
Report: State-owned French Transport Giant Exposes 10,000s of Staff to Fraud in Massive Data Breach
vpnMentor’s research team discovered a data breach in a server belonging to the French transport giant RATP.
RATP is a huge, state-owned company that manages most of the transport infrastructure in Paris and elsewhere. The company has roughly 64,000 employees across various operations.
Our team discovered that RATP had left an old server potentially related to its employee benefits web portal (“comité d’entreprise” or “CE”) with records from the majority of its workforce wide open and accessible to anyone with basic web browsing skills. Furthermore, the same server was being used to store highly sensitive code that exposed the RATP to sophisticated hacking and attacks.
In doing so, the company jeopardized the safety and security of 10,000s of people across France, along with exposing itself to massive risk.
Data Breach Summary
| Company | RATP Group |
| Headquarters | Paris, France |
| Industry | Public Transport |
| Size of data in gigabytes | Approx. 1GB |
| Suspected no. of records | 2,512,473 |
| No. of people exposed | ~57,000 |
| Date range/timeline | 2014-2019 |
| Geographical scope | France |
| Types of data exposed | PII data; API keys; website source code |
| Potential impact | Fraud; identity theft; hacking; ransomware; much more. |
| Data storage format | HTTP Server |
Company Profile
Régie Autonome des Transports Parisiens, also known as RATP, is a state-owned French public transport operator based in Paris.
RATP was established in 1949 to manage public transport in the Greater Paris region. In the decades since, it’s become responsible for the Paris Métro, Île-deFrance tram, RATP bus network, and France’s Regional Express Rail network. RATP has also expanded beyond Franceand, through international subsidiaries, has a presence in 13 countries dotted across Europe, Asia, Africa, and North America.
RATP’s services carry 3.3 billion passengers every year, and the company employs 64,000 people.
Timeline of Discovery and Owner Reaction
- Date discovered: 13th October 2021
- Date vendors contacted: 20th October 2021
- Date of 2nd contact attempt (if relevant): 22nd October 2021
- French CERT contacted: 26th October 2021; replied the same day
- Date of Response: RATP never replied
- Date of Action: between October 26th and October 30th 2021
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. We often need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, RATP was using an exposed HTTP server to store its files. An HTTP server is the same infrastructure on which websites are built and easily accessible via any web browser if not protected. Furthermore, the server was organized as a file directory, making it very easy to navigate. Finally, RATP’s name was found on files throughout.
Once we confirmed RATP was the owner of the data, we reached out to the company to present our findings. We also contacted France’s Computer Emergency Response Team (CERT) to notify it of the breach. The French CERT replied within the same day, and shortly after, the vulnerability was closed.
RATP never replied.
Example of Entries in the Database
RATP’s server contained 2 folders, each containing very different types of records:
- A folder containing source codes and configuration files for websites belonging to RATP. Within the source codes were API keys that granted access to third-party services used by the company’s employee benefits portal’s backend. This revealed incredibly sensitive information about the RATP website and the people using it.
- A database containing records from 57,000 RATP employees, including many people who had retired.
We’ll now look into each of these and what they exposed.
Source Codes and API Keys
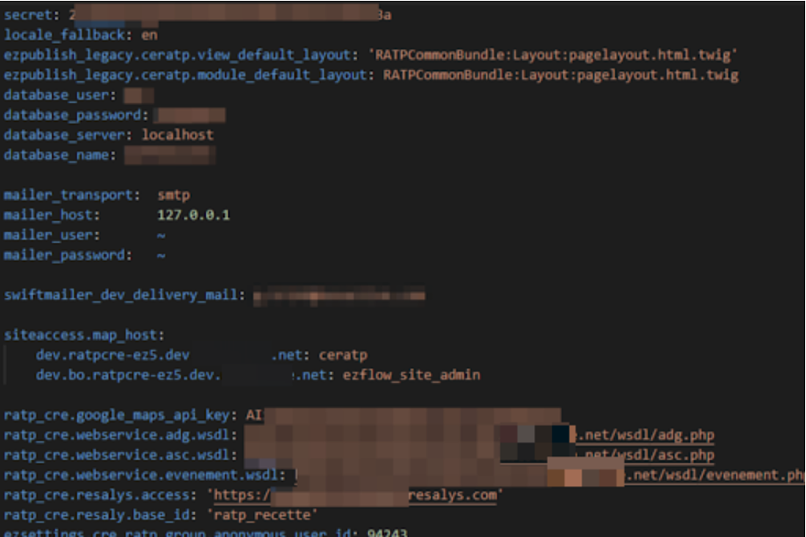
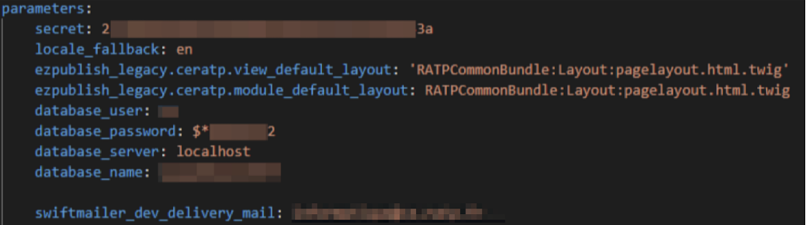
The exposed folder contained configuration files as well as source codes for RATP’s employee benefits web portal. Within these source codes were API keys that granted access to sensitive information about the website’s backend.
It’s important to note that leaked source codes and API keys belong to the domain www.ce.ratp.fr, as this website is the location of RATP’s employee benefits portal.
The API keys exposed the following:
- A database configuration with login credentials
- Secrets for the development environment
- Secrets from the deployment script
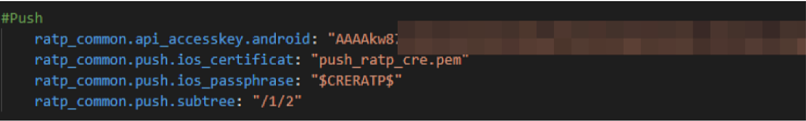
- Access key to send push notifications to Android apps
- A SQL database belonging to RATP
- Details about RATP staff email accounts
It’s possible some of the data also belonged to a second separate website connected to RATP. We believe this may have been a website set up by an outside consultant as an internal platform for RATP employees.
Finally, the folder contained an API key which almost certainly relates to RATP’s GitHub account. For ethical reasons, we didn’t use any of RATP’s API keys or access its GitHub account via the vulnerability we discovered. That means we cannot confirm this conclusion 100%, although we firmly believe the RATP’s Github account could be exposed, and there are genuine risks associated with such a vulnerability.
GitHub is a cloud collaboration platform for developers to build software together remotely. Many companies use GitHub to securely store the source codes for their websites, mobile apps, and much more.
However, if malicious hackers had discovered RATP’s server and the API keys stored within, theoretically, they could perform numerous activities with its GitHub account that would present huge risks to the company and its customers. We’ll explain how further down.
The following screenshots demonstrate how the private data and sensitive code were exposed:
Employee Database
Aside from the source codes and API keys, RATP was also using the exposed server to store an SQL database backup dating back to 2018 which contained over 3 million records. Included among these records were the details of 57,000 RATP employees.
These records exposed a massive range of Personally Identifiable Information (PII) Data, including:
- Full names
- Email addresses
- Login names for RATP employee accounts
- MD5 hashed passwords (it is unclear what they give access to)*
Our team was able to view PII data belonging to current and former RATP employees at the highest level of the company, including its executives, cybersecurity team, and much more.
*The MD5 hash is a very outdated, although still effective, method for encrypting plaintext passwords stored online. It was initially developed in 1991 and has been made completely redundant by advances in encryption since 2011.
As a result, in theory, hackers could still crack some of the passwords by converting billions of plaintext passwords into MD5 hashes and seeing if any match with those stored on RATP’s server. This wouldn’t take very long, as a basic modern commercial laptop is powerful enough to convert 10s of billions of MD5 hashes per second.
To safeguard data and backend infrastructure effectively, RATP (as well as other companies) should implement contemporary encryption methods.
Data Breach Impact
Had malicious or criminal hackers discovered RATP’s server before it was secured, they could have used the exposed data in a wide range of criminal schemes.
The exposed data would have been enough for skilled hackers to commit many of the most common forms of fraud, including:
- Identity theft
- Tax fraud
- Insurance fraud
- Mail fraud
- Bank account takeover
- Debit or credit card fraud
- Mortgage fraud
- Many more...
However, even if the exposed data wasn’t sufficient to exploit for criminal gains, it could also be used to carry out complex phishing campaigns.
In a phishing campaign, criminals send victims fake emails and text messages imitating real businesses and organizations. By building the victim’s trust, they hope to trick them into any of the following actions:
- Providing additional PII data (i.e., social security numbers) or private information (i.e., bank account details) that can be used in the fraudulent activities listed above.
- Inputting debit or credit card details into a fake payment portal, so they can be scraped and used by criminals or sold on the dark web.
- Clicking a link embedded with malicious software that infects a user’s device, such as malware, spyware, and ransomware.
Due to the number of people exposed in this data breach, cybercriminals would only need to successfully scam a small fraction for any criminal scheme to be considered successful. Furthermore, once this information is out in the open, it can be used against you repeatedly for the rest of your life.
Impact on RATP
The exposed API keys represented a massive security risk for RATP and gave malicious criminals numerous potential attack vectors.
For example, the API keys for sending push notifications would allow hackers to send RATP app users messages directly from the app itself, leading to a wide range of criminal activities and embarrassing issues for the company.
Depending on the permissions granted by the GitHub API keys, hackers could potentially do any of the following:
- Create or delete software projects being built on RATP’s account.
- Add themselves as users on RATP’s GitHub account.
- Change configurations and source codes on live apps or websites being managed from GitHub.
- Embed malicious backdoors into RATP’s apps, websites, and network.
- Plant ransomware to shut RATP’s apps, websites, and network down completely.
Any of these outcomes would massively disrupt RATP’s operations. Considering it services 3.3 billion people annually, the impact could devastate France and bring the country’s capital to a standstill.
Aside from the security risks posed by this data breach, RATP may also face regulatory scrutiny for exposing so many of the employees’ private data. RATP is within the jurisdiction of the EU’s GDPR, and as a state-owned company employing 10,000s of French people, it risks considerable backlash for such an egregious lapse in protocols.
Advice from the Experts
RATP could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
- Updating its security protocols and using newer forms of encryption.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For RATP Employees
If you work at RATP and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a massive web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
RATP was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to RATP, not only to let them know about the vulnerability but also to suggest ways in which it could make its system secure.
These ethics also mean we carry a responsibility to the public. RATP customers and staff must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included exposing the growing popularity of cybercrime groups on Telegram. We also revealed how a popular Chinese game developer was leaking data from over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.


