
Report: 1,000s of UK Consultants and Firms Exposed in Huge Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor's research team recently discovered; a breach in a database containing highly sensitive files from several British consulting firms.
Relating to their respective HR departments, the compromised files exposed detailed sensitive information belonging to the firms, along with 1,000s of British professionals.
Had this database been discovered by criminal hackers, there could have been serious consequences for the security and privacy of those exposed.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times.
Most often, we need days of investigation before we understand what's at stake or who's leaking the data. Understanding a breach and its potential impact takes careful attention and time.
We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness. Some affected businesses disregard our research, deny the facts, or play down its impact.
So, we need to be thorough and make sure everything we present is correct and true.
In this case, the files were being stored on an Amazon Web Services (AWS) S3 bucket database. This is a popular method for storing files on AWS, but requires users to implement their own security protocols. While the owner of the database was not initially clear, it was labeled "CHS".
We traced this back to CHS Consulting, a London-based consulting firm. However, as the company has no website, we cannot confirm their ownership of the database. In the meantime, we also contacted AWS directly and CERT-UK, the country’s Computer Emergency Response Team - responsible for monitoring and handling data security in the UK.
By December 19th, the breach had been closed and the database secured.
- Date discovered: 9/12/19
- Date CERT-UK contacted: 10/12/19
- Date of contact with AWS: 17/12/19
- Date of Response from AWS: 18/12/19
- Date of Action: Approx. 19/12/19
Example of Entries in the Database
The exposed database contained files belonging to many UK-based consultancy firms. These included:
- Dynamic Partners (closed in 2019)
- Eximius Consultants Limited
- Garraway Consultants (closed in 2014)
- IQ Consulting
- Partners Associates Ltd (closed in 2018)
- Winchester Ltd (closed in 2018)
While most of the exposed data were from 2014-2015, some files go back as far as 2011.
Given the nature of the files contained within the database, the information exposed is still relevant and could be used in many ways. The private personal files our team viewed included but were not limited to:
- 1,000s of passport scans
- Tax documents
- Job applications
- Proofs of address
- Extensive background checks
- Criminal records
- Expenses and benefits forms
- Paperwork related business taxes and HMRC
- Scanned contracts with signatures
- Salary information for a range of roles and positions
- Emails and private messages
- A contract for a loan agreement
- Much more
These documents contained a wide range of Personally Identifiable Information (PII) data for 1,000s of British residents and working professionals.
For context, just two files from a single firm contained a full range of PII data:
- Full names
- Addresses
- Phone numbers
- Email addresses
- Dates of birth
- Genders
- Job titles & industries
- National Insurance numbers
- Tax codes
- Immigration and Visa statuses
- Nationalities
- Salary details
- Details of individual consultants’ fees
- Company financial records
Some of these can be seen in the following two snippets (identifying details have been covered): 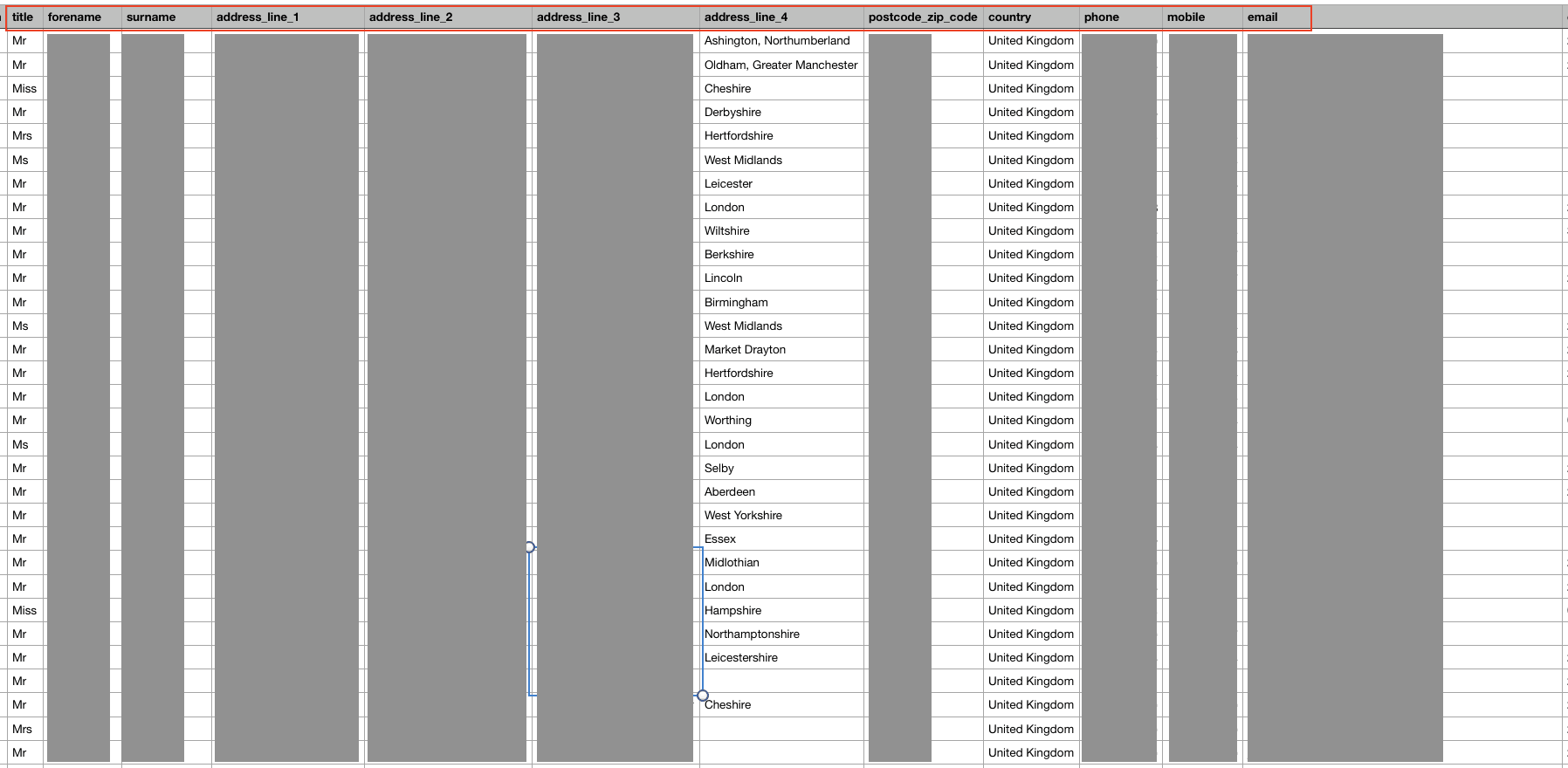
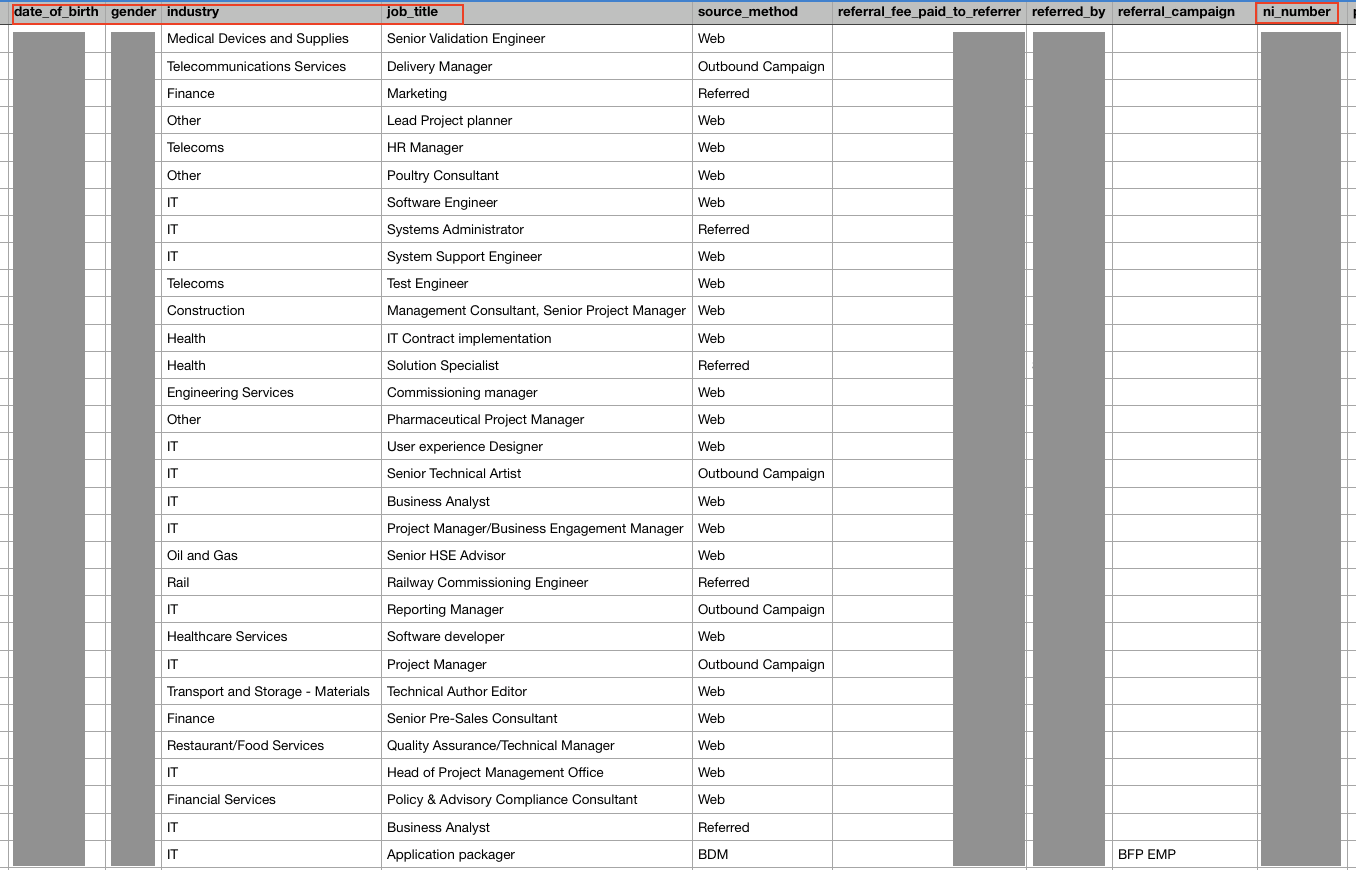
Had criminal hackers discovered this database, it would have been a goldmine for illicit activities and fraud, with potentially devastating results for those exposed.
Advice from the Experts
"CHS" could have easily avoided this leak if they had taken some basic security measures to protect the database.
These include, but are not limited to:
- Securing their servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
Securing an Open S3 Bucket
It's important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They're usually the result of an error by the owner of the bucket.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private. In the case of "CHS", the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For The Individual Consultants and Firms Exposed
If you're a UK-based consultant or consulting firm and are concerned about this breach, contact the CERT-UK to understand what steps are being taken to keep your data safe and ensure it has not been leaked.
To learn more about data vulnerabilities in general, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The research group at vpnMentor detected a breach in the "CHS" database while carrying out a substantial web mapping initiative. Our investigators employ the method of port scanning to inspect specific IP blocks, seeking potential vulnerabilities in systems via any open gaps.
They examine each hole for data being leaked. When they find a data breach, they use expert techniques to verify the database's identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this AWS S3 bucket database because it was completely unsecured and unencrypted. The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we're obliged to inform a company when we discover flaws in their online security. As we couldn't reach out to the owner directly, we reached out to both the NSCS and Amazon, to let them know about the vulnerability but also to have them help us secure the data.
These ethics also mean we carry a responsibility to the public. People affected must be aware of a data breach that impacts them also.
We also never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years. This has included a huge data leak exposing the biometrics and fingerprints of over 1 million people globally.
We also revealed how British video editing platform VEED had compromised the privacy and security of their users. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 31.12.2019]


