
10GB Database Exposing VPN Users Dumped (for Free) on Telegram
21 million records were leaked on Telegram, exposing the email addresses and hashed passwords of the users of several VPNs.
The SQL dump was posted on Telegram on May 7th, 2022.
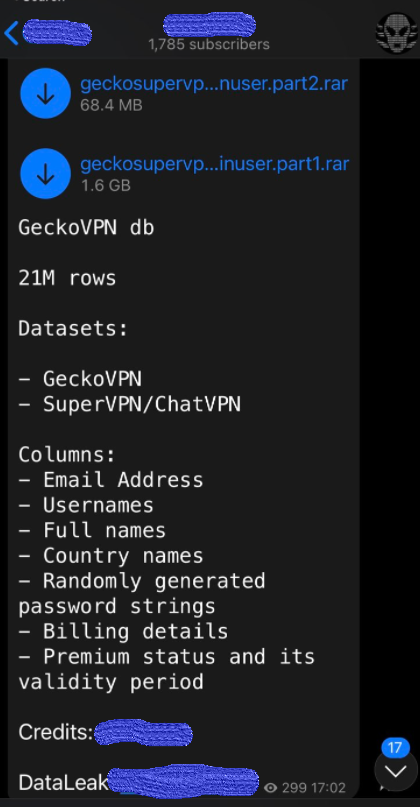
The dump, exposing users from several VPN services including GeckoVPN, SuperVPN, and ChatVPN, was initially offered for sale on the dark web back in 2021. It is now posted for free on Telegram.
The file, a Cassandra database dump, is dated 2021-02-25.
Note that we reported a leak affecting SuperVPN back in 2020, but it seems that the released information is different from our previous report.
The breach contains 21 million records, counting for 10 GB of data, exposing about 21 million people (the records appear to be unique).
Overall, the database contains:
- Email addresses
- Usernames
- Full names
- Country names
- Randomly generated password strings
- Billing details
- Premium status and validity period
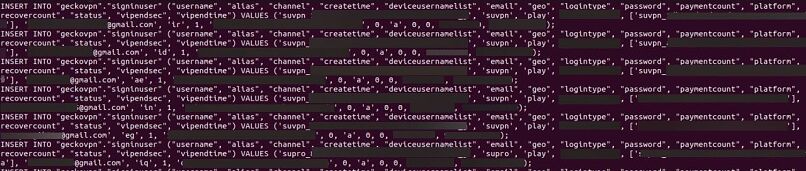
It appears that the passwords were either hashed and salted or random, without collision. This means each password hash is different, making them harder to crack.
99.5% of the email addresses were Gmail accounts, which is much higher than the average percentage. This may also mean the group who leaked the dump shared a subset of the data and not the full dump. It is important to note that for ethical reasons, we do not keep the data. We only keep a sample for the purpose of our research.
GeckoVPN, SuperVPN, and ChatVPN are all free VPN service providers.
You can see a full breakdown of the data exposure in the table below.
| Where and when was the leak posted? | Telegram, on May 7th, 2022 |
| Companies affected | GeckoVPN, SuperVPN, and ChatVPN |
| Size of the exposure | 10 GB, 21 million records |
| Number of affected users | Approx. 21million |
Potential Impacts
VPN users value their privacy and anonymity, making their data more valuable when exposed. When their personal details are leaked, they may become victims of blackmail. For some users, even just the fact that they are using a VPN may put them in danger, and others use a VPN to hide certain things they wish to keep private. A common scam among hackers in the last few years is when they send out blackmail emails declaring they have sensitive information about sites the user visited, and will expose it if not given a certain amount of bitcoin. When they get access to a group of people who value their privacy, such scams may become more profitable for malicious actors.
Bad actors could send phishing messages and scams to exposed users via email, using their full name and other personal details that only the company could know about, such as usernames, countries, or billing details, to build trust.
Furthermore, if hackers manage to access a password, they can seize control of a user's account and exploit their premium status.
Another critical risk would be for this database to end up in the hands of a restrictive government in a country where VPN use is banned or access to certain sites is blocked. This would allow the authorities to potentially arrest dissidents and VPN users.
What Should You Do If You Think You’re Affected?
You may want to take some steps to protect your data if you use one of these VPNs or if you fear that your account may be compromised.
If you haven’t done this yet, you should change your VPN account password immediately, opting for a random mix of upper and lower case letters, numbers, and symbols for maximum security.
You should also ignore any suspicious SMS messages and emails and educate yourself about phishing attacks, scams, malware, and other forms of cybercrime.
What Are Telegram Leaks and Why Should You Care?
As previously reported by our team, hackers are making more and more use of platforms like Telegram to communicate and share information about data breaches.
Telegram uses encryption and offers its users some anonymity. It is also easily accessible and doesn’t require any technical skills. This makes it the perfect platform for hackers to post data breaches, even more so if they want more people to have access to them.
Our cybersecurity researchers scour Telegram and the dark web to find the latest cyberattacks and data breaches. Hackers often post information on these channels before the cybersecurity incident is publicly known.
By reporting on these incidents, we’re able to inform potentially affected parties earlier so that they can act quickly to protect their data.


