unsecured and unencrypted. The company uses an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing the database schemata.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we're obliged to inform a company when we discover flaws in their online security. This is especially true when the companies data breach contains such private information. These ethics also mean we carry a responsibility to the public. SOS Online Backup users must be aware of a data breach that impacts them also.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data. In the past, we've discovered a huge data breach exposing the data of millions of Ecuadorean citizens. We also revealed that a breach in Biostar 2 compromised the biometric data of over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.


