
Report: Popular Marketing Tool Exposes Dating Site Users in Massive Data Leak
vpnMentor’s research team recently received a report from an anonymous ethical hacker about a massive data leak exposing users of over 70 adult dating and e-commerce websites from around the world.
The various websites were all using the same marketing software built by email marketing company Mailfire — who was responsible for the leak.
The software in question had been compromised through an unsecured Elasticsearch server, exposing people all over the world to dangers like identity theft, blackmail, and fraud.
Upon further investigation, it turned out that some of the sites exposed in the data leak were scams, set up to trick men looking for dates with women in various parts of the world.
Data Leak Summary
| Company | Mailfire |
| Headquarters | Cyprus |
| Industry | Online Marketing |
| Size of data in gigabytes | 882.1 GB |
| Suspected no. of records | 320 million |
| Websites affected | 70+ |
| No. of people exposed | 100,000's |
| Date range/timeline | August 2020 |
| Geographical scope | Worldwide |
| Types of data exposed | Notification contents; PII data; Private messages; Authentication tokens and links; Email content |
| Potential impact | Fraud; Identity theft; Phishing scams; Blackmail and extortion; Website account takeover |
| Data storage format | Elasticsearch |
Timeline of Discovery, Investigation, and Owner Response
- Data leak discovered: 31st August 2020
- Vendors contacted: 3rd September 2020
- Response received from Mailfire: 3rd September 2020
- Server secured: 3rd September 2020
- Client companies informed: 4th September 2020
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the data leak originated from an unsecured Elasticsearch server, which we suspected was owned by Mailfire. The server appeared to be connected to a notification tool used by the company’s clients to market to their website users and notify them of private chat messages.
After investigating the server and compiling sufficient evidence to confirm Mailfire owned the exposed server, we reached out to the company and presented our findings. They acted immediately and secured the server within a few hours. Mailfire assumed full responsibility and insisted that the companies exposed were in no way responsible at all — and our research has also confirmed this to be true.
It is also worth noting that Mailfire is not responsible for the activity of the customers using their service.
Websites Affected by The Data Leak
In total, more than 70 websites were affected in the data leak, all using Mailfire services.
Most of the websites using the tool were adult dating websites. However, the database also contained data from e-commerce websites.

Screenshot of Mailfire homepage - Sep 3, 2020
Among the websites affected included a dating site for meeting Asian women, a premium international dating site targeting an older demographic, one for people who want to date Colombians, and more similar sites connecting men to women in different parts of the world.
It also appeared that many of the websites shared common owners.
Example of Entries in the Database
Based on our investigation, the unsecured server was a log for notifications being sent by the owners of all 70+ websites via Mailfire’s software.
At the beginning of our investigation, the server’s database was storing 882.1 GB of data from the previous four days, containing over 370 million records for 66 million individual notifications sent in just 96 hours.
This is an absolutely massive amount of data to be stored in the open, and it kept growing. Tens-of-millions of new records were uploaded to the server via new indices each day we were investigating it.
It’s also possible older data had been stored before this time. However, it appears that the exposed server was the victim of a recent and ongoing ‘Meow’ cyberattacks campaign that has been targeting unsecured Elasticsearch servers and wiping their data.
Based on what we observed, the notifications were primarily used to alert website users of new messages from potential matches, with some other functions included.
Each of the millions of notifications contained valuable and sensitive Personally Identifiable Information (PII) data for people using the affected websites to send and receive messages.
The PII data revealed included:
- Full names
- Age and date of birth
- Gender
- Email addresses
- Locations of senders
- IP addresses
- Profile pictures uploaded by users
- Profile bio descriptions
Aside from the PII data, the leak also exposed conversations happening between users on dating sites affected.
These often revealed private and potentially embarrassing or compromising details of people’s personal lives and romantic or sexual interests.
The following screenshots, taken from the database, show how people worldwide were exposed by this data leak.
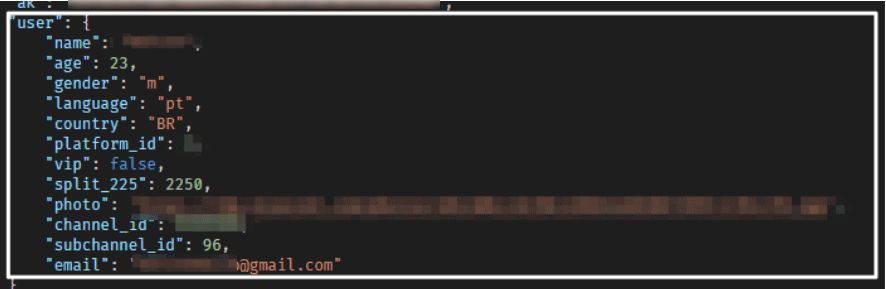
PII data from both the sender and receiver, a resident of Brazil, are exposed
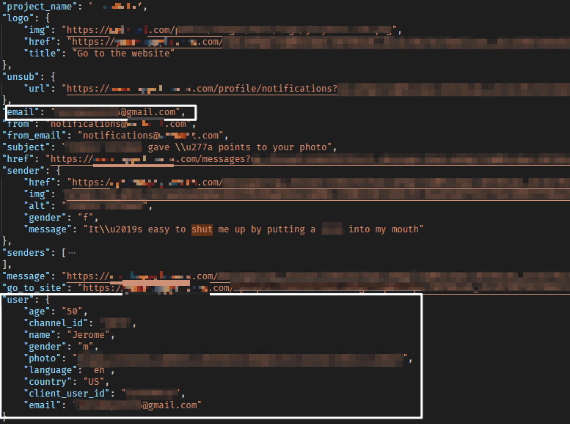
An explicit text (potentially written by a chatbot) is sent to a user in the USA, also exposing his PII data
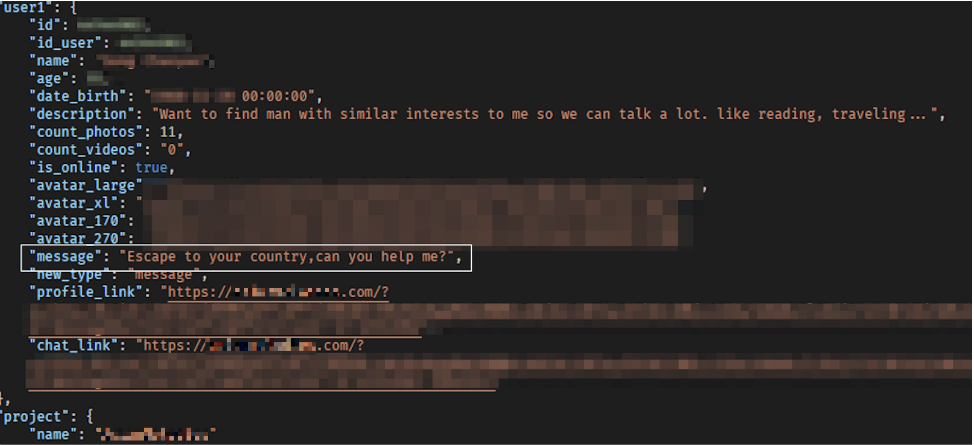
A user in China asks for help escaping from the country, potentially written by a chatbot
Furthermore, it was possible to view all the emails sent by the companies, including the emails regarding password reset. With these emails, malicious hackers could reset passwords, access accounts and take them over, locking out users and pursuing various acts of crime and fraud.
The number of sites affected and the amount of data makes it difficult to calculate how many people were exposed by the data leak.
However, we know that it affected people from across the globe, in over 100 countries, including:
- Afghanistan
- Australia
- Belgium
- Canada
- Estonia
- France
- Germany
- Hong Kong
- Israel
- Japan
- Kenya
- New Zealand
- Portugal
- Qatar
- Russia
- Singapore
- UK
- USA
Data Leak Impact
As mentioned above, Meow hackers have already successfully attacked the server potentially leaking this data once before and deleted all the data stored.
Unfortunately, this is just one of many ways cybercriminals could have used the server (and its data) for criminal activities, with potentially far-reaching and devastating consequences for the people exposed.
Fraud and Identity Theft
PII data exposed in the leak could be used in several fraudulent activities.
For example, hackers could exploit it for phishing scams (see below), attempt to access private accounts on other platforms by testing login details for reuse, and pursue various financial fraud schemes.
Phishing Scams and Malware
Cybercriminals could use contact information like names and email addresses to target users with phishing emails, tricking them into sharing even more sensitive data, like credit card details or login credentials, or clicking links embedded with malware.
A user’s personal information and account details on a particular website would make it easy for cybercriminals to imitate the website in question, establish trust with their targets, and successfully trick them.
Blackmail and Extortion
Since many of the websites impacted by the data leak are adult dating websites, a bad actor may try blackmailing users, threatening to ‘expose’ their private messages in public and extort money.
Corporate Espionage
Competitors of the impacted websites could use this data leak to attract users to their platforms in a couple of ways.
Firstly, they could use the negative publicity in aggressive marketing campaigns calling out the websites involved for not protecting their users’ data. They could then offer their services as a ‘safer’ alternative.
Furthermore, had the database been leaked publicly, competitors could have gone one step further. They could use it to micro-target people via their PII data for highly effective marketing campaigns, making it even easier to convert them.
Cyberattack
The server responsible for this data leak has already been successfully attacked once. Meanwhile, the Meow attacks continue to be a growing threat and could strike against the server again if it isn’t appropriately protected going forward.
Simultaneously, other malicious hackers could now view the server, and its owner, as an easy target for future attacks.
Account Takeover
Since the URLs exposed in the data leak contained login-bypass tokens, hackers could take over private accounts on the websites affected. With access to the accounts, hackers could lock out users and exploit their account in numerous ways.
Investigating the Websites - What we discovered
Almost all of the companies that owned websites we found on the server, maybe all of them in fact, were based in notoriously secretive ‘offshore’ locations, such as the British Virgin Islands, Gibraltar, and Nevada, USA.
After finding out many accounts appeared to be fake, we decided to investigate some of these websites to check if they were legitimate or being used to scam people in any way.
As the leak exposed email addresses and profile pictures linked to user accounts, we could check a sample of these online and assess their legitimacy.
We found throughout several websites that disingenuous accounts were a huge issue. Many profile photos used were registered on scam databases or reused across accounts. Some were simply photos of celebrities found online.
Furthermore, many sites required female users to register through customer support manually, but made it much easier for men to register. On some, ‘man seeking man’ was not a working option. Such restrictions suggest that these websites’ owners are not focused on creating real, honest connections, but something less legitimate.
Many of the sites had complicated, difficult to understand payment structures and some refused to offer refunds. Some required a credit card as ‘proof of age,’ yet the fine print declared the card would be charged $29.90 monthly.
Lastly, after opening dating accounts on a couple of the websites, we were approached by a barrage of messages from other ‘members,‘ that turned out to be chatbots - many with identical messages. We verified this by asking topical questions about current affairs that the chatbot wasn’t programmed to answer.
Based on the findings outlined above, we believe that some of the websites exposed in this data leak were set up primarily to scam men through catfishing and other forms of fraud.
Advice from the Experts
Mailfire could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on protecting your business, check out our guide to securing your website and online database from hackers.
For Companies Using Notification Tools
Whenever you incorporate software from a third party into your digital framework, it is essential to meticulously scrutinize it for any potential weaknesses that could jeopardize you or your customers' safety.
Furthermore, always review the amount of customer PII data being shared with 3rd party tools. You should only be required to provide the absolute minimum data needed for a tool to perform its intended function successfully.
For Users of the Affected Websites
If you think you use a website affected by this data leak, contact them immediately and ask what steps they’re taking to protect your data.
Whenever using dating websites, or any sites that connect you with strangers, always be careful about what information you share. Before sending any message on a dating site, stop and ask yourself if you’d be comfortable having it shared publicly - this is always a risk. You can always share partial data, like your birth year, but not your birth date; or introduce a typo in your name; etc.
Make sure the website is safe and well known, with independent reviews on sites like Reddit, Facebook, etc. Check its payment and refund policies, to ensure you’re not getting ripped off.
Finally, whenever chatting to a stranger online, you can test to make sure it's not a chatbot by asking topical questions about recent events that only a real human could answer.
To learn about data vulnerabilities in general, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team was contacted by an anonymous hacker who wished to share the details of Mailfire’s data leak, due to our reputation in the ethical hacking community and our huge, ongoing web mapping project.
When a vulnerability is reported to us, we rigorously test the relevant systems for weaknesses or vulnerabilities. We also examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted. The data was being stored on an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Mailfire, not only to let them know about the vulnerability but also to suggest ways to make their systems secure. We also reached out to the companies that owned websites we saw in the server’s databases to inform them of the risk to their users.
These ethics also mean we carry a responsibility to the public. Internet users must be aware of a data leak that exposes so much sensitive data, in case it affects them.
The purpose of this web mapping project is to help make the internet safer for all users. We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach from another group of niche dating apps, compromising 100,000s of people across the globe. We also revealed how a group of free VPNs exposed the internet activity of over 20 million users worldwide. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor any time, from anywhere, without compromising your privacy.
[Publication date: 13.09.2020]


