
Report: Indonesian Government’s Covid-19 App Accidentally Exposes Over 1 Million People in Massive Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach in the Indonesian government’s eHAC program created to tackle the COVID-19 pandemic spread in the country.
eHAC is a ‘test and trace’ app for people entering Indonesia to ensure they’re not carrying the virus into the country.
The app was established in 2021 by the Indonesian Ministry of Health. However, the app developers failed to implement adequate data privacy protocols and left the data of over 1 million people exposed on an open server.
Data Breach Summary
| Responsible Party | Ministry of Health (Kemenkes), Republic of Indonesia |
| Headquarters | Jakarta, Indonesia |
| Industry | Public Health |
| Size of data in gigabytes | 2 GB |
| Suspected no. of records | 1.4m+ |
| No. of people exposed | Approx. 1.3 m |
| Geographical scope | Indonesia |
| Types of data exposed | PII data; travel information; medical records; COVID-19 status |
| Potential impact | Fraud; Hacking; Disinformation |
| Data storage format | Elasticsearch |
What is eHAC?
The Indonesian government introduced the electronic Health Alert Card (eHAC) to help combat the spread of COVID-19 within the country.
It’s a mandatory requirement for any traveler entering Indonesia from overseas, both Indonesian citizens and foreigners. It’s also required for domestic flights within Indonesia.
The eHAC app is downloaded onto a passenger’s mobile device and stores their up-to-date health status, Personally Identifiable Information (PII) data, contact details, COVID-19 test results, and much more.
Timeline of Discovery and Response
- Databased discovered: 15th July 2021
- Contacted Ministry of Health (Kemenkes) Republic of Indonesia: 21st July 2021
- Disclosure made to Indonesian CERT: 22nd July 2021 (https://www.cert.or.id/), 16th August 2021 (https://idsirtii.or.id/) and 22nd August 2021 (https://bssn.go.id/)
- Disclosure made to Google (hosting provider): 25th July 2021
- 2nd contact attempt with Kemenkes: 26th July 2021
- Date of Response: -
- Date of response (BSSN): 22nd August 2021
- Date of Action: 24th August 2021
Sometimes, the extent of a data breach and the data owner are obvious, and the issue is quickly resolved. But rare are these times. Instead, we often need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, our cybersecurity team discovered the exposed database as part of a broader effort to reduce the number of data leaks from websites and apps around the world.
Our team discovered eHAC’s records with zero obstacles, due to the lack of protocols put in place by the app’s developers. Once they investigated the database and confirmed the records were authentic, we contacted the Indonesian Ministry of Health and presented our findings.
After a couple of days with no reply from the ministry, we contacted Indonesia’s CERT* agency and, eventually, Google - eHAC’s hosting provider.
By early August, we had not received a reply from any of the concerned parties. We tried to reach out to additional governmental agencies, one of them being the BSSN (Badan Siber dan Sandi Negara), which was established to carry out activities in the field of cyber security. We contacted them on August 22nd and they replied on the same day. Two days later, on August 24, the server was taken down.
*The Indonesia Computer Emergency Response Team (ID-CERT) is a government agency responsible for addressing cybersecurity incidents in the country. Most countries have a similar agency to address localized data leaks and hacks.
Example of Entries in the Database
The developers of eHAC were using an unsecured Elasticsearch database to store over 1.4 million records from approximately 1.3 million eHAC users.
These records didn’t just expose the users. This data leak exposed the entire infrastructure around eHAC, including private records from hospitals and Indonesian officials using the app.
The following is a breakdown of the various types of data exposed.
COVID-19 Test Data
- Passenger ID and type (including domestic and international travelers)
- Hospital ID
- Queue number while doing this test
- Reference number
- Address and time for home visit
- Test type (PCR, rapid antigen, etc.), date, and place
- Test result and date issued
- eHAC document ID
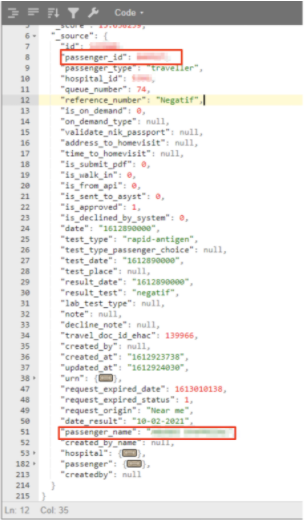 A record revealing passenger name, date of test, result, and more
A record revealing passenger name, date of test, result, and more
eHAC Account Data
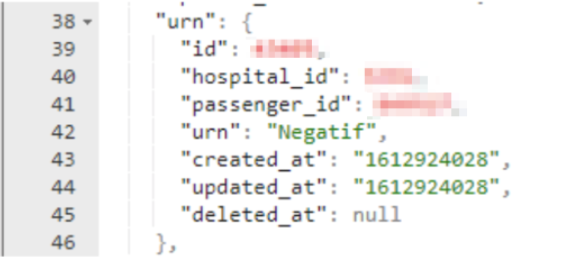
Each record also contained Unit Record Number (URN) details specific to eHAC, including:
- Passenger name and URN ID number
- URN hospital ID number
- Much more
Individual Hospital Data
Data from 226 hospitals and clinics in Indonesia was also exposed:
- Hospital details (ID, name, country, license number, address and exact location (with coordinates), phone and WhatsApp number, opening hours)
- Name of the responsible person for the passenger
- Name of the passenger’s doctor
- Hospital capacity
- Allowed test types in the hospital
- Information about how many tests were done each day
- Which type of passengers are allowed in this hospital
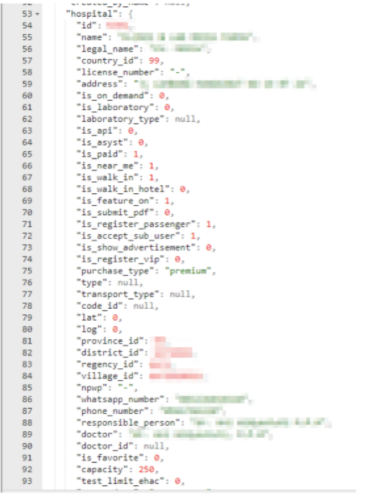 Hospital data exposed, including staff PII data
Hospital data exposed, including staff PII data
Passenger PII Data
- Passenger details (ID number, full name, mobile phone number, DOB, citizenship job, gender, etc.)
- Passenger’s national Indonesian ID number (where applicable)
- Passport and profile photo attached to eHAC account
- PII data for passenger’s parent(s) or next of kin
- Passenger’s hotel details (name, address, phone number)
- Additional passenger photo ID (possibly a placeholder for future use)
- Details about a person’s eHAC account and when it was created
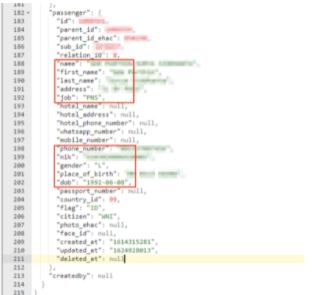 Records potentially exposing vast amounts of PII data
Records potentially exposing vast amounts of PII data
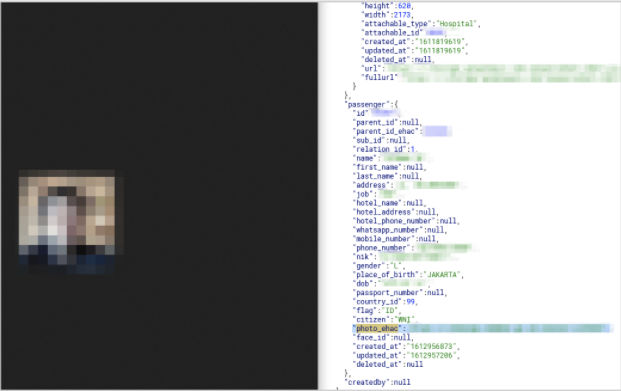 Records exposing PII data and profile photo
Records exposing PII data and profile photo
PII Data From eHAC Staff
The database held considerable information about the staff creating passenger accounts on eHAC:
- ID number
- Name
- eHAC account username
- Email address
- Whether they’re using a default password for their eHAC account
- eHAC account creation date, along with updates
Data Breach Impact
This data leak has wide-ranging implications for eHAC and the Indonesian government’s efforts to contain COVID-19.
Had the data been discovered by malicious or criminal hackers, and allowed to accumulate data on more people, the effects could have been devastating on an individual and societal level.
For Users
The massive amount of data collected and exposed for each individual using eHAC left them incredibly vulnerable to a wide range of attacks and scams.
With access to a person’s passport information, date of birth, travel history, and more, hackers could target them in complex (and simple) schemes to steal their identity, track them down, scam them in person, and defraud them of thousands of dollars.
Furthermore, if this data wasn’t sufficient, hackers could use it to target a victim in phishing campaigns over email, text, or phone calls. In a phishing campaign, hackers pose as legitimate businesses or government officials to trick victims into any of the following:
- Provide additional PII data used to steal their identity or access private accounts (i.e., tax records and bank accounts)
- Make payments with their credit cards on fake websites and portals, which the hackers set up to scrape their credit card details.
- Click a link embedded with a virus, such as ransomware or spyware, to attack, spy on, and defraud a victim via their device.
Criminals could easily use the eHAC data to pose as health officials following up on a person’s COVID-19 test, build trust, and pressure them into relinquishing even more sensitive information.
We estimate over 1.3 million people have been exposed in this data leak. As a result, cybercriminals would only need to trick and defraud a small sample of the passengers to consider their scheme(s) a financial success.
For eHAC and Indo MOH
The leak also poses several risks for the eHAC app, the Indonesian government, and the country’s efforts to contain the spread of Coronavirus.
Hacking and Viral Attack
The records stored within the eHAC database could potentially allow hackers to access the app directly and change data on passengers, including their COVID-19 test results. Given the scale of records exposed and the number of people being tested, such an action could wreak havoc on Indonesia’s response to the pandemic.
Due to ethical concerns, we did not test this theory, but our investigation pointed to clear indicators it would be possible.
Aside from changing records on the app, hackers could also use the database to attack it with various viruses and malicious software, including ransomware - an increasingly popular tool amongst criminal cybergangs.
Lastly, if hackers can’t find a way to exploit the database directly, they could use the eHAC staff records stored within to break into the eHAC network via a ‘backdoor.’ Staff could be targeted in phishing campaigns similar to those described above, and the repercussions would be even more significant.
A single eHAC staff member clicking a dangerous link could expose the entire network and infrastructure built to support the app. Skilled hackers could even use it as a launchpad to infiltrate and attack the highest levels of Indonesia’s government.
Increased Vaccine Hesitancy and Distrust
Had anyone successfully exploited the eHAC database for criminal gain, and news of this became public, the government would have to contend with a significant backlash.
Distrust, misinformation, and conspiracy theories have been huge obstacles in the fight against the Coronavirus pandemic, not just in Indonesia. But if the Indonesian people learned the government had exposed over 1 million people to attack and fraud via an app built to combat the virus, they may be reluctant to engage in broader efforts to contain it - including vaccine drives.
Bad actors would undoubtedly exploit the leak for their gain, jumping on any frustration, fear, or confusion, creating mistruths and exaggerating the leak’s impact beyond all reasonable proportion.
All of these outcomes could significantly slow down Indonesia’s fight against Coronavirus (and misinformation in general) while forcing them to use considerable time and resources to fix their own mess. The result is further pain, suffering, and potential loss of life for the people of Indonesia.
For Hospitals
While the hospitals using the eHAC were mostly safe from the worst outcomes of the leak, they still face a degree of risk.
Hackers could harvest data from the app on individual hospitals and their staff, using this information to target the hospitals in various phishing, fraud, and viral attacks.
The success of such criminal schemes would depend on the skills of the hackers and each hospital’s awareness of and training against cybersecurity risks.
Advice from the Experts
The developers behind eHAC could have easily avoided this leak if they took some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Regardless of its size, any company has the capability to replicate identical steps.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For eHAC Users
If you’ve registered on eHAC and are concerned about how this breach might impact you, contact the Indonesian Ministry of Health directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a vast web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
eHAC was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in its online security. We reached out to the various parties responsible for eHAC to inform them about the vulnerability and suggest ways to secure their system.
These ethics also mean we carry a responsibility to the public. eHAC users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included exposing the growing popularity of cybercrime groups on Telegram. We also revealed how a data leak by the biggest US baby apparel chain had compromised 100,000s of customers’ data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.


