Report: Millions of Americans at Risk After Huge Data and SMS Leak
Introduction
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a breached database belonging to the American communications company, TrueDialog.
TrueDialog provides SMS texting solutions to companies in the USA and the database in question was linked to many aspects of their business. This was a huge discovery, with a massive amount of private data exposed, including tens of millions of SMS text messages.
Aside from private text messages, our team discovered millions of account usernames and passwords, PII data of TrueDialog users and their customers, and much more.
By not securing their database properly, TrueDialog compromised the security and privacy of millions of people across the USA.
TrueDialog Company Profile
TrueDialog is based in Austin, Texas USA, and has been around for more than 10 years. It specializes in creating SMS solutions for large and small businesses. There are several different SMS programs including mass text messaging, marketing SMS options, urgent alerts, an Education SMS solution, and more.
Currently, TrueDialog works with over 990 cell phone operators and reaches more than 5 billion subscribers around the world.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But this is really a rarity, typically it takes several days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and what’s at stake takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
In this case, it was quite easy to identify TrueDalog as the database owner. Their host ID “api.truedialog.com” was found throughout. However, it was also clear that this was a huge data breach, compromising the privacy and security of tens of millions of US citizens across the country.
Once the full extent of what had been exposed in TrueDialog’s database was clear, we contacted the company. We disclosed our findings and offered our expertise in helping them close the data leak and ensure nobody was exposed to risk.
The database has since been closed but TrueDialog never replied to us.
- Date discovered: 26/11/19
- Date vendors contacted: 28/11/19
- Date of action: 29/11/19
Overview of the Database
The TrueDialog database is hosted by Microsoft Azure and runs on the Oracle Marketing Cloud in the USA. When we last looked at the database it included 604 GB of data. This included nearly 1 billion entries of highly sensitive data, which we’ll detail below.
Example of Exposed Data
It’s difficult to put the size of this data leak into context. Tens of millions of people were potentially exposed in a number of ways. It’s rare for one database to contain such a huge volume of information that’s also incredibly varied.
The database contained entries that were related to many aspects of TrueDialog’s business model. The company itself was exposed, along with its client base, and the customers of those clients.
The information contained in this database could have been used in myriad ways against the people whose information was exposed.
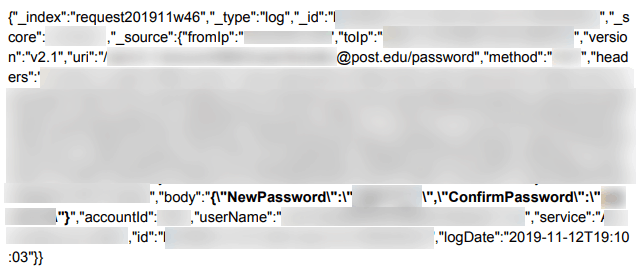
TrueDialog Account Logins
Millions of email addresses, usernames, cleartext passwords, and base64 encoded passwords (which are easy to decrypt) were easily accessible within the database.
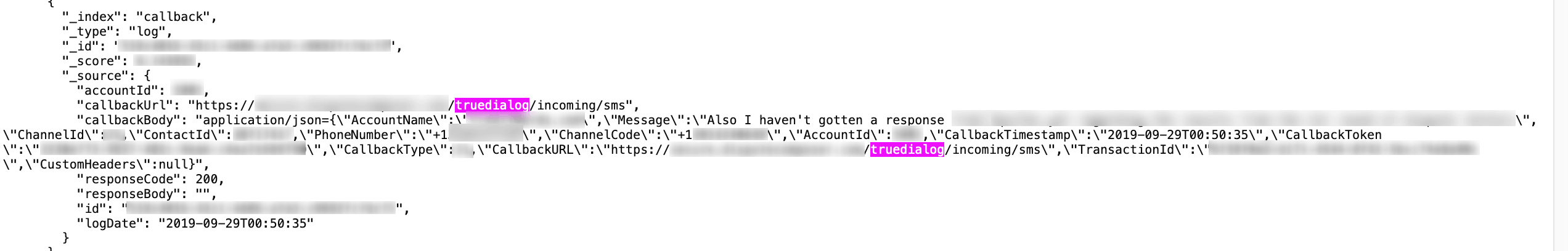
SMS Messages sent via TrueDialog
We were able to find tens of millions of entries from messages sent via TrueDialog and conversations hosted on the platform. The sensitive data contained in these SMS messages included, but was not limited to:
- Full Names of recipients, TrueDialog account holders, & TrueDialog users
- Content of messages
- Email addresses
- Phone numbers of recipients and users
- Dates and times messages were sent
- Status indicators on messages sent, like Read receipts, replies, etc.
- TrueDialog account details
The data exposed was a mix of TrueDialog account holders, users, and tens of millions of American citizens.
Account User Details
There were hundreds of thousands of entries with details about users, including full names, phone numbers, addresses, emails and more.
There was also some more detailed user information that was found. However, due to problems with the search functionality of the database, it was difficult to estimate the exact amount of these entries.
Technical logs
These logs revealed important details as to how the database is structured and managed. For example, there were hundreds of thousands of entries that documented the communication between different phone numbers linked to TrueDialogs marketing platform, Eloqua by Oracle.
We also found in the database logs of internal system errors as well as many http requests and responses, which means that whoever found it could see the site's traffic. This could by itself had exposed vulnerabilities.
Data Breach Impact
The impact of this data leak can have a lasting impression for tens of millions of users. The available information can be sold to both marketers and spammers.
For TrueDialog
There is also a significant impact for TrueDialog themselves, not including how this will negatively affect their reputation.
Their competitors could have gotten a look into their backend and seen how the company is run from within. This would have given them a way to copy, or improve upon, the business model that has brought TrueDialog success. And now that TrueDialog failed at keeping its customer database safe, its competitors can also take advantage of the bad publicity the brand is going to receive, and even take over their customers.
Also, with the logs of internal system errors, ill-intentioned hackers could find vulnerabilities in TrueDialog's system and exploit them.
For Companies Using TrueDialog
Account Takeover
The account credentials were not only left unprotected but in cleartext as well. This means that anyone who accessed the database would be able to log in to the company account, change the password, and do an incredible amount of damage.
Corporate Espionage
This is another fallout of the unencrypted message system that TrueDialog uses. It would be easy for a corporate spy to read confidential messages that were sent by a rival company. That data could include marketing campaigns, roll out dates for a new product, new product designs or specs and much more.
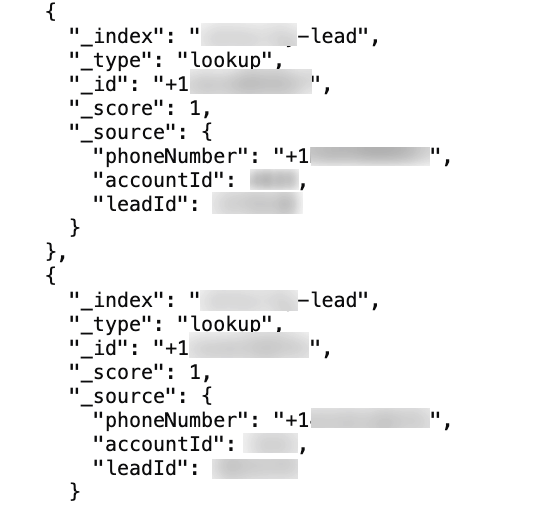
Loss of income, incl. Losing leads they buy
This leak also exposed records regarding sales leads for potential customers of TrueDialog users. Users are buying leads from external parties and if these leads came to leak, they could lose a lot of money.
For Companies’ Customers & Students
Identity theft and Fraud
A scammer could use the private details that were exposed in the messages, as well as the full names, emails and phone numbers exposed in it for a variety of fraudulent schemes.
Phishing and Scams (phone & online)
The vast amount of contact details itself is a huge asset for spammers. Moreover, exposed personal details can prove very valuable in order to target individuals to respond to spam and phishing.
Blackmail
With all the message content exposed in cleartext, scammers will have plenty of ammunition for blackmail. Scammers can use any of the personal information that is sent by either customer, or students in the Education programs, and use it to extort them.
Advice from the Experts
TrueDialog could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For TrueDialog Users
If you’re a customer of TrueDialog and concerned about how this breach specifically might impact you, or data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
During a comprehensive web mapping endeavor, the vpnMentor research team identified a breach in TrueDialog's database. Our investigators utilize port scanning to scrutinize specific IP blocks and inspect system vulnerabilities by testing open gaps. Each of these gaps is carefully assessed for any indications of data leakage.
When they find a data breach, they use expert techniques to verify the database’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this database because it was completely unsecured and unencrypted.
The company uses an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing the database schemata.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. This is especially true when the companies data breach contains such private information.
However, these ethics also mean we carry a responsibility to the public. TrueDialog users must be aware of a data breach that impacts them also.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
In the past, we’ve discovered a huge data breach exposing the data of millions of Ecuadorean citizens. We also revealed that a breach in Biostar 2 compromised the biometric data of over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.