
Report: Popular Chinese Android Game Developer Exposes Over 1 Million Gamers to Hacking
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach belonging to Chinese mobile gaming company EskyFun.
The company was using an unsecured server to store vast amounts of data collected from users on its games. Much of this data was incredibly sensitive, and there was no need for a video game company to be keeping such detailed files on its users.
Furthermore, by not securing the data, EskyFun potentially exposed over 1 million people to fraud, hacking, and much worse.
Data Breach Summary
| Company | EskyFun |
| Headquarters | China |
| Industry | Mobile gaming |
| Size of data in gigabytes | 134 GB |
| Suspected no. of records | 365,630,387 |
| No. of people exposed | Potentially 1M+ (based on total downloads of EskyFun games on Android) |
| Date range/timeline | June 2021 - Present |
| Geographical scope | Global |
| Types of data exposed | PII data; tracking and analytics data; device permissions |
| Potential impact | Phishing; Fraud; Corporate espionage; Hacking |
| Data storage format | Elasticsearch |
Company Profile
EskyFun Entertainment Network Limited is a Chinese mobile game publisher with numerous gaming titles available on Android. Their games are a mix of role-playing and fantasy adventures that, combined, have over 1,500,000 downloads.
The EskyFun games affected in this data leak were: Rainbow Story: Fantasy MMORPG (500,000+ downloads); Metamorph M (100,000+ downloads); Dynasty Heroes: Legends of Samkok (1,000,000+ downloads).
Timeline of Discovery and Owner Reaction
- Date discovered: 5th July 2021
- Date vendors contacted: 7th July 2021
- Date of 2nd contact attempt: 27th July 2021
- Date we contacted Hong Kong CERT: 27th July 2021
- Date of Response: -
- Date of Action: by 28th July 2021
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Instead, we often need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, our team discovered the EskyFun database in early July. Once we had confirmed the details of the leak, and EskyFun as the responsible party, we reached out to the company immediately. After a couple of weeks with no reply, we sent a follow-up email and contacted the Hong Kong CERT.*
Hong Kong CERT was rapid and proactive in its response, seeking additional information to take appropriate measures. However, at this point, the database was secured, and the breach had been closed.
As we never heard back from EskyFun, we can’t confirm exactly when it fixed the vulnerability.
*The Hong Kong Computer Emergency Response Team (HKCERT) is a government agency responsible for addressing cybersecurity incidents in the country. Most countries have a similar agency to address localized data leaks and hacks.
Example of Entries in the Database
EskyFun’s server was storing a rolling log of the previous 7 days’ user records from 3 separate games. At the end of each day, any data older than 7 days was automatically deleted to make room for fresh data.
As a result, our investigation focuses on just 7 days’ worth of data and any players exposed in that short window.
However, despite only covering 7 days, the server still contained over 360 million records from players. This is an enormous amount of data collected from a few small, not well-known mobile games.
Affected Games
Dynasty Heroes: Legends of Samkok
Excessive Permissions and Tracking
The reason for the sheer size of the data exposed appears to be EskyFun’s aggressive and deeply troubling tracking, analytics, and permissions settings.
Most likely, most players have no idea just how much data and access they’re providing to EskyFun just from downloading one of the company’s games. In fact, it appears you don’t even need to start playing a game before it’s accessing your devices’ settings and networks.
The following table shows the various tracking programs connected to EskyFun’s games.
| Tracking App | Permission |
| Adjust | analytics |
| AppsFlyer | analytics |
| Bugly | analytics |
| Facebook Analytics | analytics |
| Facebook Login | identification |
| Facebook Share | social media |
| Google AdMob | advertisement |
| Google Firebase Analytics | analytics |
| Tencent MTA | analytics |
| Tencent Stats | analytics |
The following table shows how many permissions users allow EskyFun every time they download and install a game from the company. As you can see, EskyFun gains access and control to almost every aspect of a person’s device and even their private networks.
| Permission | Purpose |
| ACCESS_NETWORK_STATE | view your device network connections |
| ACCESS_WIFI_STATE | view your device Wi-Fi connections |
| BLUETOOTH | the app can pair with Bluetooth devices |
| BLUETOOTH_ADMIN | access your device Bluetooth settings |
| CHANGE_NETWORK_STATE | change your device’s network connectivity |
| CHANGE_WIFI_STATE | connect and disconnect your device from Wi-Fi |
| GET_TASKS | application has permissions to see which other applications are running on the phone at the same time |
| INTERNET | give the app full network access from your device |
| MODIFY_AUDIO_SETTINGS | change your audio settings |
| READ_EXTERNAL_STORAGE | the app can read the contents of your SD card |
| RECEIVE_BOOT_COMPLETED | the app runs at startup |
| RECORD_AUDIO | the app can record audio on your device, i.e., phonecalls |
| REQUEST_INSTALL_PACKAGES | request install packages |
| WAKE_LOCK | the app prevents your phone from sleeping |
| WRITE_EXTERNAL_STORAGE | the app can modify or delete the contents of your SD card |
| WRITE_SETTINGS | the app can modify your device system settings |
| BILLING | Allows in-app purchases. Required for making purchases within the app without visiting the play store. |
| CHECK_LICENSE | used for checking if the current user owns the game |
| C2D_MESSAGE | (cloud to device messaging) A kind of permission for push notifications. |
| RECEIVE | allows receiving push notifications |
| BIND_GET_INSTALL_REFERRER_SERVICE | Allows the app to recognize where the application was installed from (play store or another store etc.) |
| PUSH | The app can send push notifications |
Due to this excessive tracking and access, EskyFun was harvesting vast amounts of data from players - most of it totally unnecessary for the games to function.
Tracking Records: 15M+
While EskyFun's game apps are active, they seemingly monitor and record all user actions, leading to the accumulation of extensive sensitive information, which includes the following:
- IP address
- IMEI number
- Mobile application package doing the tracking
- Device screen size - whether a device is ‘rooted’*
- Device model
- Phone number (if any)
- Platform (Android/iOS)
- NetType (WiFi or cellular)
- Events (open,login,level_up, etc)
*A ‘rooted’ device is one in which the user has gained total administrative controls. Smartphone manufacturers restrict access to certain functions and abilities on their devices, such as the operating system (OS). But if someone ‘roots’ their device, they have bypassed these restrictions.
Login Records: 6,000-10,000
The apps also recorded any time a user logged into a game and tracked additional information specific to that moment, including the person’s exact ‘GeoIP’ location.
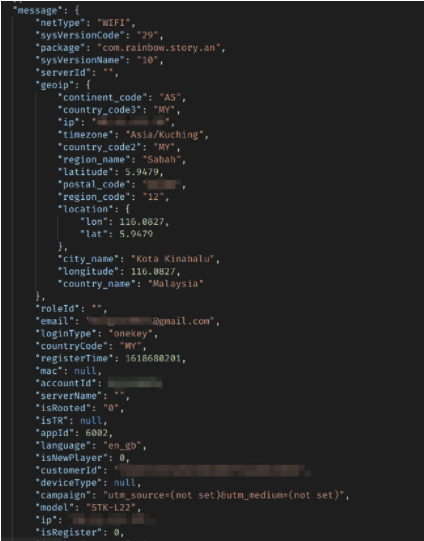 User in Malaysia exposed
User in Malaysia exposed
Receipts: 148,000+
The database contained receipts generated by purchases made in-game over the previous 7 days. These included the following data:
- Which game the purchase was made on
- Buyer account ID
- Amount paid
- Transaction date and time
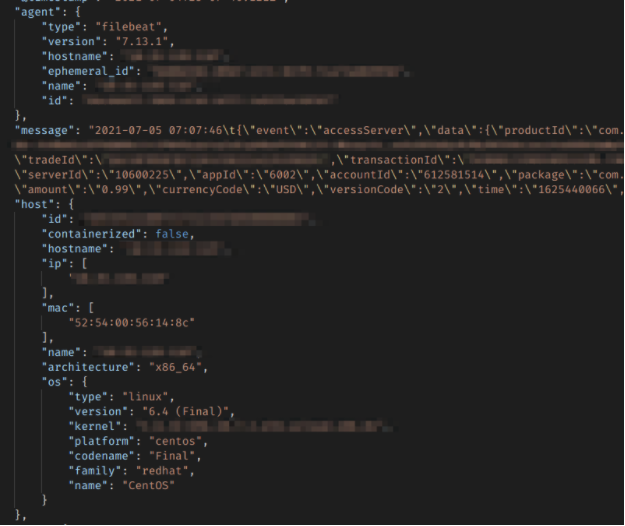 A snippet of receipt record for payment made in-app
A snippet of receipt record for payment made in-app
Runtime Logs: 217M+
Run time logs contained all kinds of data, some of which were incredibly sensitive.
Even in the small sample, we still found the following records on users:
- Email addresses
- Plain text passwords for EskyFun accounts
- Support requests
- Much more
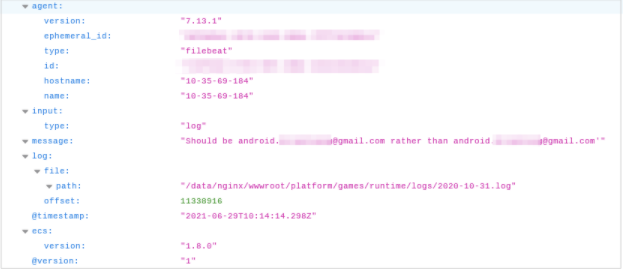 A support request made in-game
A support request made in-game
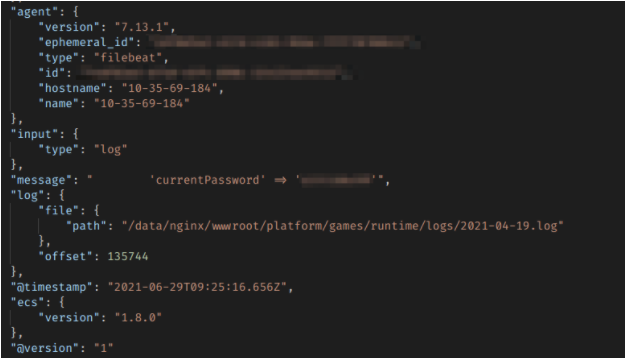 EskyFun user’s password exposed in the database
EskyFun user’s password exposed in the database
Data Breach Impact
By not securing its users’ data, EskyFun has put potentially millions of people at risk of fraud and cyberattack.
Phishing, Fraud, and Scam
The abundance of PII data for each user in the database opens up a wide range of attack options for criminal hackers.
Combining a user’s email address, gaming history, and support requests, hackers could send thousands of phishing emails posing as EskyFun’s support.
For example, suppose a player is having issues making payments within a game. In that case, an attacker could send an email directing them to a malicious website with a fake payment portal set up to scrape their credit card details, steal from them, or embed a virus on their device (i.e., ransomware, spyware, tracking, etc.).
Given the wealth of information stored about each user, appearing legitimate and building trust would be very easy for an experienced cybercriminal. The database also contained plenty of data to build a profile of users and identify two vulnerable groups: high-paying accounts and children. By focusing on these users, hackers could reap huge financial rewards from a small group of victims.
Furthermore, considering how many people were exposed in the leak, they would only need to trick a small fraction of users for a campaign to be considered successful.
Using Passwords to Hack Other Accounts
EskyFun’s database also contained plaintext passwords for user accounts on its games.
Hackers could use these passwords to access and take over EskyFun gaming accounts and commit further acts of fraud against users.
However, the more significant risk comes from hackers using these passwords outside of EskyFun’s network. This is because most internet users share their passwords across multiple private accounts and devices. For example, a person’s EskyFun account password might be the same as their bank account.
Criminal hackers know this. So, they would most likely use the email addresses and passwords in EskyFun’s database to conduct brute force attacks against users, bombarding websites across the internet with their email and password in the hope of accessing private accounts.
The result could be catastrophic. And worse, it would be almost impossible to trace a successful attack back to EskyFun.
Corporate Espionage
The leak also poses a risk to EskyFun.
Competitors could use the leak to learn about EskyFun’s games and what makes them successful while also running a smear campaign against the company, highlighting how much the company endangered its customers.
In doing so, they could simultaneously build rival games almost identical to EskyFun’s games, and then micro-target EskyFun users to promote their ‘safer’ alternatives.
Advice from the Experts
EskyFun could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For EskyFun Users
If you’re a player on any of EskyFun’s games and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a vast web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
EskyFun was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to EskyFun, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. EskyFun users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included exposing the growing popularity of cybercrime groups on Telegram. We also revealed how a data leak by the biggest US baby apparel chain had compromised 100,000s of customers’ data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.


