Report: Tobacco Promotional Campaign Exposes Romanian User Data
vpnMentor's research team recently discovered a data breach in a Romanian web platform owned by the international tobacco company British American Tobacco (BAT).
BAT is based in the United Kingdom. It is one of the world's largest manufacturers of tobacco and nicotine products.
Led by internet privacy researchers Noam Rotem and Ran Locar, our team found the data breach on an unsecured server connected to the web platform YOUniverse.ro. The web platform is part of a BAT Romania promotional campaign targeting adult smokers.
Through the platform, Romanian residents can win tickets to parties and events featuring well-known local and international performers.
Romanian law prohibits most kinds of tobacco advertising. However, the law permits certain types of promotional campaigns and event sponsorships that exclusively target existing smokers over the age of 18.
The data breach involves sensitive personally identifiable information (PII) of users.
Even more worrying is that our team discovered that the unsecured server has already been compromised by ransomware.
Despite multiple attempts by our team to disclose the breach, the database remained open and unsecured for over two months. Starting on September 22nd, we repeatedly tried to contact the company (the local branch as well as the global company), the server's hosting company, Romania's National Authority for Consumer Protection (ANPC), and the certification authority (CA). The only party we heard back from was the CA. We also contacted several Romanian journalists asking for help getting in touch with the company, but we have yet to receive a reply.
As of November 27th the database was finally closed, but nobody ever replied to us.
Example of Entries in the Database
The breach was discovered on an unsecured Elasticsearch server located in Ireland. The leaked database involves close to 352 GB of data.
Ransomware Attack
Whenever our research team finds a vulnerability in a server, our hope is that no malicious actor found the vulnerability first.
Unfortunately, that is exactly what happened here. By the time our research team discovered the data breach, the server had already been compromised by ransomware.
We found 53 indices on the server, but nearly all of them were empty. It is likely that these indices were created by the hackers responsible for the ransomware attack.
The server also contained a readme file with a ransom request:
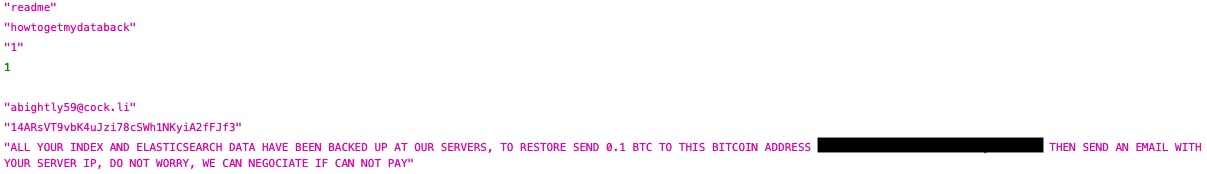
Based on the readme file, it seems that a hacker or group of hackers are threatening to delete the data from the server if their demands aren't met. The hackers are demanding a Bitcoin payment in exchange for the data.
Daily Logs
Even after being tampered with, the server still contained some meaningful data. We could view daily logs from the past seven days, each stored in a separate index.
The logs seem to be records of http communications through the YOUniverse web platform.
Examples of personal details we could view include:
- full name
- phone number
- date of birth
- gender
- source IP
- cigarette and tobacco product preferences
There are also internal values that could possibly contain more sensitive information. The meaning of some of the internal data was unclear.
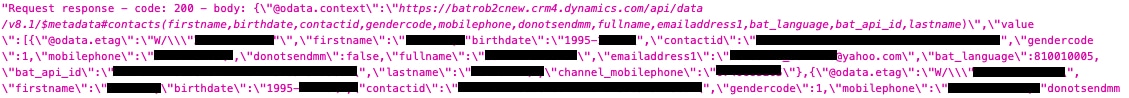
Some of the entries included messages written in Romanian. They appear to be queries submitted by users, who may be customers or affiliates.
For example, some of the messages ask for assistance and describe problems with prizes and rewards codes.
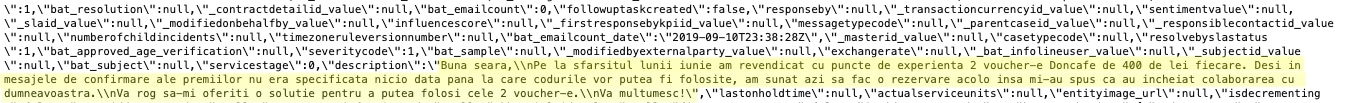
In English, the message reads:
"Good evening, At the end of June I used experience points to claim 2 Doncafe vouchers of 400 lei each. The confirmation messages for prizes did not specify a date when the codes could be used, but when I called today to make a reservation there, they told me they had concluded the collaboration with you. Please provide me with a solution to use the 2 vouchers. Thank you!"
The database also contained some metadata related to outgoing emails that failed to reach the recipient. These entries only contained metadata, not the actual message content of the emails.
We could view the following information within the email metadata:
- intended destination email address of the user
- email subject
- internal user ID
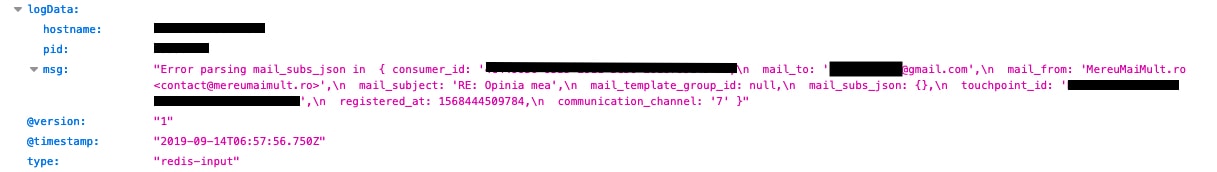
We could also view the sender's email address. The sender's email domain, MereuMaiMult, is associated with BAT Romania. Mereu mai mult is a Romanian phrase that roughly translates to "always more." It is part of the same promotional campaign as YOUniverse.
More Information May Be Exposed
A lot of data may have been missing from the server due to the ransomware attack, so we can't be sure what other information may be compromised.
To get an idea of what kind of data might have been leaked, we looked at the privacy policy that covers all of the web platforms for the BAT Romania promotional campaign. These include YOUniverse.ro, the YOUniverse mobile application, experiencemore.ro, mereumaimult.ro, preprietenie.ro, and theunseen.ro.
We also discovered login credentials to a Microsoft Dynamic CRM system, including unencrypted passwords. Unfortunately, this means there might be even more data exposed. For ethical reasons, we didn't use the login credentials, so we don't know what information is accessible through the system.
According to the privacy statement, the company collects and uses the following information when users register for any of its platforms:
- first and last name
- date of birth
- phone number
- email address
- place of residence
- brand and product preferences, including favorite tobacco
In order to sign up for the platform, users must also enter a code that can only be obtained by purchasing a pack of cigarettes.
This code is used to comply with Romanian law. The company is required to verify that all users are active smokers before they can participate in the promotional activities.
In addition, the privacy statement says that if you win a prize worth over a certain amount, the company must request your CNP for the declaration and payment of income tax. That is concerning because CNP refers to a Romanian national identity card number.
We didn't find evidence that users' CNP numbers were exposed, but we were only able to view the daily logs. It is possible that users' national identity numbers were previously exposed in the ransomware attack.
Data Breach Impact
It is difficult to estimate the number of people who could be impacted by this data breach.
Due to the size of the database and ethical boundaries that prevent us from digging too deeply into personal data, we can't be sure how many users may be affected.
The server contains logs for the previous seven days. Some of the daily logs contain more than 60 million entries, and some entries contain multiple sets of user data. On the other hand, some entries contain null or duplicate data.
It is possible that a large number of users have had their privacy compromised by this data breach.
Scams and Phishing Attacks
The data breach exposed contact information for a large number of users. Leaked emails and phone numbers put people at risk of phishing attacks and scams.
Malicious parties could use other personal details from the data breach to create tailored phishing attacks that target individual users.
Phishing attacks can take the form of emails that seem legitimate. In reality, these emails could be designed to infect the recipients with malware or trick people into exposing sensitive details.
Users could also be at risk of becoming victims of text message and phone scams. In extreme cases, hackers could even trick phone service providers into helping them hijack users' cell phone numbers.
Successful phishing attacks and scams that give hackers access to additional information or personal accounts could even lead to identity theft.
Competitors and Advertisers
Another issue to consider is the consequences of the data breach for BAT Romania and its competitors. Competitors may now have access to BAT Romania customer details, including PII and tobacco preferences.
This information could help competitors to effectively target active smokers. This could provide a big benefit to BAT Romania's competition.
Third-party advertisers could also benefit from having access to the leaked user data. The information could be used to create highly effective targeted ad campaigns.
Privacy Concerns for Smokers
The data breach compromises users' privacy in another potentially harmful way.
In order to participate in the platform, users are required to prove that they are current smokers by providing a code that can be found on a pack of cigarettes.
The data breach exposed the names of current smokers, who may not want their smoking habits exposed to the world. This could even have serious financial consequences for users. For example, insurance companies often have different rates for smokers.
If someone claims not to be a smoker but the insurance company finds that person's name in the leaked database, the user could be charged a higher rate.
Consequences of Ransomware
In truth, the consequences of the data breach could potentially be far more significant than they initially appear. Regrettably, by the time our research team discovered the vulnerability, the unsecured server had already fallen prey to ransomware.
Because the database has already been tampered with, the real size and severity fo the data breach's impact are unknown. Even if the ransom request is paid, there is no way to truly get back the leaked information.
The hackers might restore any missing data, but the hackers can easily keep a copy of sensitive user and company data.
Another concern is that other companies' servers may be affected. When we ran a Google search with keywords from the ransom message, we found multiple examples of other servers that experienced the exact same ransom attack, with the same message word-for-word.
This could mean that the data was already leaked and is now in the hands of a criminal organization.
Advice from the Experts
The ransomware attack that we discovered as part of this data breach is a perfect example of the risks of not securing your servers.
The data breach could have been prevented with some basic security measures. At the very least, you should always keep in mind the following security practices:
- Secure your servers
- Implement appropriate access rules
- Require authentication to access all systems
For a more in-depth guide on how to protect your business, check out our article on how to secure your website and online database from hackers.
How and Why We Discovered the Breach
Led by security experts Ran and Noam, the vpnMentor research team discovered this breach as part of our large-scale web mapping project.
Our research team scans ports to find known IP blocks. The team then searches for vulnerabilities in the system that would indicate an open database.
Once a data breach is found, our team links the database back to the owner. We then contact the owner, inform them of the vulnerability, and suggest ways that the owner can make their system more secure.
As ethical hackers and researchers, we never sell, store, or expose the information we encounter.
Our goal is to improve the overall safety and security of the internet for everyone.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data.
We recently discovered a huge data breach in Ecuador that affected millions of individuals. We also revealed a massive fraud network targeting Groupon and online ticket vendors.

