ENVEIL — Never Decrypt Your Data (Always Keep Encrypting)
- I would normally start by asking you to tell me about your background and experience, but I am guessing that since before founding ENVEIL you spent 12 years as a researcher at the NSA (National Security Agency) you are not going to be able to tell me very much.
- What was it like to move from a government research lab to a commercial startup?
- How exactly do you take a technology developed inside the NSA and commercialize it for yourself?
- Before getting into the specifics of ENVEIL, can you share your top three enterprise security tips?
- Your tagline – or mission statement – is “Never Decrypt.” How can applications access their data when it is encrypted? Does using ENVEIL require modifying an application’s source code?
- How do you define your target market?
- What does your pricing model look like?
- How many active customers do you have today? Where are they mainly located?
- Whom do you see as your main competitors?
- What are your future plans for ENVEIL?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
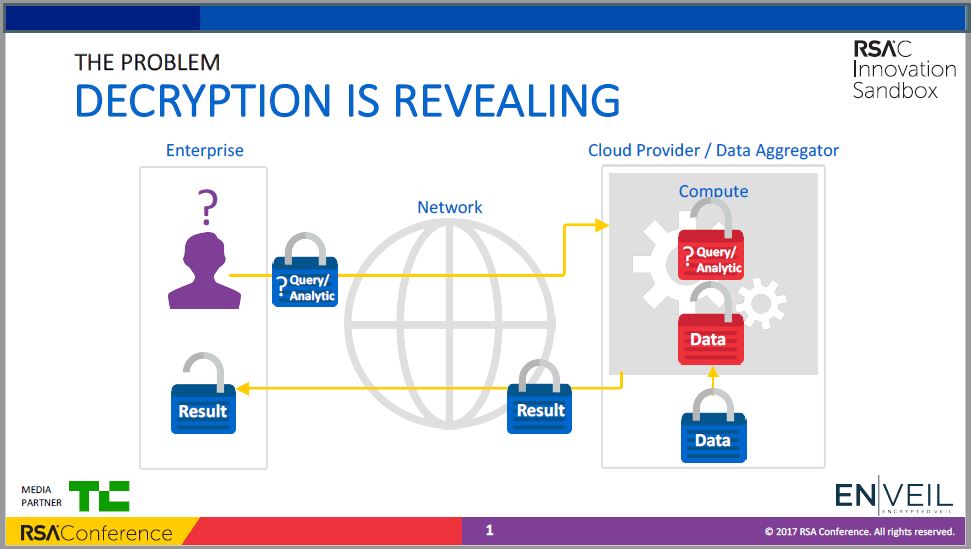
It should not come as any surprise that the mantra repeated by Dr. Ellison Anne Williams, the CEO and founder of ENVEIL is “Encrypt Your Data.” As you will see, she actually goes further with her company’s tagline, which is “Never Decrypt.” It is not surprising because before establishing ENVEIL, Ellison spent over a decade as a Senior Researcher at the U.S. NSA (National Security Agency). It was there that the core technology of the ENVEIL platform was developed and field-tested.
I would normally start by asking you to tell me about your background and experience, but I am guessing that since before founding ENVEIL you spent 12 years as a researcher at the NSA (National Security Agency) you are not going to be able to tell me very much.
That is pretty much correct [Laughs]. I joined the NSA after graduate school. Before hiring me, they would not tell me what I would be working on, but promised me that it would be “really cool.”
Let’s just say that I worked on various projects dealing with what we now call “Big Data.”
What was it like to move from a government research lab to a commercial startup?
I absolutely love it. I always wanted to go out on my own. Even while I was working inside the NSA, I was always starting new things. Now, however, I get to work in an environment that is smaller and more agile.
How exactly do you take a technology developed inside the NSA and commercialize it for yourself?
The core technology of ENVEIL was developed and used inside the NSA. However, I was able to take portions of that technology out of the NSA to be commercialized. The NSA actually has a formal process in place for this, called the Technology Transfer Program. It is a long and not easy process, but it is doable if you are tenacious enough. I was also fortunate to have several people who worked for me at the NSA join me at ENVEIL.
Before getting into the specifics of ENVEIL, can you share your top three enterprise security tips?
- Encrypt Your Data.
- Encrypt Your Data.
- Encrypt Your Data.
People and organizations are simply not employing basic security practices by securing their sensitive data.
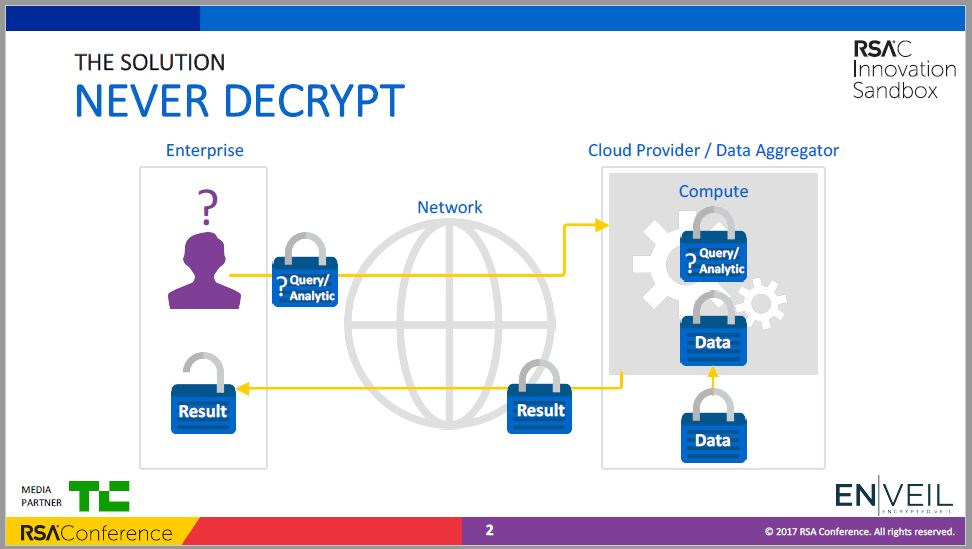
Your tagline – or mission statement – is “Never Decrypt.” How can applications access their data when it is encrypted? Does using ENVEIL require modifying an application’s source code?
Employing ENVEIL is not at all intrusive to your existing environment and applications. That means that it does not require any charges to your system architecture or application code.
The way it works is that we are a proxy layer on top of your data storage. There is a client application that is deployed either on each device or as a centralized gateway. This app communicates with a server application that is deployed in the environment of the data storage. The server app is granted access to whatever data source it is protecting.
To be a little more technical, our client application is a drop-in replacement for the JDBC (Java Database Connectivity) API and for standard REST (Representational State Transfer) APIs.
The critical point is that no data is ever decrypted while being processed in the cloud/public space. Our framework allows you to operate on data (query/analytics) without ever revealing the content of the interaction, the results, or the data itself. This is because we use homomorphic encryption, which allows us to perform computations on encrypted data as if they were unencrypted.
How do you define your target market?
The ENVEIL framework is appropriate for anyone that is security conscious and concerned about their data, regardless of whether it is located on-premises or remotely. Our technology is valuable across all verticals, although to date we have received the most interest from:
- Financial Services
- Healthcare
- Data Aggregators
What does your pricing model look like?
As with most enterprise software, our pricing model is a based on a yearly subscription. Right now, we offer one variety, which we call “All You Can Eat” – meaning that you get unlimited users, unlimited transactions, and unlimited data transfer.
How many active customers do you have today? Where are they mainly located?
Although the technology itself has been in use for many years (inside the NSA), the company itself is still very young. We are currently working with several big banks and large healthcare companies located in the U.S.
Whom do you see as your main competitors?
We do not have any direct technical competitors – there is no one doing what we are doing.
Of course, we do still have competition, in the form of people continuing to work the way they always have or adopting various workarounds to try to achieve the same goals.
What are your future plans for ENVEIL?
Our overarching objective is to foster a heightened understanding of the imperative need for data encryption across all stages. This includes advocating for the protection of data at rest, data in transit, and data in process, underscoring the importance of safeguarding information at every possible juncture.
More specifically, we are going to strive to grow as a company by focusing on two main areas:
- Continued enhancement and extension of our core capabilities.
- Additional, deeper, and richer secure, encrypted analytics.
How many employees do you have today? Where are they located?
We are currently seven employees, all located outside of Washington, D.C.
How many hours a day do you normally work? What do you like to do when you are not working?
I would have to say that I work 27 hours a day… [Grin]
When I am not working, I love to cook and bake – I am a serious foodie.